Welcome to another week of Triage Thursday update news! We’ve got quite a list of changes for you this week, with multiple configuration extractor updates and detections for a couple of new families:
- New configuration extractor for RustyBuer
- Added initial Mimikatz signatures
- Updated BazarLoader detections
- Initial BlackMatter ransomware detection
- New BlackNetRAT configuration extractor
- Updated Danabot configuration extractor
- Updated SnakeKeylogger detection
- Added family detection for Shurk Stealer
In other news we are still looking for a Go developer to join to Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
As usual if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
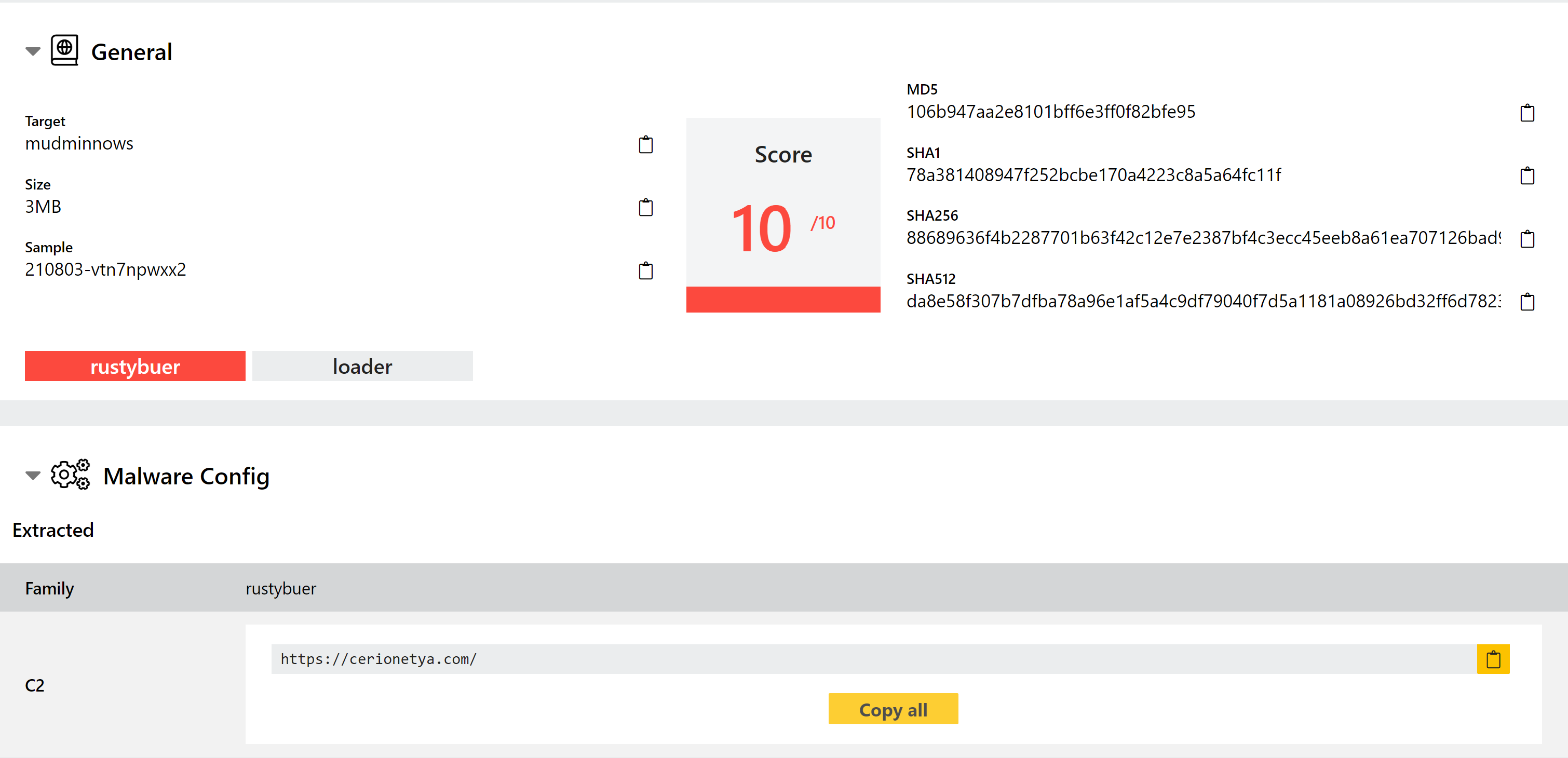
New RustyBuer Configuration Extractor
Buer is a malware loader framework which has been active in the wild since late 2019. It is sold through forums as an off-the-shelf downloader and installer for other payloads. The initial version was written in C, but in May 2021 Proofpoint reported the discovery of a new variant of the family developed using Rust instead. This rewrite was likely just intended to switch up the code base and evade existing detections, although Rust also comes with potential performance and maintainability improvements too.
Due to it being available as malware-as-a-service, both RustyBuer and its C-based predecessor have been seen in use by a very wide range of families, including Trickbot, BazarBackdoor, Ryuk ransomware, and more recently even CobaltStrike beacons.
The family is successful for more than just its availability, with an extensive feature set including VM checks, locale restrictions, and robust C2 communications.
We have featured Buer on this blog a couple of times in the past, when we initially added signatures and again when a tweak to the payload required a signature update. Today we’ve continued our support for it by adding detection for the RustyBuer variant and implementing a full configuration extractor for it.
Analyses:
Added Mimikatz Detection
Mimikatz is an open-source program for stealing Windows credentials and escalating privileges on a system. Initially created as a proof of concept of flaws in the security of Windows account logins, it has since become an extremely popular tool among cybercriminals. This mainly comes down to 2 reasons - first that the application is extremely effective and stable, but also that its status as a common tool with security/penetration testers it often slips under the radar where custom implementations would not.
This week we’ve added some initial detections for Mimikatz payloads, so that they will be appropriately tagged with the family name in future. As an open source project there are many different versions floating around in the wild, so we’ll likely be continuing to expand support for the family in the weeks to come.
For reference, some examples are available below.
Analyses:
Updated BazarLoader Detections
Since the end of Emotet, the Bazar family has rapidly become one of the most widely used and successful threats of 2021. Initially starting out as a simple loader and backdoor combination, it has since branched out to now include a large number of different versions and rewrites, with various iterations of the loader module now being heavily used by other families to distribute their own malware. A recent campaign - dubbed BazarCall - has seen the family being used in large spam phonecall campaigns using various social engineering lures to get people to install the loader on their machines.
The family is constantly changing and evolving, and although our detections continue to be quite reliable for the backdoor elements the changes have piled up in the loader and we recently began noticing that many analyses were no longer properly detected. We have reviewed available samples from Triage and the community, and made some much needed updates to improve detection again.
There are still a couple of variants in our backlog, so expect more improvements here in the coming days.
Analyses:
Added Initial BlackMatter Ransomware Detection
BlackMatter is a new ransomware which popped up in July 2021, in the aftermath of the successful attack against the Colonial Pipeline in the USA.
Advertised through cybercrime forums, the ransomware group claim to be incorporating significant elements of the Darkside, Lockbit and REvil families into their new malware and are clearly trying to align themselves as the successor to these families. Whether there is actually a significant overlap in the teams for these projects or if they are just attempting to use the names to gain attention is not currently clear.
Interestingly unlike many ransomware operators the BlackMatter team are not, at least currently, directly selling access to the malware. Instead they are recruiting cybercriminals who already have access to compromised corporate networks which the ransomware team will seemingly then carry out a targeted attack against.
They also have very clear rules on which organisation types they will and will not target - likely a precaution triggered by the recent disruption caused by attacks like the Colonial Pipeline. Whether or not they adhere to this limitations only time will tell.
Analyses:
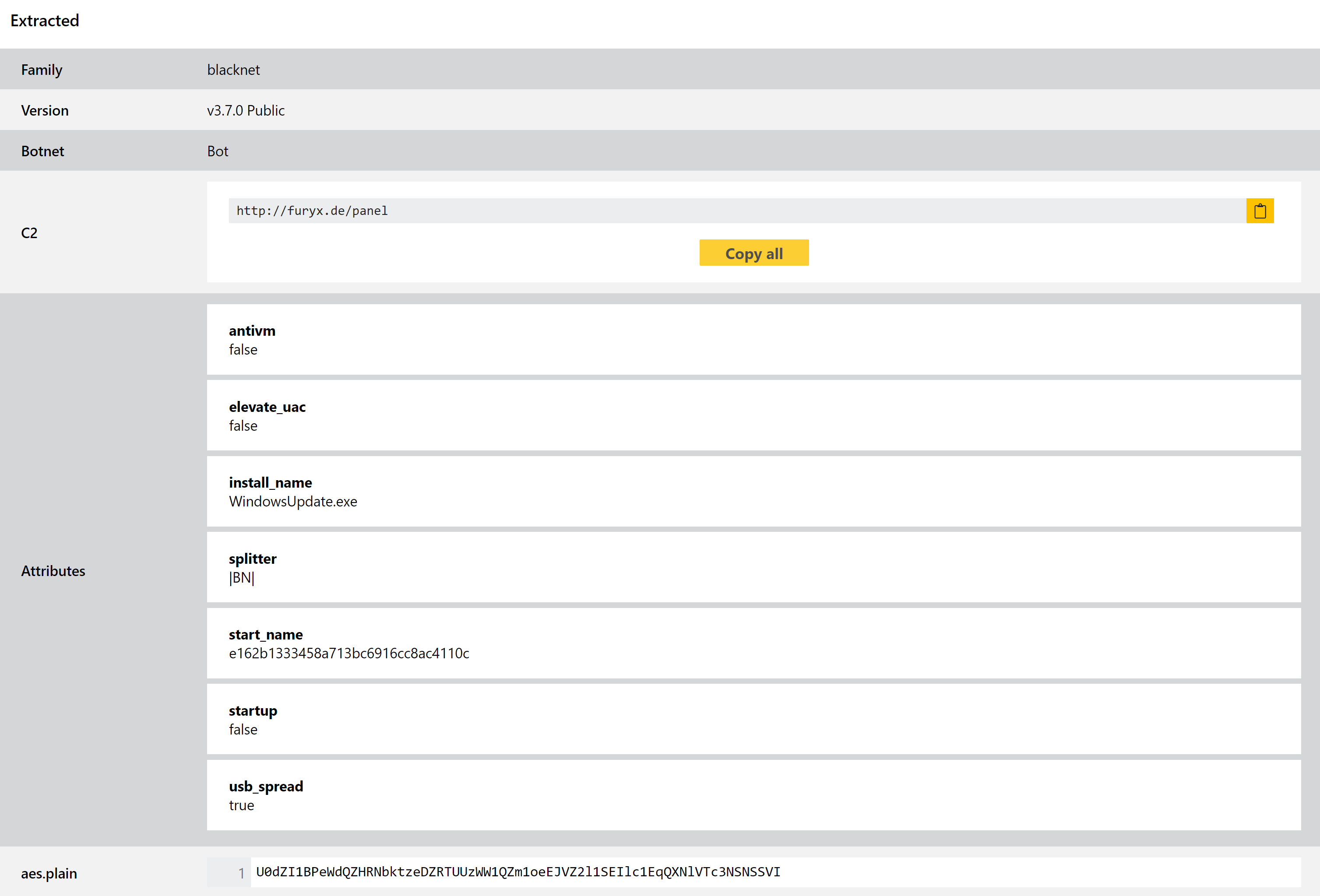
New BlackNetRAT Configuration Extractor
BlackNet is an open-source RAT and stealer which first appeared in early 2020. It has been seen mainly exploiting COVID-19 related lures to infect victims, including a fake “Corona Antivirus” program which - ludicrously - claimed to protect those who installed it from the actual Coronavirus.
The malware has a good range of functionality including stealing web browser data, logging keystrokes, capturing screenshots, and dumping cryptocurrency wallets. It can also be used to carry out DDoS attacks. As the name suggests the main payload is written in VB.NET, and it comes with a control panel created in PHP.
We have implemented a new configuration extractor for the family which can dump out C2 information, version numbers, and a range of settings defined at compile time.
Analyses:
Updated Danabot Configuration Extractor
Danabot is a common banking trojan/stealer which was initially observed by Proofpoint targeting users in Australia in mid-2018.
The family has continued to be active since then, with new samples and variants still regularly appearing in the wild. At the start of 2021 a new version was released after a period of lower activity which appears to have increased use of the family again. The malware itself is modular including functions for browser injections and network sniffing, stealing local browser credentials, and remote access capability.
We have support detection and configuration extraction for Danabot for some time now, but recent changes meant that this was no longer catching all versions. We have reviewed the samples and made the necessary changes to bring it back to full support.
Analysis:
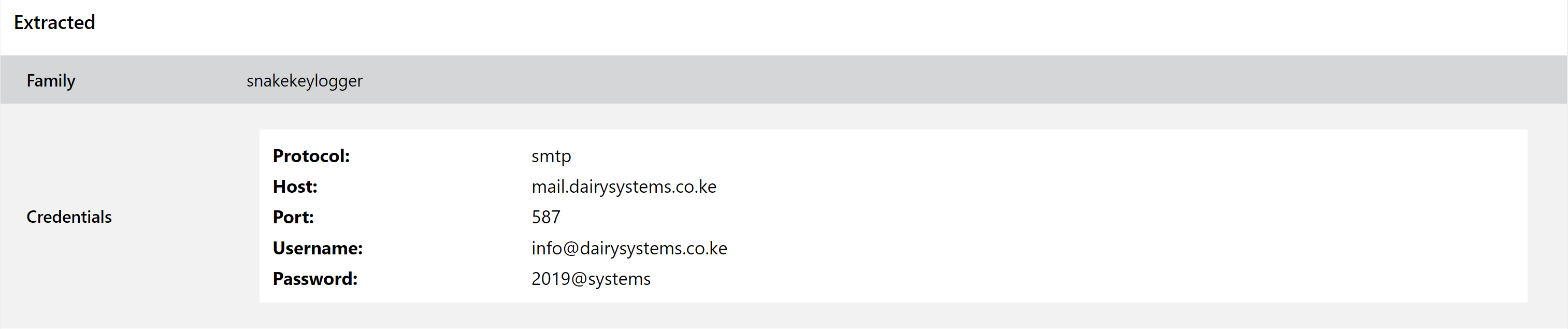
Updated SnakeKeylogger Detection
Snake is a relatively simple keylogger which is operated as malware-as-a-service, being sold through underground forums for fairly low prices. As is common now it is not solely a keylogger, also featuring functionality common to infostealers - theft of browser data, screenshot capture and clipboard interception.
Triage features behavioural detection and a full configuration extractor for SnakeKeylogger, but again some recent changes meant some samples were not being handled correctly. We have no applied changes to fix that.
Analysis:
Added Family Detection For Shurk Stealer
Shurk is a fairly basic infostealer written in C++. While not particularly complex, it is capable of stealing information such as cryptocurrency wallets, browser cookies/passwords and data from local secure messaging applications such as Telegram. The family takes its name from a hardcoded string value within the payloads examined so far.
Like a few other families Shurk is distributed by the G-Cleaner program, a fake garbage cleaner posing as something similar to CCleaner but in fact just acting as a dropper for various bits of malware. It was brought to our attention at the end of July by a tweet from @benkow_:
Analysis:
