Another week has flown by, and it’s time for a new Triage Thursday blogpost. Today we have a selection of detection updates to introduce for Windows and Linux, including adding initial support for a couple of families:
- New configuration extractor for LimeRAT
- New Socelars family support
- Static detection for Sodinokibi/REvil Linux variant
- Added detection for DarkVNC RAT
- Initial detections for GoldDragon backdoor
- New family signatures for FatalRAT
In addition to our updates, we are still looking to hire a new Go developer for the Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
As usual, you can also contact us with any feedback or suggestions about Triage or its analysis results. It’s a big world of malware out there and there can always be things we miss! If you notice anything not behaving as expected please do reach out and report it to us. You can contact us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
New LimeRAT Configuration Extractor
LimeRAT is an open-source remote administration tool which is available on Github. It has an extensive list of supported features and is able to operate as a typical stealer, ransomware, cryptocurrency miner, or a bot for DDoS attacks etc. It also includes some anti-VM and anti-virus evasion techniques to help it remain undetected.
Although the base project hasn’t been updated since 2019, the open-source nature of the project means that a number of actors still leverage the tool - or modified variants of it - in their campaigns.
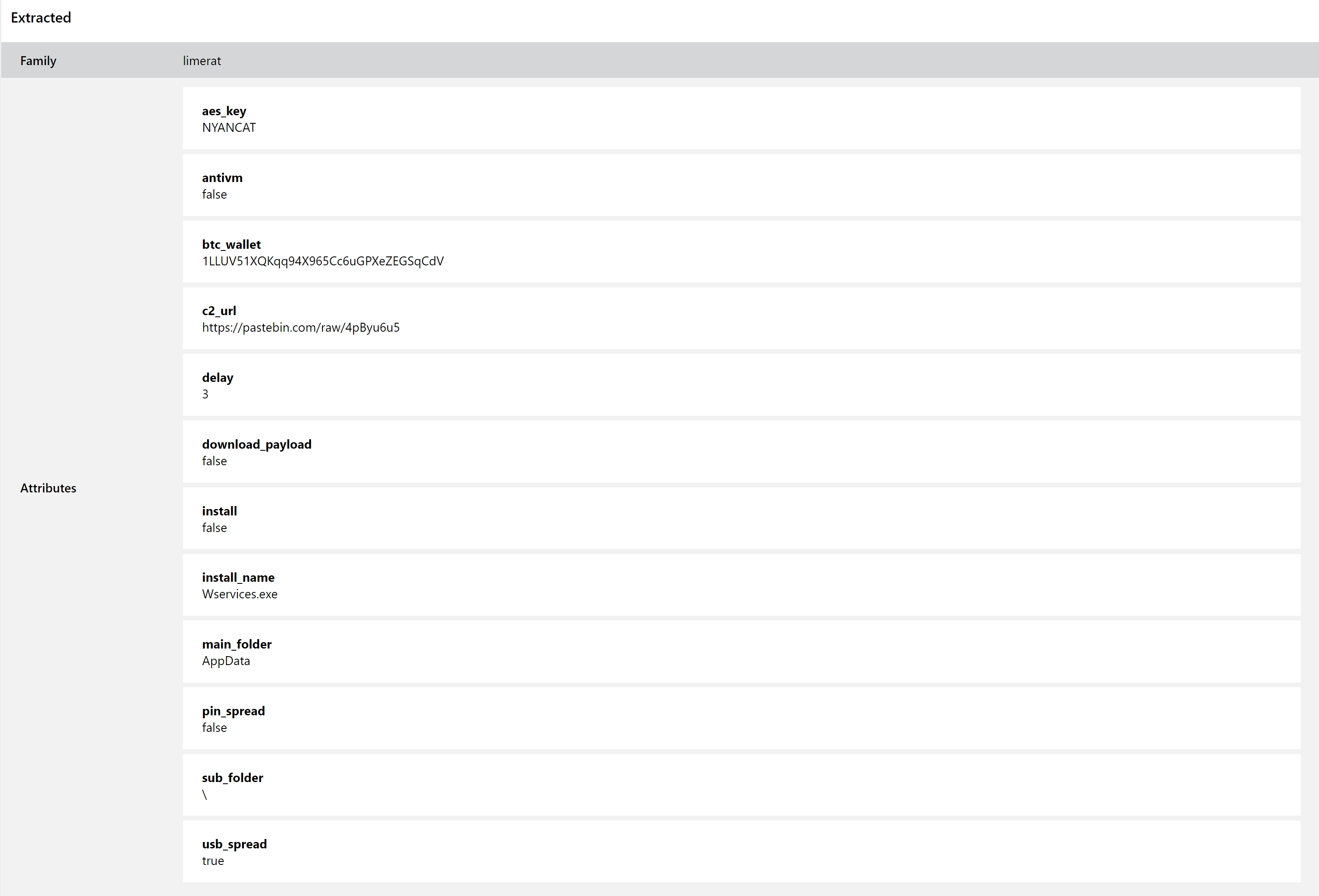
Triage has featured behavioural detection for the family for some time, but this week sees the release of a full configuration extractor. This can pull out extensive data on the samples, including C2 information, AES keys, operation settings (whether things like spreading via USB, downloading additional payloads, etc. are enabled or not) and filepaths. We are carrying out reprocessing of the family and you can find some recent examples below.
Analyses:
New Socelars Family Support
Socelars is a stealer family which has been around since at least late 2019. It is slightly unusual in its functionality, as it doesn’t target many of the standard data sources focused on by most other stealers. Rather than going after passwords and profile data stored on disk, Socelars is more interested in cookie data with a specific focus on Facebook and Amazon.
We have observed samples of the family being uploaded to Triage regularly, so we have reviewed it and added some initial signatures to properly detect it. Some examples are provided below.
Analyses:
Static Detection for Sodinokibi Linux Variant
The Sodinokibi family likely needs no introduction. Also known as REvil, it has been a persistent and highly successful ransomware threat since it stepped into the gap left by Gandcrab’s ‘retirement’ earlier that year. It regularly hits the news for its successful infections of large organisations.
The family receives regular updates and is still very active in the wild. At the end of June a new variant of the family was reported which widens its scope to include Linux machines for the first time. Earlier this week we released a detection update to catch these samples and ensure they are correctly identified.
We’ll be continuing to keep an eye on developments from Sodinokibi, as it’s likely this is just the first iteration of their Linux support.
Analyses:
Added Detection for DarkVNC RAT
The DarkVNC family was first seen in the wild in 2017 abusing the VNC protocol to provide remote access and control of infected systems. The original release was based on the leaked source code of Cerberp, an old trojan with a history going all the way back to 2019, and was mostly seen being distributed by the exploit kits that were common at the time.
The family was brought to our attention recently by a tweet from @malware_traffic, reporting a new sample being deployed alongside Trickbot.
We have reviewed available examples and deployed some family signatures to properly index them. Thanks to Brad at @malware_traffic for the samples.
Analyses:
Initial Detections for GoldDragon Backdoor
GoldDragon is a backdoor and loader generally attributed to the Kimsuky APT group from North Korea. Activity is mostly limited to targeting various South Korean companies and government organisations, and GoldDragon itself normally forms just one part of a much larger infection and exploitation chain.
The family is capable of automatically downloading and installing additional payloads, as well as providing direct backdoor access for the attacker if needed. Some examples were recently reported to us by one of our customers, and we have now deployed initial signatures.
Analyses:
New FatalRAT Family Signatures
FatalRAT is a new addition to the malware landscape in 2021, with initial reports popping up around late May. Alongside a set of fairly standard stealer functionality, the family includes several evasion and anti-VM techniques which can make it tricky to analyse manually. It can also act as a dropper/loader for additional modules.
We have investigated some samples uploaded to Triage recently, and today deployed signatures to detect them. An example is available below.
Analysis:
