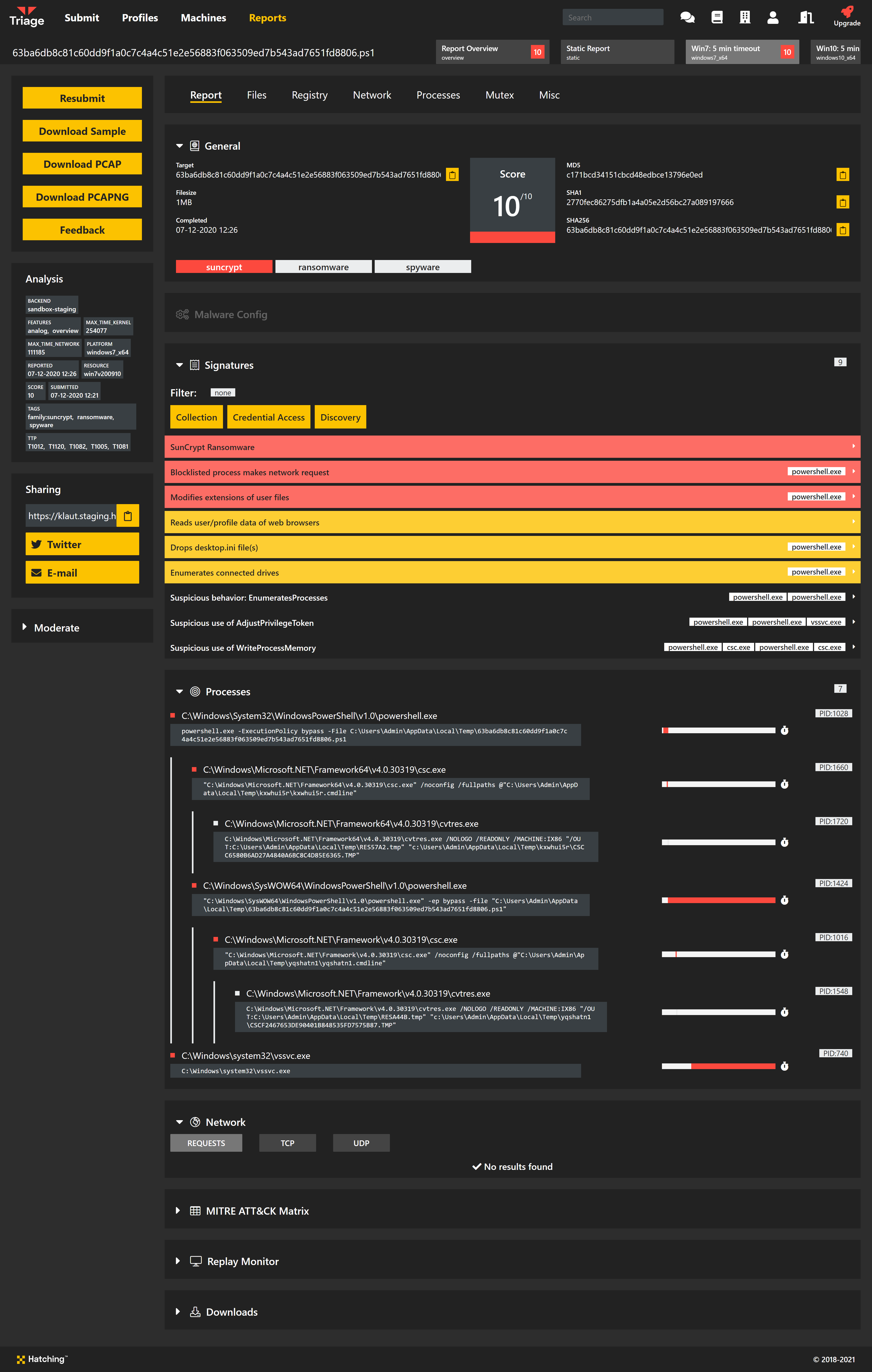
Welcome back to our Triage Thursday blog series, and another week of updates! The main things on the menu today are improvements to the Triage web interface which we hope will improve your experience using the platform and make information more accessible.
As usual we also have family updates to expand and improve detection. Read on below for more information on all of the changes:
- Directly submit dropped files from analysis reports
- DNS queries now show the source process
- Show Submitter name in Organization Samples view
- Updated Overview report section to show signature summary
- New dark mode for the web interface
- Automatic handling of anti-VM measures used by Qakbot
- Review of Gozi/Ursnif family signatures
- Emotet extractor update
- New configuration extractor for IcedID/BokBot
- Signatures for XenArmor Suite
- Family detection for Velgax RAT
- Improved handling of non-Latin characters in ransom notes
If you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Directly submit dropped files from analysis reports
A feature that has been commonly requested through feedback is the ability to submit a file dropped by a sample as a new analysis, without having to manually download and reupload the file. We’re pleased to say that this is now available on Triage - valid files which appear in the Download list of a report can be submitted with a single click.
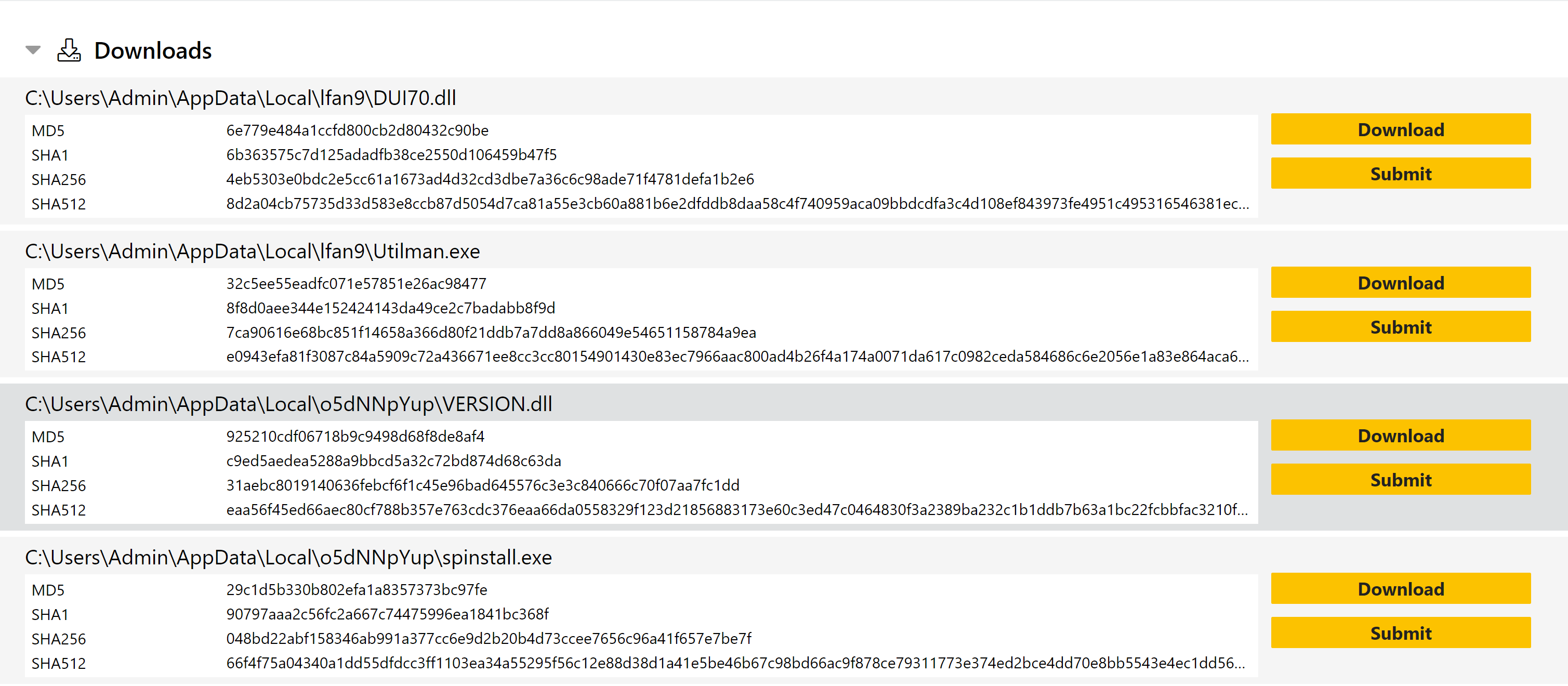
The Submit button will take you to the profile selection page where you can configure the analysis just the same as with any file upload submission.
Updated DNS view to show source process
We’ve pushed a small tweak to our Network report section, adding the name of the source process to DNS queries shown in the UI. This should help with relating activity to particular aspects of an analysis.
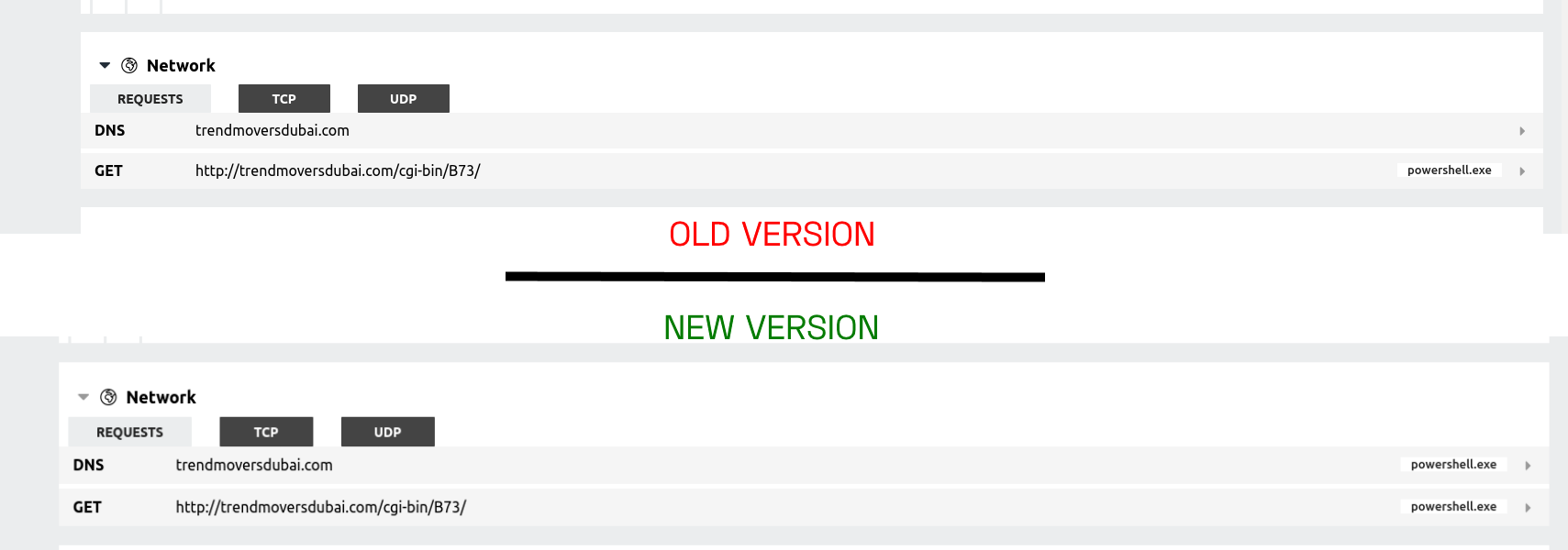
Our network section will be seeing more significant changes in the future as we look to review and improve the information made available there, so if you have any particular suggestions for this part of Triage please feel free to send them to us through the Feedback feature.
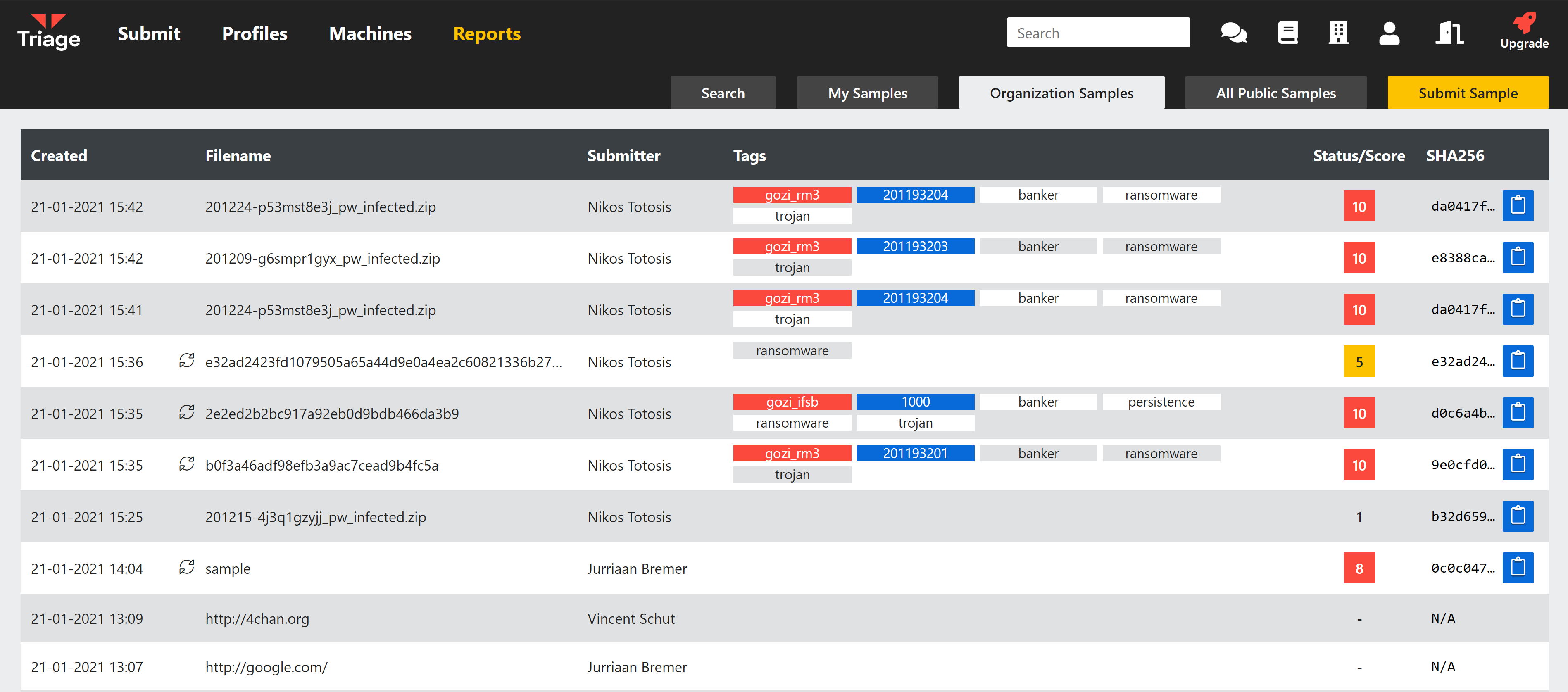
Show name of submitter in Organization view tab
Note: this is only relevant for Private Cloud users and is not available through the public tria.ge server.
For users of Private Cloud installations of Triage, Organizations can be configured to group users and provide shared access to samples owned by subsets of the registered accounts.
Based on feedback from our users, we have added a column to the Organization Samples section which shows the user that submitted the sample. Note that this is only displayed on the Organization tab, and thus is not visible to anyone not also within that group.
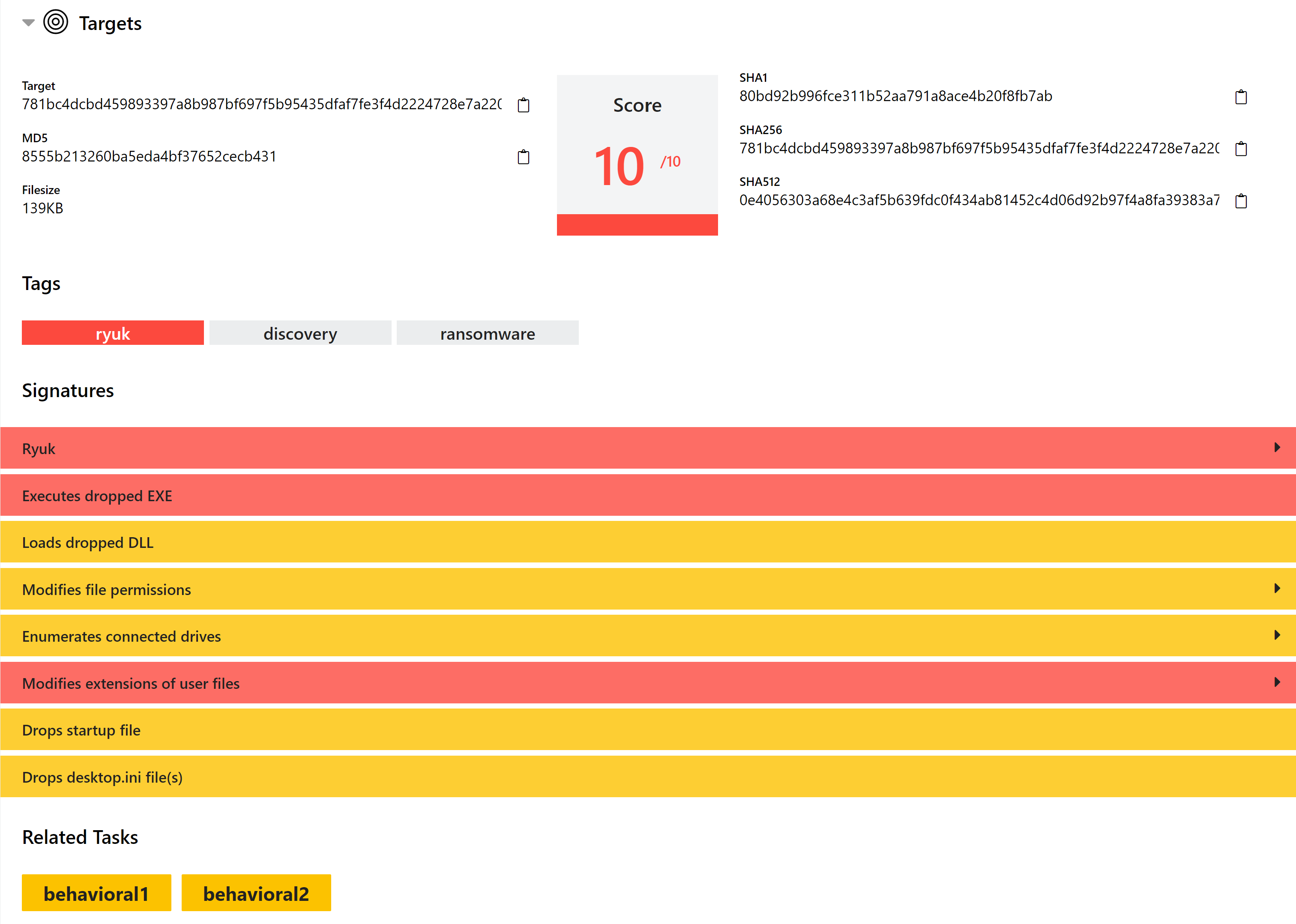
Updated Overview tab for each analysis
Back in September we added a new Overview section to analysis reports. This brought together score and verdict information from all tasks that make up an analysis to provide a quick-glance summary of findings.
With our latest update we have updated this to also include a summary of high-scoring signatures from the sub-tasks. Informational signatures will not be shown here, but these are still available on the relevant behavioural report page.
New Dark Mode for the web interface
We all know that the next question after “can it run Doom?” is “does it have dark mode?”1. Well now Triage does!
You can find the new setting on the Account page.
Automatic handling of Qakbot anti-VM techniques
Qakbot has long had issues with detection stemming from anti-VM techniques which are difficult to reliably defeat from the sandbox side. Although a simple mechanism, its checks of the sample’s filename have been tricky to circumvent in an environment where we allow users to submit with whatever file name they choose. Forcing a different filename never seemed like a practical solution due to the mismatch that would then occur between the expected system activity and how it would actually appear, potentially causing some confusion and issues with automated parsing of output.
We have now found a workaround which resolves most of these issues and allows for far more reliable detection of Qakbot in a sandbox environment. We have been improving and updating many of our dumping strategies (which dictate how memory/process dumps are taken for further analysis) over recent weeks, and as part of this we are now able to dump the Qakbot payload at an earlier stage of execution and successfully identify and extract it from there.
This should mean that in the future Qakbot detection will be far less dependant on the way in which it was submitted. As usual we’ll be monitoring the family going forward and will continue making improvements if needed.
Review of Gozi/Ursnif signatures
The Gozi/Ursnif family is quite a messy collection of variants and forks which are regularly updated. We have been carrying out a review of the signatures we have implemented over time for the family’s variants, as well as revisiting our naming conventions based on more recent reports and findings.
As such, in future the Ursnif family tag will be replaced with Gozi. This is intended to bring it more in line with the more common naming conventions used in the industry, as well as being technically more accurate for certain samples.
We have also updated the detections and the configuration extractor to be more reliable and handle more variants correctly. This is now available on tria.ge.
Updated Emotet extractor
Earlier this week Emotet was at it again, with another version appearing which got around our configuration extractors.
The change was relatively minor but was evading our Yara rules which trigger the family extractor. We quickly tweaked the rules and this ‘variant’ is now also fully supported.
We’re sure this won’t be the last time we mention Emotet in these blogposts, but we view it as a priority and will continue pushing rapid updates for future changes. Thanks to everyone who reports broken analyses like these to us - it’s a great help with getting fixes out quickly.
Analysis:
New configuration extractor for IcedId/BokBot
IcedID, also commonly known as BokBot, is a banking trojan which has been active since late 2017. It is relatively advanced, containing a wide range of functionality including:
- Anti-VM/anti-debugging measures
- Web injection/man-in-the-browsers
- Full remote access
- VNC module for live control of the infected system
IcedID has often been seen deployed by Emotet campaigns, mainly targeting financial organisations.
Triage has had signatures to identify IcedID for some, but we are now fleshing this out further with a new configuration extractor which dumps basic C2 information.
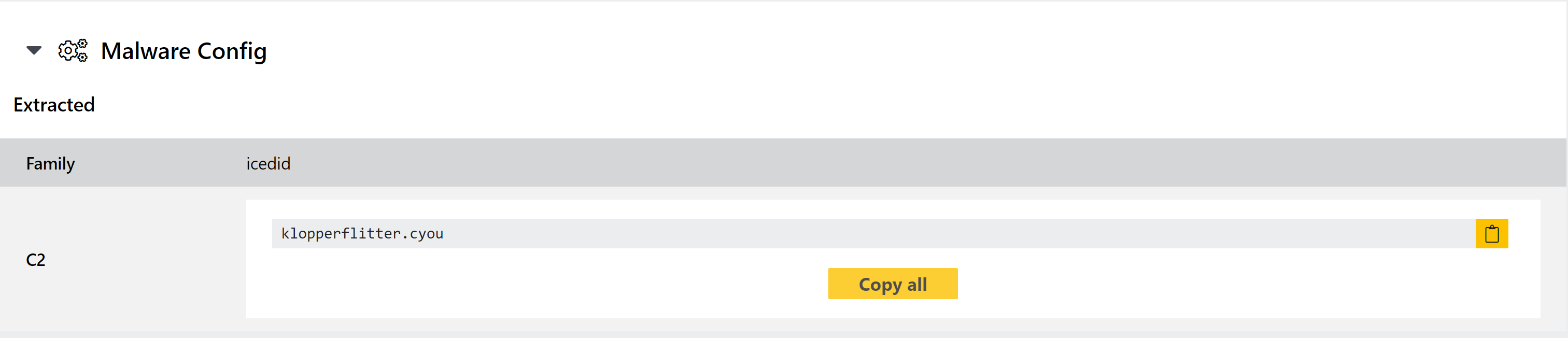
Analysis:
Signatures for XenArmor Suite usage
XenArmor is a set of legitimate utilities related to password recovery. We have recently observed them being deployed by malware such as the BitRat family as a 3rd party tool for stealing system credentials.
As such we have now added signatures to report when utilities from this suite are detected being loaded onto the VM. Although not themselves malicious it seems fair to consider their presence an indicator of compromise.
Analysis:
Family detection for Velgax RAT
Velgax is a new RAT we have observed which appears to be forked from the Quasar RAT codebase. It has been built with additional capabilities over its older brother, featuring support for extra commands once installed on a system. Rather than just classify it as Quasar, we have named it Velgax based on the mutex it creates and report it as such for clarity.
We’ll continue to keep an eye on this for further development over time.
Analysis:
Updated ransom note parsing
We recently noticed a Conti ransomware sample where the ransomnote was not being successfully extracted due to Cycrillic characters being used in place of certain Latin characters they happen to resemble. To resolve this we have added a simple ’normalisation’ process for the contents of dumped text files to help our extractor identify valid ransom notes.
Analysis:
-
We may have made this up. ↩︎
