Welcome back to Triage Thursday! We’re back to the normal format this week, with a range of new updates to introduce.
Chief among these is the release of our Phishing analysis support. You can find more details on that below.
We also have several detection updates since our last blogpost:
- Onemon agent updates
- Bazar family detection improvements
- New Campoloader/NLoader signatures
- Ginp Android trojan detection
- Updated Gozi RM3 configuration extractor
- Expanded coverage for Guloader
- New Redline stealer variant
- WSHRAT signature update
As usual if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Phishing Analysis
In our last blogpost we took a look at our plans for phishing analysis within Triage. We are pleased to announce today that the first version of this is now available on the public Triage server for all users.
This is the first iteration of phishing analysis and we will be expanding its coverage significantly in the future. The initial detections available are based around particular brands which are commonly targeted by malicious campaigns (e.g. PayPal, Amazon, Facebook etc.), but we have plans to add heuristic-based signatures which can provide more generalised coverage.
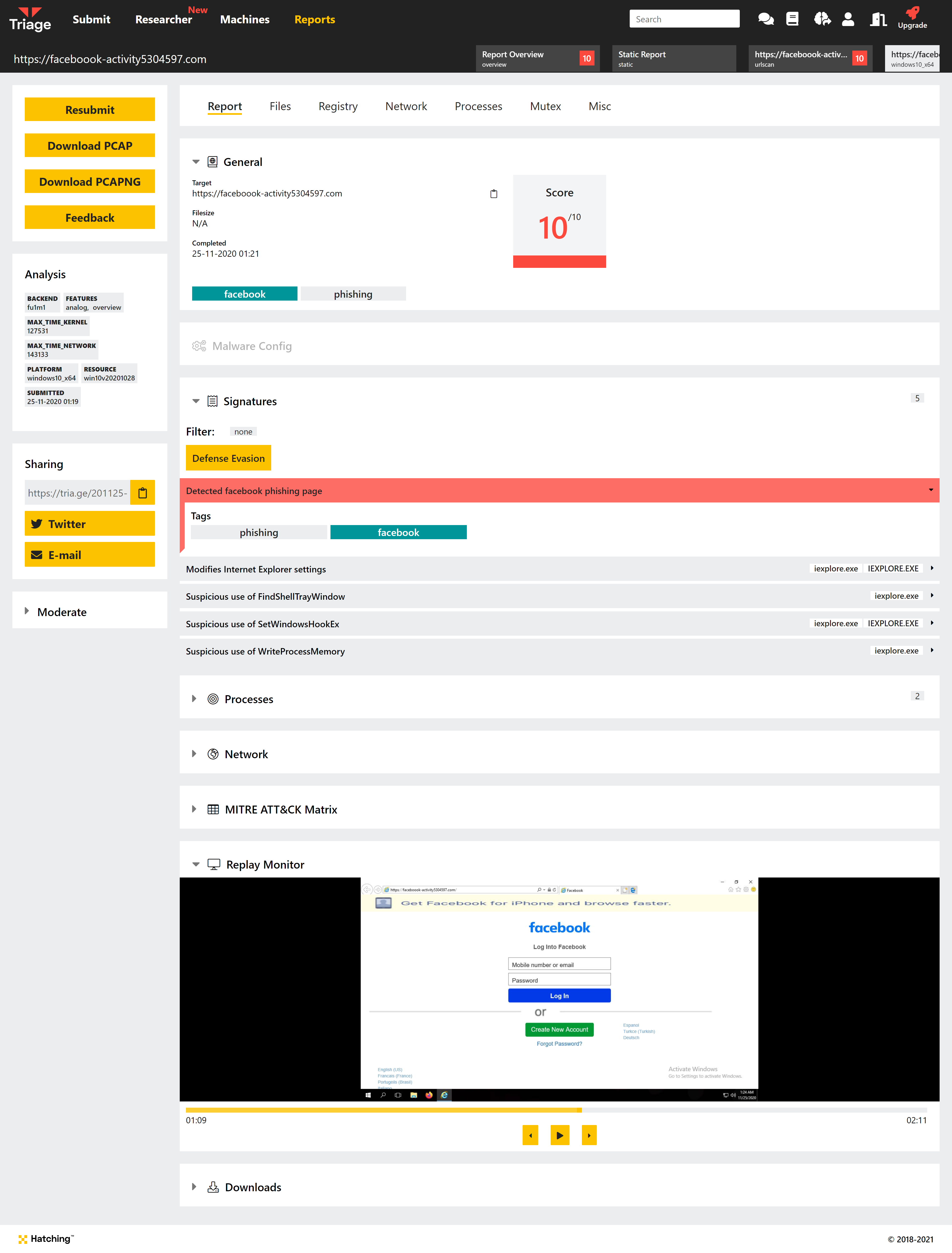
Phishing-related searches are also supported, to help filter the report list:
tags:phishing: Find all analyses which triggered a phishing-related result.brand:[name]: e.g.brand:facebook. Filter reports to find phishing analyses which target Facebook accounts.
Onemon Agent Improvements
In addition to this week’s detection updates, we have also been working on some tweaks to the kernel monitor agent itself. The largest of these changes provides Triage with the ability to dump Windows event logs during analysis, making them available for further analysis in existing toolsets/workflows. This is currently not integrated into Triage itself so the logs are inaccessible for now - we’ll be fully implementing this feature in the coming weeks.
We have also made some changes which will better support Excel maldocs, and improved a dumping strategy used by families like IcedID.
Bazar Family Update
Bazar, especially the loader variant, has somewhat exploded in popularity in recent months and this shows no sign of ending soon. We have been carrying out a detailed review of the family - loader and backdoor - and are releasing revamped detections for it in this update.
Triage has generally done a good job of identifying new BazarLoader samples where many other solutions have struggled with the changes, but even so a growing number of variants were getting by our signatures. This has now been addressed, and we’ll continue keeping an eye out for new variants.
Analyses:
CampoLoader/NLoader Detection
During our review of Bazar samples, we observed a sample on MalwareBazaar which was being tagged as Bazar but on closer inspection didn’t actually appear to be part of the family directly. It appeared to be a different, fairly generic loader.
Based on reverse engineering of the sample, we initially allocated the name NLoader due to a debug string within the sample. However based on discussion with @Cryptolaemus it appears to be more widely referred to as Campoloader, based on the C2 URL.
Although the malware itself is not a variant of BazarLoader, it is clearly related to some degree as it has so far been distributed in Bazar campaigns.
We have implemented initial detections for the samples which are currently available.
Analyses:
Ginp Android Trojan
Ginp is a banking trojan for Android platforms which has been around since late 2019. It began with a fairly standard set of stealer functions: harvesting contacts, intercepting messages, and using overlays to capture sensitive credentials for banking apps.
However since then the family has seen multiple updates such as creating fake text messages on the infected device and triggering push notifications to make the user open particular apps of interest to the malware.
We have reviewed samples submitted to Triage and implemented detections and extraction for the family.
Analyses:
Gozi RM3 Configuration Extractor Update
At the end of March, Checkpoint reported that Gozi RM3 had changed the method it uses for encryption from Serpent to AES.
As Triage’s configuration extractor decrypts data before reporting it, this meant that it did not work with the new version. We have now made the necessary changes and deployed them to Triage.
Analyses:
Guloader Configuration Extractor Update
Guloader is always coming up with new ways to make more work for us, and recently we again observed samples which were not being properly detected and handled by the family configuration extractor.
We have reviewed the samples and extended our detection to cover this variant. We have also implemented some improvements in the backend which should enable Triage to better handle the anti-VM techniques in use by Guloader - we’ll be testing and fully integrating these in the coming weeks.
Analyses:
New Redline Stealer Variant
We have recently made some improvements to our Redline and AgentTesla detections in Triage. As usual, immediately afterwards we have noticed a new variant doing the rounds which gets by the existing signatures.
Redline makes use of the SOAP network protocol for its C2 communications, and a few weeks ago we added support for parsing of these headers to Triage. The new variant still uses SOAP but abuses different aspects of the protocol.
We have updated our signatures to include this variant.
Analyses:
- 210403-gtexn6kycs
- 210403-8j7qxf1122
- 210402-hwstjrzxrj
- 210401-qmxmygyems
- 210331-jyyb1v5l1j
- 210331-33amgtwf6n
WSHRAT Update
WSHRAT has been around in various forms since as far back as 2013. It has changed over time, moving away from its initial highly-targeted attacks towards more standard and less centralised campaigns. It is now available to purchase through cybercrime forums.
We last covered WSHRAT back in October 2020, when first introduced family signatures for it to Triage. This week’s update extends that coverage to include additional samples observed since then.
Analyses:
