Welcome back to our Triage Thursday blog series and our latest set of updates. It’s a shorter post this week - our main update has been a new interface for displaying Mitre ATT&CK techniques, which now appear clearly on the main report page instead of in the details for individual signatures.
We also have updates for some families:
Stay tuned for more major updates coming in the next few weeks - we’re working on lots of awesome features which we hope to be able to show you soon.
Not signed up yet? Visit https://tria.ge/signup to sign up for a free account!
Updated Mitre ATT&CK Matrix
We’ve been looking at ways we can make the Mitre ATT&CK information more accessible, and this week we have released a new view for the TTPs in analyses. This is designed to more closely relate to the official matrix and give easier access to more information for the various techniques.
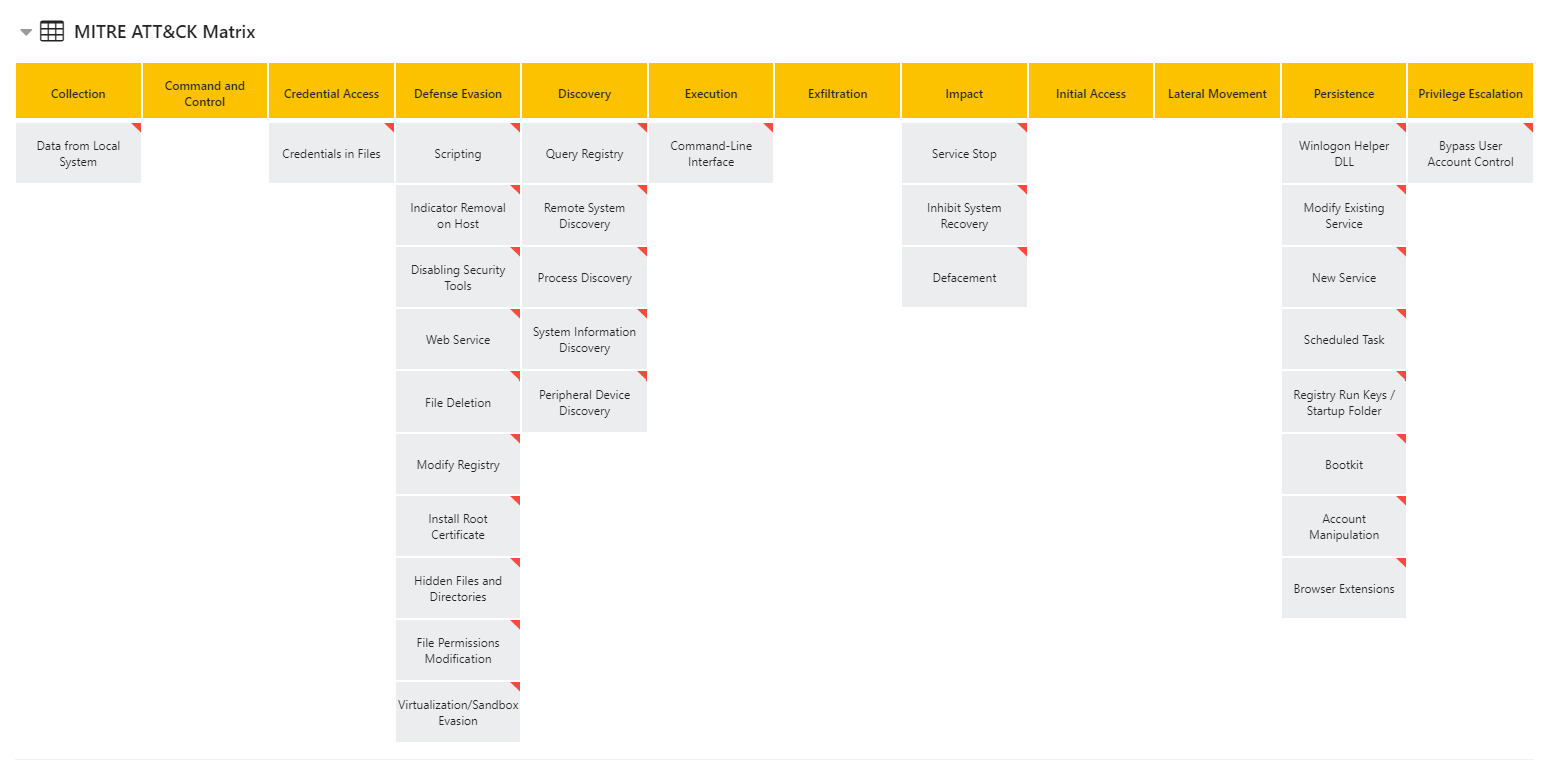
Instead of being hidden away in the signatures, all TTPs are now displayed in one place matched up to the stages defined by the Mitre Matrix. Selecting a technique will take you directly to the relevant description page on the Mitre website.
RegretLocker Ransomware
The new RegretLocker ransomware was first reported at the end of October by @MalwareHunterTeam.
We have added behavioural detection based on this sample and will update as needed if the family sticks around. The ransom note is also quite short and was not being picked up by our parser, so this has also been updated so that it is dumped correctly.
Hello, friend.
All your files were encrypted.
If you want to restore them, please email us : [email protected]
Your hash:
Analysis:
Jigsaw Ransomware
Jigsaw has been around since 2016, named for the wallpaper of Billy the Puppet from the Saw films which it initially deployed to encrypted systems. It gained attention for its unique mechanism of gradually deleting user files if the ransom wasn’t paid promptly, using it as threat to encourage payment. Restarting or deleting the main executable also triggers the deletion of 1000 files from the system.
A new sample recently reported on Twitter by @siri_urz no longer uses the Saw imagery but retains the file deletion mechanism.
We have extended our signatures for Jigsaw to detect the family correctly. Note that this family does not drop a ransomnote, instead giving the user instructions via an interactive interface which is part of the ransomware executable.
The analyses below also feature an anti-VM technique which prevents full execution without manual interaction. A fake error message is displayed, for example warning about the installed .NET version, and a user must click OK and close the dialog for execution to proceed and files to be encrypted.
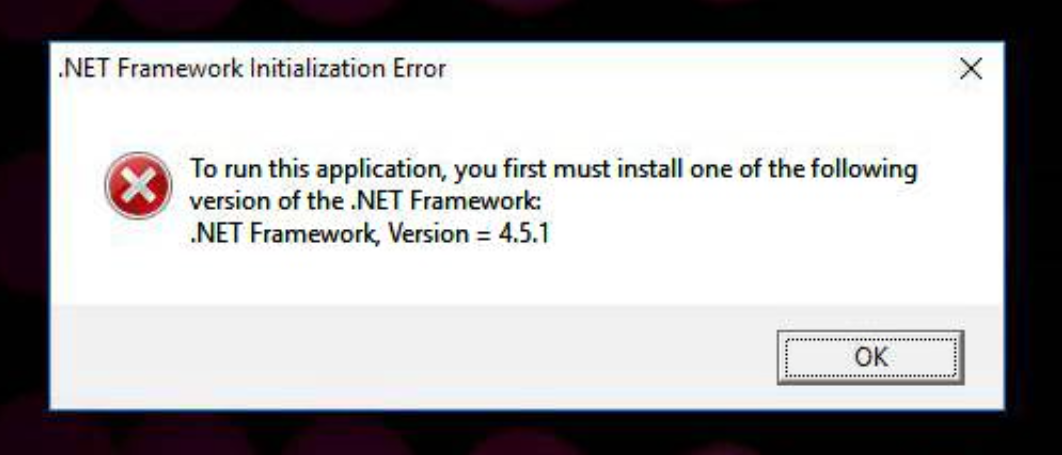
Analyses:
Phorphiex Loader
Phorphiex is a worm and loader which infects systems in order to deploy additional malware, such as ransomware, stealer or cryptocurrency miners. It also incorporates machines into the Trik botnet (not to be confused with Trickbot), which is a network of infected computers used for large scale phishing and bruteforce attacks to infect more hosts.
The family itself has been distributed in a number of forms over the years, mainly scripting formats such as .js files in email attachments. We recently noticed samples being reported on Twitter by @moto_sato which were distributed as screensaver (.SCR) files.
We have gathered what samples we can of this family and implemented detection. However if the C2 is inactive the malware doesn’t carry out many actions, so we will continue to keep an eye on the family for anything not covered by our signatures and update them as needed.
Analyses:
