It’s Triage Thursday, which means it’s time for our weekly blog update on the latest Triage news. As always, we are keeping a close eye on the latest and most trending malware families in the cybersecurity world.
Along with our regular weekly changelog for malware updates and behavioral signatures, we’ve added support for a much-requested feature. It is now easy for you to extract URLs from QR Code images in PDF files within the sandbox!
URL extraction from QR Code image in PDF
Over the past few years, PDF files with embedded QR Code images have become increasingly common. Unfortunately, many threat actors have taken advantage of this by using the QR Code image to hide phishing URL within the PDF. With this feature supported, you can now extract URLs from QR Code images inside PDF files with ease! Let’s check out how it works with a quick example.

When you submit a PDF file that contains an image of a QR Code like the above, Triage will automatically scan the image and check if it contains a valid URL. If Triage detects a valid URL in the QR Code, it will extract the URL from it and make it available for submission, similar to how we handle submitted images (For submitting QR Code image, you can refer to Submitting URLs as QR Code).
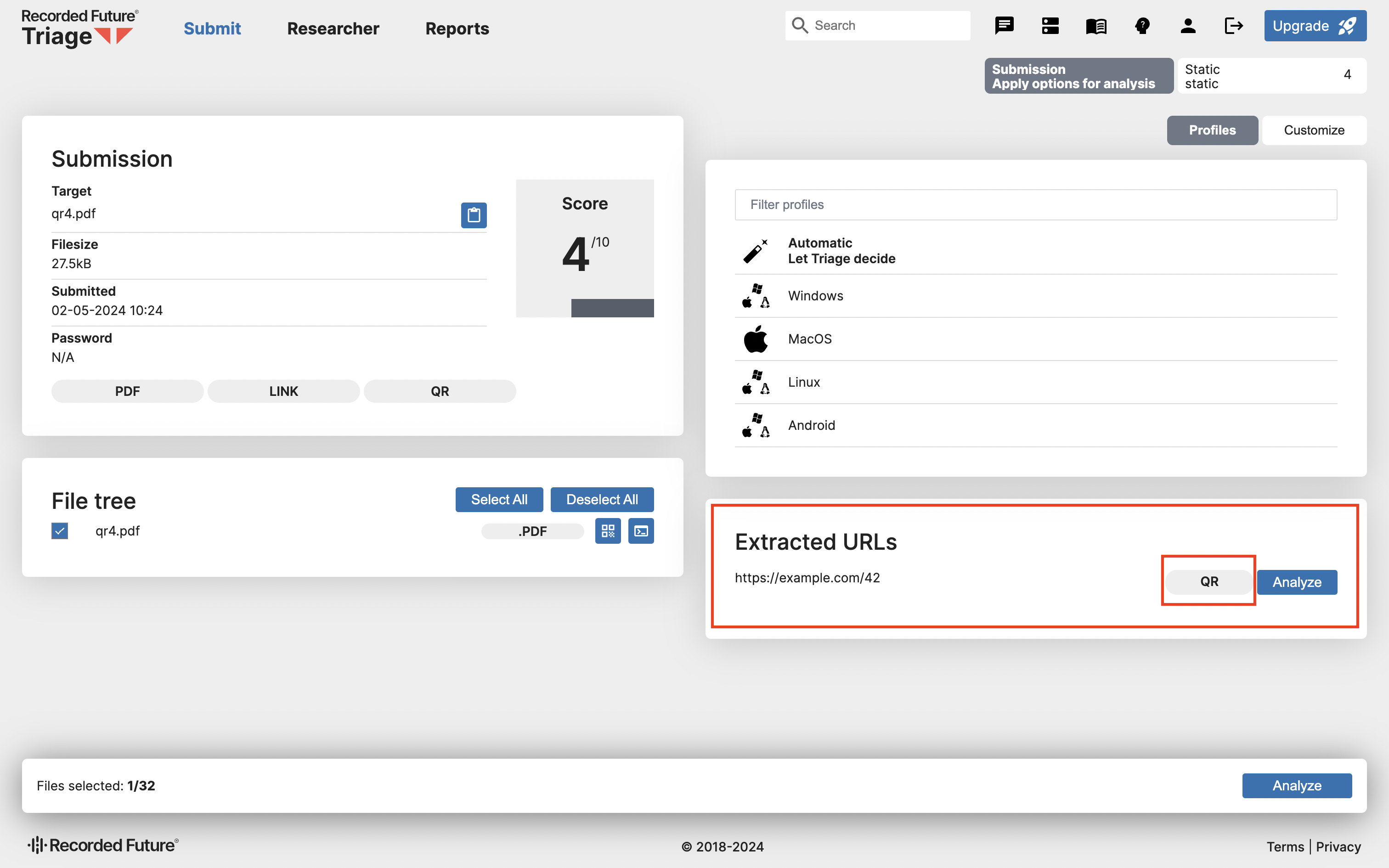
After extracting the URL from the QR Code image, you can find it on the submission page. If the URL comes from a QR Code, it will have a small QR tag.
PDF is a very loose format with huge possibilities for hiding data within it, while still being readable by many relevant programs. We have covered the most common approaches here but we’re always interested in any examples which get past - if you’re aware of tricky PDFs with QRs that don’t extract, please do send them our way!
Now, onto the detection updates and additions for this week.
New Families This Week
- Added detection rule for RawDoor backdoor
- Added detection rule and extraction note for Ransomhub family
Updates for Existing Families
- Fixed Qakbot v.5 extractor
- Fixed detection and extraction for the Vidar family
Updates for Existing Behavioral Signatures
- Extended behavioral detection for Windows Execution TTPs of Mitre Attack
- Extended more Android signatures and TTPs for evasion, persistence, collection, impact, and credential access tactics
If you have any feedback, questions, or issues about Triage feel free to reach out to us any time - we do our best to respond to all feedback but even if we can’t get back to you straight away your files will go into our list of things to review and help us prioritize tasks.
You can find us directly through the website, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
