Welcome back to our Triage Thursday blog series, where we go over all the changes deployed to the sandbox over the course of the past week. We’ve got another long list today so let’s dive in:
- Updated Warzone RAT signatures and extractor for a new variant
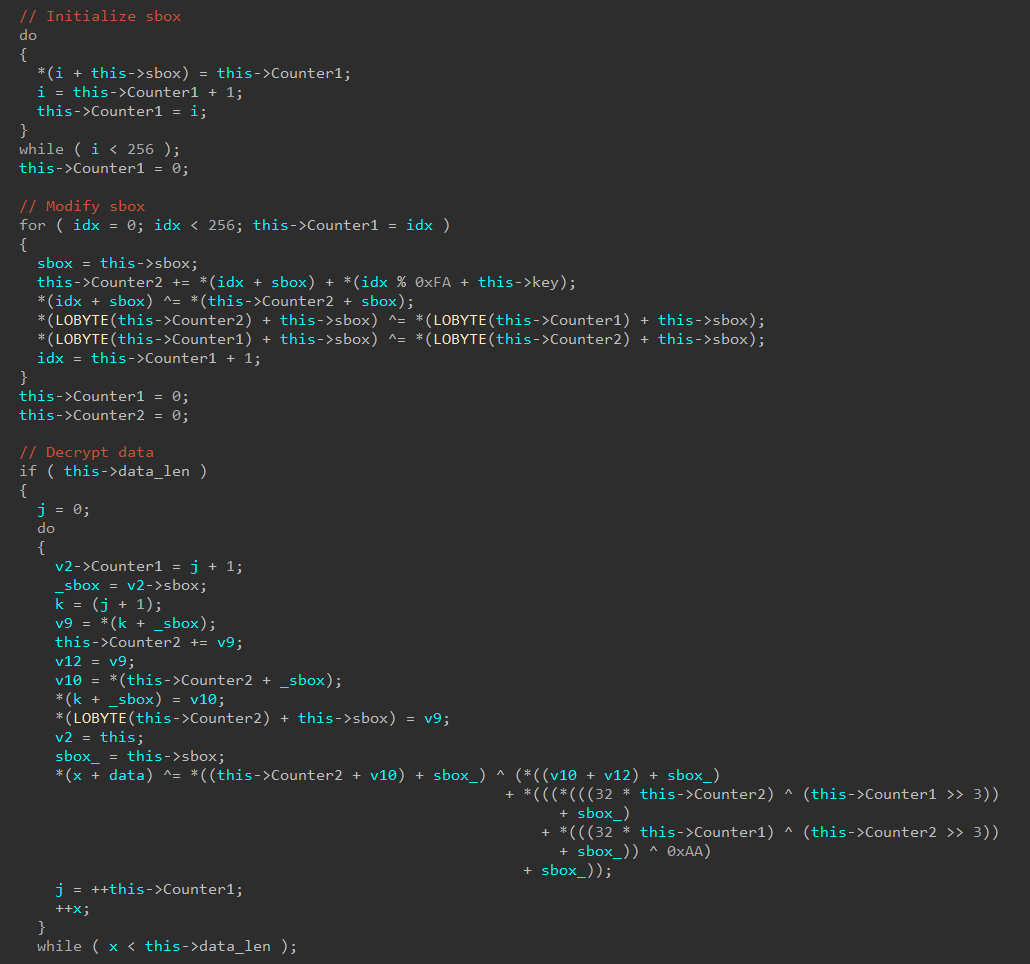
- New configuration extractor for Bandook RAT
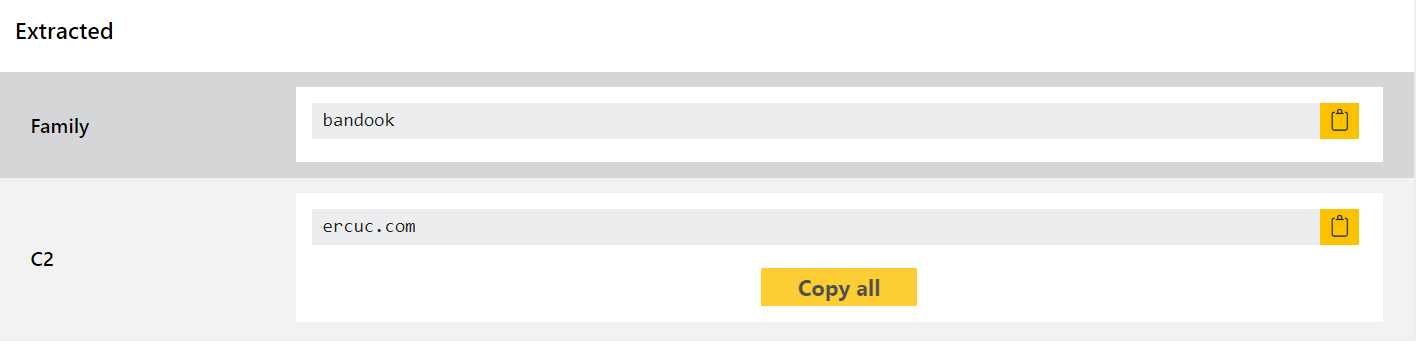
- Updated signatures and extractor for another variant of Raccoon v2
- New signatures for BlackMoon banker
- New signatures for BRATA Android banker
- New signatures for Merlin C2 framework
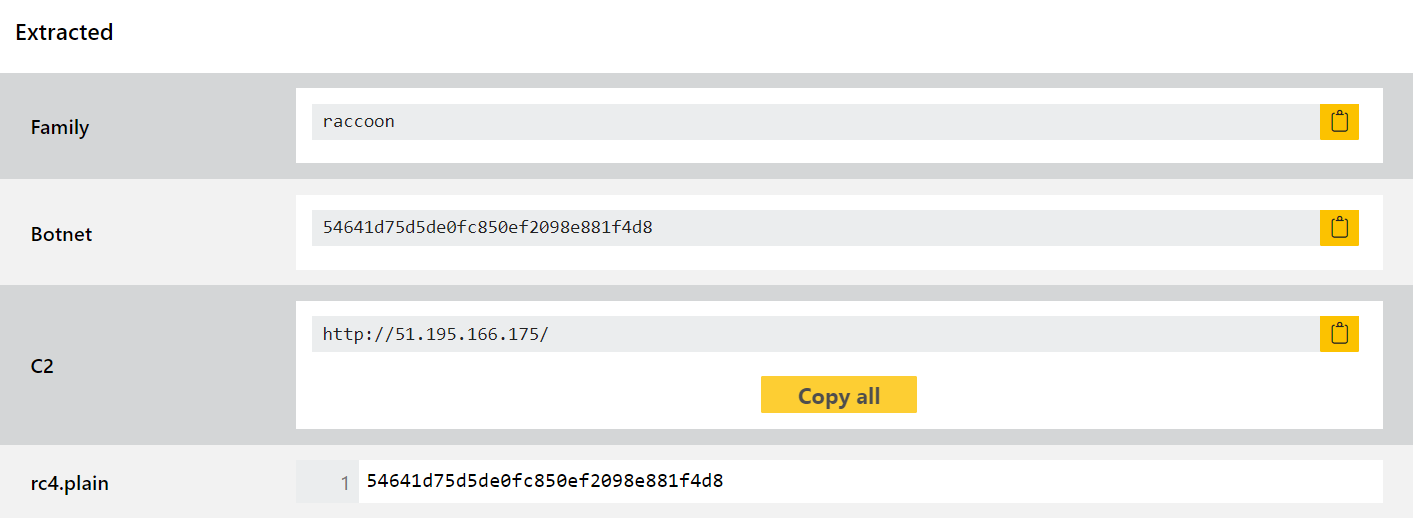
- New signatures for DarkyLock ransomware
- New signatures and extractor for CryLock ransomware
As always if you have any feedback, questions or issues about Triage feel free to reach out to us any time - knowing what is important to our customers and users is very helpful in such a rapidly changing environment. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Warzone RAT
Warzone is a popular RAT with an extensive feature list which is sold as a service for others to use in their own campaigns. It has its own branded website which presents it as a legitimate remote administration tool instead of selling solely via underground forums.
The malware uses its own DNS server to ensure reliable service, and includes a number of evasion techniques to disable Defender and gain persistence. A full writeup of the family, including details of features like its UAC bypasses, can be found in Checkpoint’s blog from February 2020.
We recently started seeing some new versions of Warzone which have changed the way they protect their hard-coded configuration. Previous versions used a standard RC4 algorithm for encryption, but the recent ones seems to have moved to a custom implementation which changes things up a bit - a snipping of this is shown below.
This change of course broke our configuration extraction since our existing code couldn’t parse them correctly, so we have now updated this to make sure both approaches are properly handled.
Analyses:
Bandook RAT
Bandook has a long history as a family, going all the way back to 2007 in its original form. It was mostly inactive for some years, only appearing occasionally in specific campaigns during 2015 (Operation Manul) and 2017 (Dark Caracal), but then popped up again in 2020 with a few new variants. It was seen carrying out a spate of attacks against various entities, including the UK’s National Health Service at the end of 2020. Since the original release - later traced to a Lebanese citizen going by the alias PrinceAli - the source code for several versions of the RAT has been leaked resulting in a large number of customisations and variations in the payloads seen in the wild.
It is a RAT/backdoor capable of receiving commands from C2 infrastructure, effectively providing full remote access to infected machines supported by automated processes to simplify usage. Delivery mechanisms vary somewhat, but mostly revolve around malicious Office documents distributed via phishing emails. These then lead to a Powershell loader which in turn deploys Bandook. For a more detailed look at the technical capabilities, including a breakdown of the commands generally supported, take a look at Checkpoint’s blogpost from 2020.
We added detection support for the family back in March this year after a bit of a rise in samples appearing on Triage, but as this trend has continued we’ve revisited it this week to add a full configuration extractor to dump out C2 information.
Analyses:
Raccoon Stealer
Raccoon was a well established family up until March 2022, when operations were shut down after a key developer was killed in the Russian invasion of Ukraine. It remained inactive until early June when the operators resumed posting on the underground forums and began to push a version 2 of the malware.
The new version appears to have involved rewriting significant sections of the malware but currently the overall flow and functionality is mostly unchanged. According to a post by S2W it claims some improvements like an expanded list of targets from which to harvest data, cross-compatibility with 32 and 64 bit systems, string encryption, and a fully automated payload builder.
We’ve recently started to see some new samples which continue the changes introduced for version 2 of the family, so today’s updates just tweak the signatures and extractor a bit to ensure reliable coverage.
Analyses:
BlackMoon Banker
BlackMoon is a fairly old family with the first detections going back to 2014. Based on reports it is entirely focused on stealing financial information from victims in South Korea, targeting online banking for a number of banks in the country. Although multiple versions have been seen over the years since this has remained a common theme across them all.
The malware is generally dropped via drive-by download, exploiting issues in outdated browsers/browser plugins to install itself. It is also often seen being delivered as a fake software update for things like Java or Flash - although the effectiveness of this has diminished in Europe and the US in South East Asia it is more common to find consumers using dated browsers like Internet Explorer. A breakdown of versions seen in more recently is available in this report from February 2021.
We have reviewed a number of samples for the family and implemented initial static detection for them.
Analyses:
BRATA Banker
BRATA is a banking trojan for Android operating systems that was first observed in November 2021. At first it was going after data from Italian banks but it has seen a few evolutions since then to expand its target list and supported functionality - it now also supports banks in the UK, Poland and Latin America. Back in January 2022 Cleafy published a blogpost summarising the new versions which they narrowed down to 3 main payloads with slightly different capabilities. These have begun to move away from purely banking-based information theft and include things like GPS tracking of the device, forced factory reset, and the ability to download a 2nd payload during runtime to bypass static detection.
The banker part itself follows a common pattern for this on Android, abusing the accessibility service to effectively gain full visibility on the user’s actions. The malware can be directly controlled by the attacker using a number of predefined commands such as get_screen which makes it start to capture screenshots and send them back to the C2 server.
This week we have reviewed available samples and implemented initial detection for the family.
Analyses:
Merlin C2 Framework
Merlin is a post-exploitation framework for stealthy C2 communication which was developed for use in red-team exercises/pentests. It is available on Github and supports encrypted network communication across a few different HTTP protocols which can be used to slip under the radar of common detections.
Although not a malware family it’s still not something you’d want to find on your network so we’ve added some quick detections to classify it properly in future reports. It is written in Golang and makes the most of its cross-compilation features with support for Linux, Windows and macOS versions.
Analyses:
Linux:
Windows:
MacOS:
DarkyLock Ransomware
DarkyLock is a new variant of the old Babuk ransomware family. It first popped up a few weeks ago and is (currently) easy to tell apart from others due to its use of the .darky file extension and clearly labelled ransomnote.
Babuk itself first appeared at the start of 2021 and saw some success across a number of large companies, culminating in the middle of the year with an attack against the Metropolitan Policy Department of Washington D.C. in April of that year. Although fairly low-tech the family has functional encryption which so far has not made it possible to decrypt files without working with the ransomware operators.
In July 2021 after a period of internal troubles within the developer group a member of the team uploaded the source code publicly, leading to other offshoots like DarkyLock.
The ransomware was already well detected on the platform but we have added some family name definitions to make sure it gets tagged properly.
Analyses:
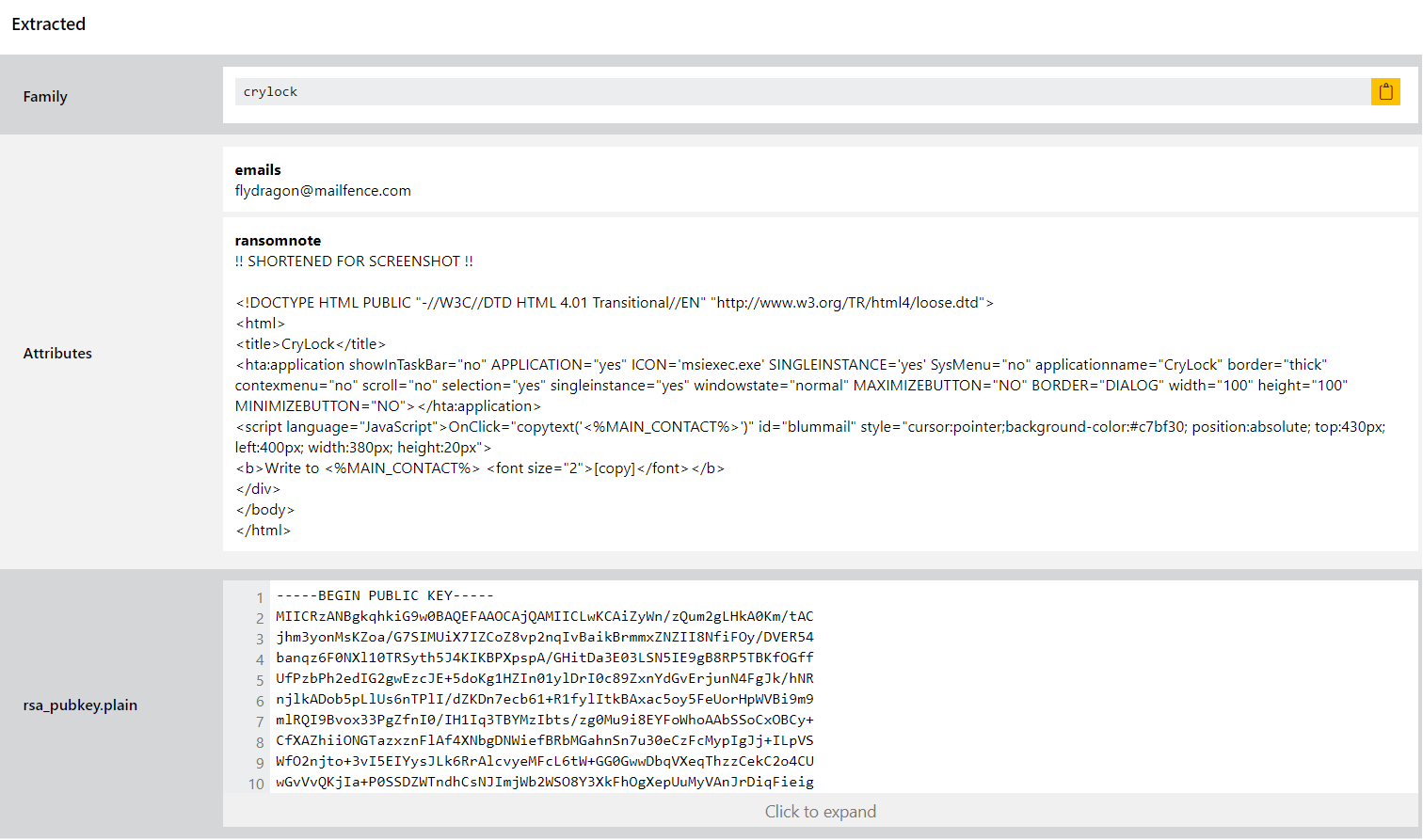
CryLock Ransomware
Like DarkyLock CryLock is also an evolution of an older family - in this case Cryakl which first appeared back in 2014. It is often deployed by other malware families, or in some cases is directly downloaded from malicious websites disguised as legitimate applications.
Ransom negotiation is quite manual with victims having to email the operators directly - no price is listed in the note, and is instead issued directly. They also offer to decrypt up to 3 files as proof that they can.
We have added standard detections for the family, and also a configuration extractor which can dump out RSA public keys used by the sample as well as the raw HTML ransomnote.
Analyses:
