Welcome back to our Triage Thursday blog series, where we round up the week’s main updates to the platform. It’s a shorter one this week as the team’s been focusing on a couple of more fiddly families, but we still have a few new additions to the list of configuration extractors as well as some updates for an existing family:
- Updated configuration extractor for BumbleBee
- Added signatures and configuration extractor for Octo Android malware
- Added signatures and configuration extractor for Nymaim
- Added detections for PureCrypter loader
As always if you find any problems with the Triage platform or its detections please do let us know. Community input is a vital part of tracking and keeping up to date with the rapidly evolving malware landscape and is extremely helpful in making these updates possible. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account!
BumbleBee
BumbleBee is a loader which rose to prominence back in April 2022. So far it has formed part of the toolkit of an Initial Access Broker group called EXOTIC LILY, who gain access to systems and networks which they can then sell on to other groups like ransomware gangs rather than directly exploiting it themselves. For example BumbleBee was seen early on distributing Conti ransomware and CobaltStrike payloads.
On a technical level it is a fairly typical example of its type, using WMI to harvest general information about the system and report it back to the C2 infrastructure which then issues commands for the next steps. This task can vary but mainly revolves around deploying code and payloads onto the system. You can find a full writeup of the family from Google’s Threat Analysis Group here.
We added detections and a configuration extractor for the family back in April but some samples were recently brought to our attention which were showing garbage data in the output. We’ve now reviewed these and made the necessary updates. If you come across any similar issues - with BumbleBee or any other family - please feel free to let us know!
Analyses:
Octo
Octo first popped up under this name in early 2022, with ThreatFabric reporting that they came across the name on underground forums on January 23rd. Analysis since then seems to suggest it was developed around the end of 2021 by a new developer using the source code for an old family called ExobotCompact, which was in operation until around 2018 when it shut down and the source code was leaked.
The family is another Android stealer which seems to be a direct successor to ExobotCompact, with ThreatFabric’s analysis suggesting that it uses basically the same functionality with some additions and general rebranding. Chief among the changes is a new remote access feature which enables the family to also be used for on-device fraud (i.e. where a device is directly hijacked to permit theft etc. rather than just exfiltrating data which can be used later) - major targets for this of course include multi-factor authentication and banking apps. Including Exobot functions it has an extensive feature set covering SMS phishing, keylogging, overlay attacks, and the ability to intercept phone calls and text messages.
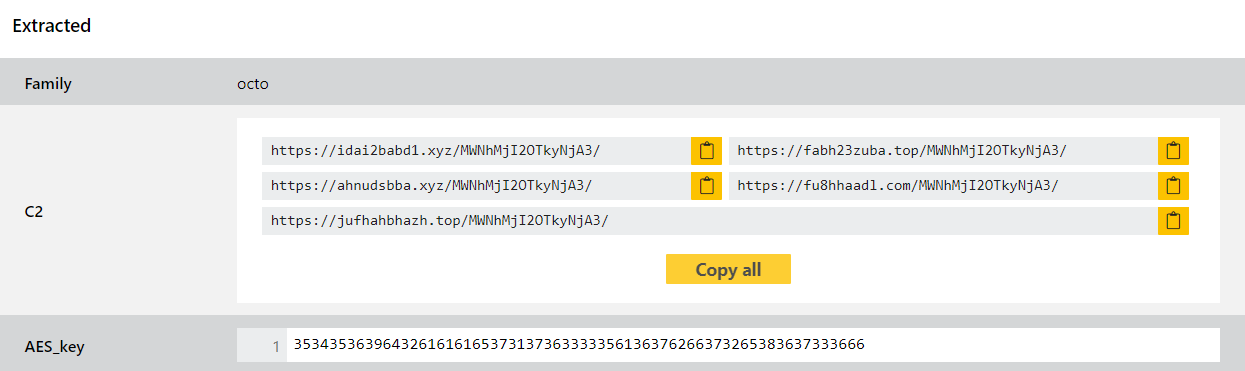
We have reviewed some available samples and implemented behavioural detections and a configuration extractor to dump C2 information.
Analyses:
Nymaim
Nymaim is a trojan/loader which has been around in various forms since 2013. In its first iterations it also included its own 2nd stage payload which was a screenlocker aimed at extorting victims into paying a ransom. It has since done away with that 2nd stage instead being primarily used to deliver other families like Ursnif and Pony - in 2016 it was even combined into a new trojan/stealer with Gozi that earned the nickname GozNym.
Although old its regular updates have kept the family relevant over the years, and it has popped up repeatedly with periods of heightened activity. It has become quite advanced by now with extensive anti-VM and anti-analysis techniques built in - for example Proofpoint reports that it at some point started using its own bytecode language which is directly interpreted by Nymaim, running in a virtual machine managed by the malware.
Since activity on this family seems to be going through one of its busier period again we’ve developed detections and a configuration extractor for it. We have reviewed as wide a cross section as we can but for something that goes back as long as this there are likely to be some edge cases we haven’t covered, so if you come across anything please do let us know and we’ll be monitoring it ourselves as well.
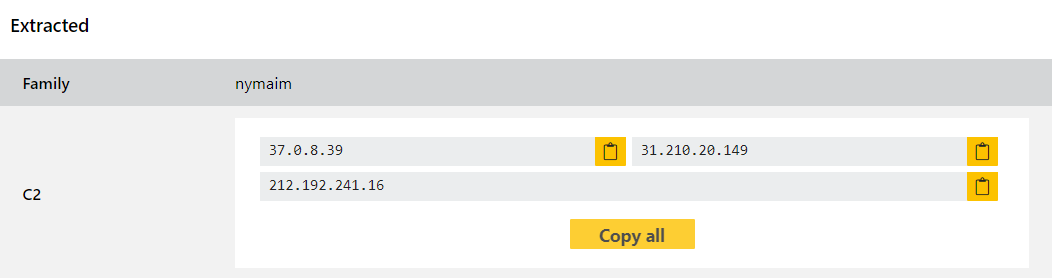
Analyses:
PureCrypter
PureCrypter is another loader family, this one written in .NET and using obfuscation and encryption techniques to evade static detection techniques. It has reportedly been around since March 2021 and can be purchased by attackers for use in their own campaigns rather than being associated with any single group.
According to Cyware’s report on a new update in June 2022 it has been seen delivering quite a large range of other families including AgentTesla, AsyncRAT, RedLine, Remcos, and Warzone RAT. The malware is still in active development and recently added the ability to communicate over Telegram for C2 as well as expanding on anti-VM methods. Configurable options are defined using Google’s Protocol Buffer format to make it harder to detect strings etc. in the payloads even once decrypted.
Buyers can customise their particular strain of PureCrypter using a web-based builder framework which includes a large range of different options around startup locations, enabled evasion modules, build metadata etc. The tooling also helps with building initial infection methods with an Office macro builder included. A technical writeup can be found in ZScaler’s blog from June 13th 2022.
We’ve haven’t seen huge numbers of this family yet but a few have come onto our radar over the first half of 2022 so we felt it was time to add detection. We have reviewed the samples we’ve identified and implemented some signatures for them.
Analyses:
