Welcome back to our Triage Thursday blog series, where we take a look at the changes made during the week and introduce new features.
Today we have a few updates to address new versions of families which have appeared recently, including Emotet returning with its Epoch 5 variant. We also have a new family and some false-positive fixes:
- Added more information to static reports
- Updated detections and extractor for new Emotet Epoch 5 samples
- Tweaked rules to handle new Redline stealer variant
- Fixed detections to work with new version of the Flubot Android banker
- Added rules for new OnlyLogger variant
- Created initial detections for Babadeda crypter
- Fixed false-positives resulting in incorrect Redline and Mimikatz detections
As always if you discover any issues or missing detections while using Triage, please do send us feedback - it’s a big help in deciding what we should be prioritising. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Expanded static reports
As part of our plans for 2022 we intend to expand on the information Triage makes available during the static analysis phase, moving toward including a more detailed breakdown of the file and its contents as available at that stage.
We have deployed the first step of that this week, although currently it is only available to users of the API. With this new update, the following additional fields are included:
- Imphash details
- Authenticode validation
- Countersigned timestamp validation
- PE section information
Note that these are included in the static report only - you can find information on that in the documentation. We’ll be adding support for this new data in the web UI in a coming update, so stay tuned for that!
Emotet Epoch 5
Over the last week or so we have received a lot of reports about the new Emotet version referred to as Epoch 5. We’d like to thank everyone who reached out with samples - it helps us a lot with turning these things around quickly.
In this case the update has been a bit more complicated than usual as the changes required some tweaks to internal components which affect our memory dumping capabilities. However these have now been implemented, and the rules and configuration extractor have been updated to properly handle these samples.
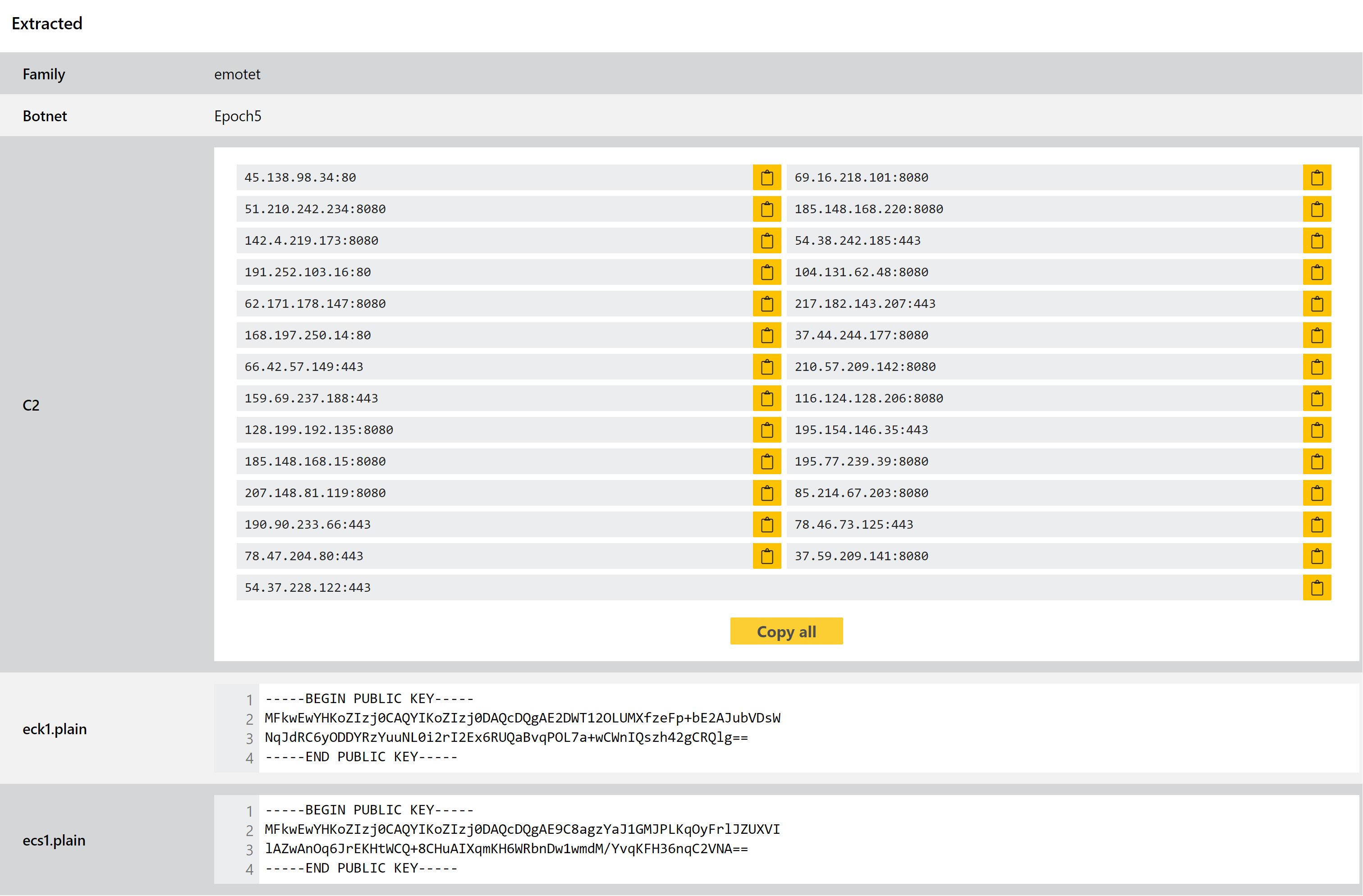
If you reported an analysis to us you should find that that has been reprocessed to reflect the change, and any new submissions will have the updated handling.
It’s a pretty safe bet this will not be the last time Emotet appears on this blog, and we’ll be keeping an eye out for any future changes as usual. Some Epoch 5 examples are listed below for reference - you can find others using Search.
Analyses:
Redline Stealer
Redline is a long-running infostealer which is currently extremely common in the wild. It is actively developed and has appeared on this blog fairly regularly since we added initial support for it.
We last visited the family back in July last year when a change to their C2 communications affected detection, but at the start of 2022 we observed another new variant which has been getting past our extractor.
We have reviewed a significant number of samples and updated our detections accordingly, so all Redline samples should be properly handled again.
Analyses:
Flubot
Flubot is an Android trojan/infostealer first discovered in late 2020. Spread mainly via SMS phishing it gained attention at the start of 2021 after carrying out large scale spam campaigns against European users. The family was a major follower of an overall trend with mobile malware since the start of the pandemic where it makes use of lures related to package delivery services like FedEx, DHL and Correos.
We made some improvements to our Flubot detections in our last blogpost of 2021, but this time we’re addressing a brand new variant reported to us by a user earlier this week. This version was completely bypassing our family detection, so we have applied updates to make sure that it is handled properly.
Analyses:
Babadeda Crypter
Babadeda is a new crypter observed in late 2021 and reported on at some length in a blogpost by Morphisec. Crypters are a class of malware which sit on the line between a standard packer and a first-stage loader, using encryption to obfuscate and hide the true contents of the final payload.
In Babadeda’s case it is doing this very successfully, getting very low/non existent detections on most anti-virus solutions. This makes it a significant threat as even well known and documented payloads can leverage this to bypass all defences and gain access to systems.
So far it appears to have been mainly used in attacks against the cryptocurrency and NFT communities, with threat actors distributing their campaigns via Discord spam. A detailed look at these campaigns and the attack chain can be found in the Morphisec blogpost.
We have added some initial detections to report the presence of this crypter, and will continue to look at ways to get the most out of analyses where it is present.
Analyses:
OnlyLogger
OnlyLogger is, despite the name, a small loader module which was reported on Twitter in mid 2021. We added some detections for it in December but have since noticed some additional samples not fully covered by those. As such we have revisited to update and improve the detections to better support the entire family.
Although the name suggests it is a keylogger or similar, it actually just comes from debug paths embedded in the original samples. It is really a first stage loader, using the web service IPLogger to verify the IP of the infected machine and fetch additional payloads.
Analyses:
