We’re constantly pushing small updates to improve detections on Triage, but this week sees the release of some larger changes in a few different places. In this blogpost we’ll take a brief look at these and go over some examples to demonstrate their use and show the new information which is available.
Feel free to get in touch with us to give us any feedback on these or other aspects of Triage. Follow us on Twitter (@hatching_io) to catch all the latest updates, big and small, as they are released.
Not signed up yet? Head on over to https://tria.ge/ to request early access to the platform!
Summary of changes:
- Listing dropped files and memory dumps in web interface
- Automated dumping of all files deleted through Explorer during an analysis
- New HawkEye Reborn config extractor
- New SmokeLoader Extractor
- MassLogger Log file dumping
- Updated Qakbot config extractor
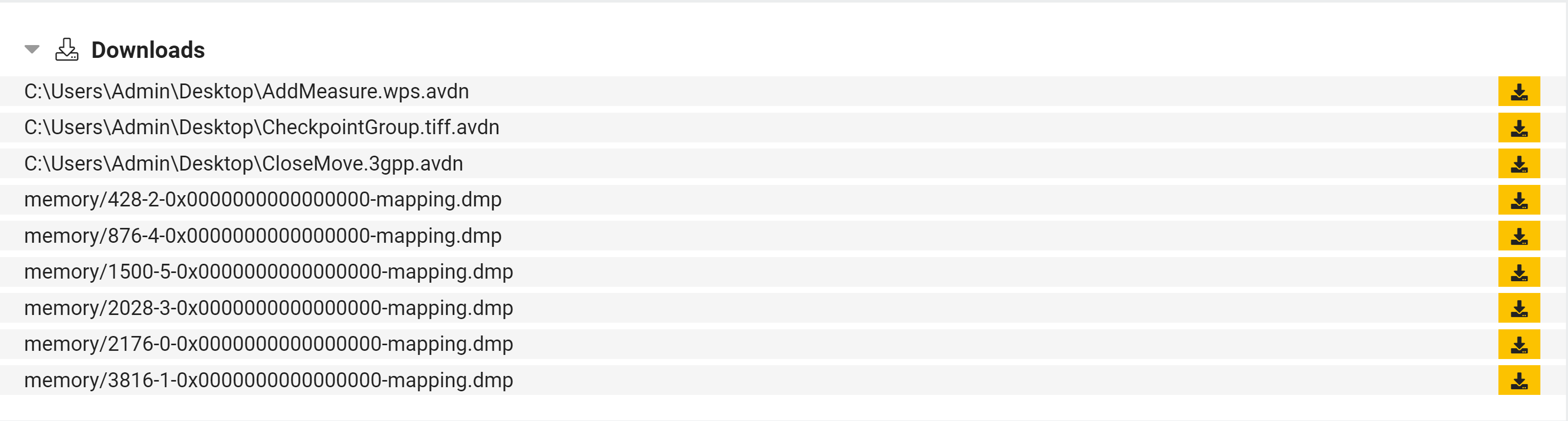
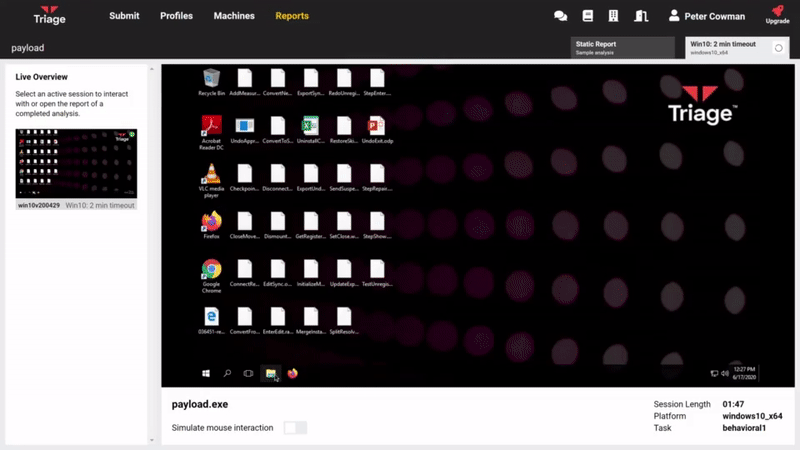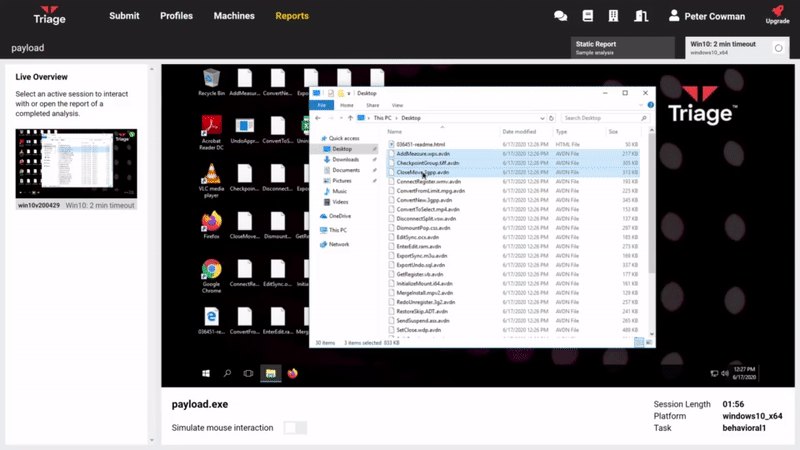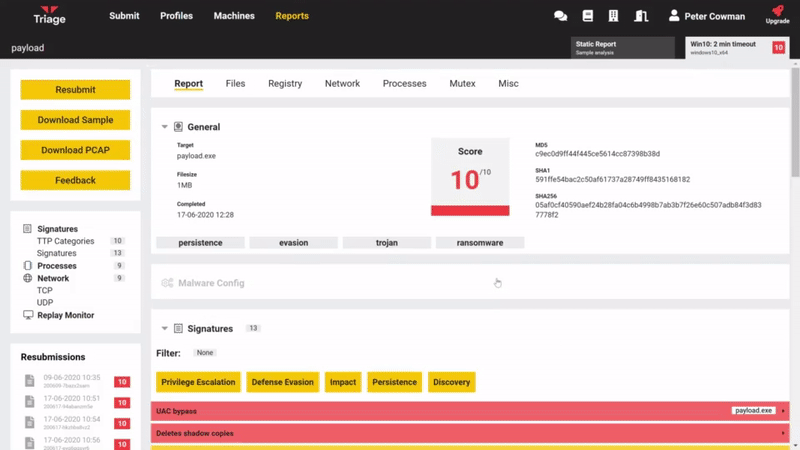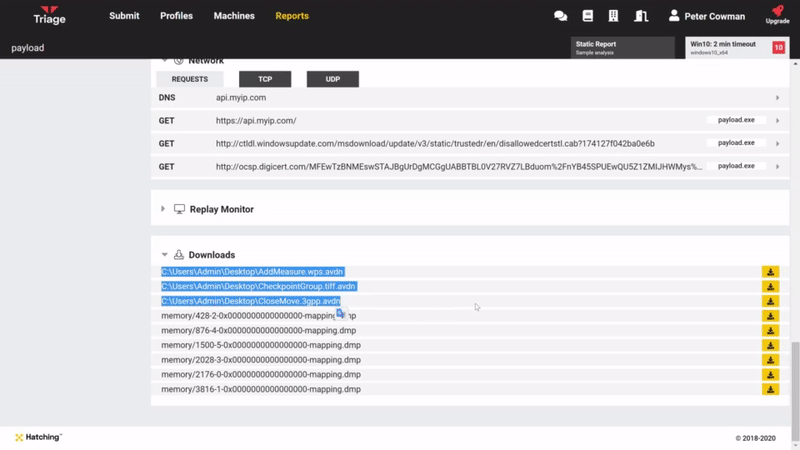
List Dropped Files/Memory Dumps in Web UI
Dropped files from an analysis are now available to download directly from the web UI. A new section has been added at the bottom of the report pages (underneath the Replay Monitor) which lists the available file names and provides a download link.
File download using the API functions just as before with no change. For more details check out our past blogpost on the feature.
Automated Dumping of Deleted Files
One of the more requested features from Triage users has been a way to dump particular files during analysis. Triage already includes some dumping strategies but these only trigger under predefined circumstances, sometimes meaning that a particular file may not be available.
To aid with manual analysis we have added a new feature which will dump any files which are deleted through the Explorer interface. This file will then be available for download through the API or straight from the web UI via the new download section.
New HawkEye Reborn Extractor
Triage has included behavioural detection for many variants of HawkEye for some time. This update widens that detection and adds configuration extraction for payloads.
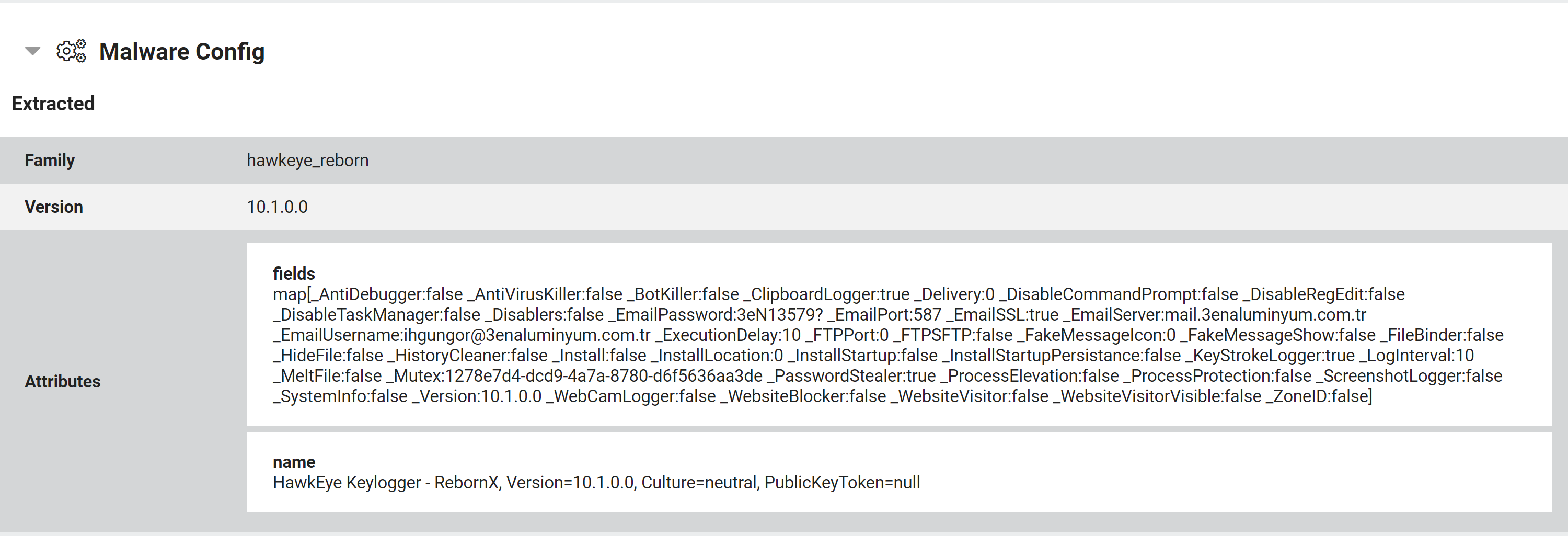
Example HawkEyeReborn configuration
HawkEye is another successful infostealer which has been active since 2013. It can steal credentials from a wide range of software (browsers, email clients, FTP/SSH programs etc.) and has recently added loader capabilities to let it install other malware once it’s infostealer activity is done.
Many campaigns now use the newer variant of the family called HawkEyeReborn, which is a total rewrite of the original with improved performance and features.
Examples:
New SmokeLoader Extractor
SmokeLoader is a modular loader which has been available to buy since around 2011. It is generally used in campaigns as the first stage for other malware, and has come to feature a wide range of anti-analysis and anti-virtualization functionality. It is still actively supported and developed.
As with the other examples covered in this blogpost, SmokeLoader includes a configuration within the executable which stores the settings for the campaign. In this case it includes version information, RC4 keys for decrypting resource strings and C2 communications, and the C2 domain/IP.
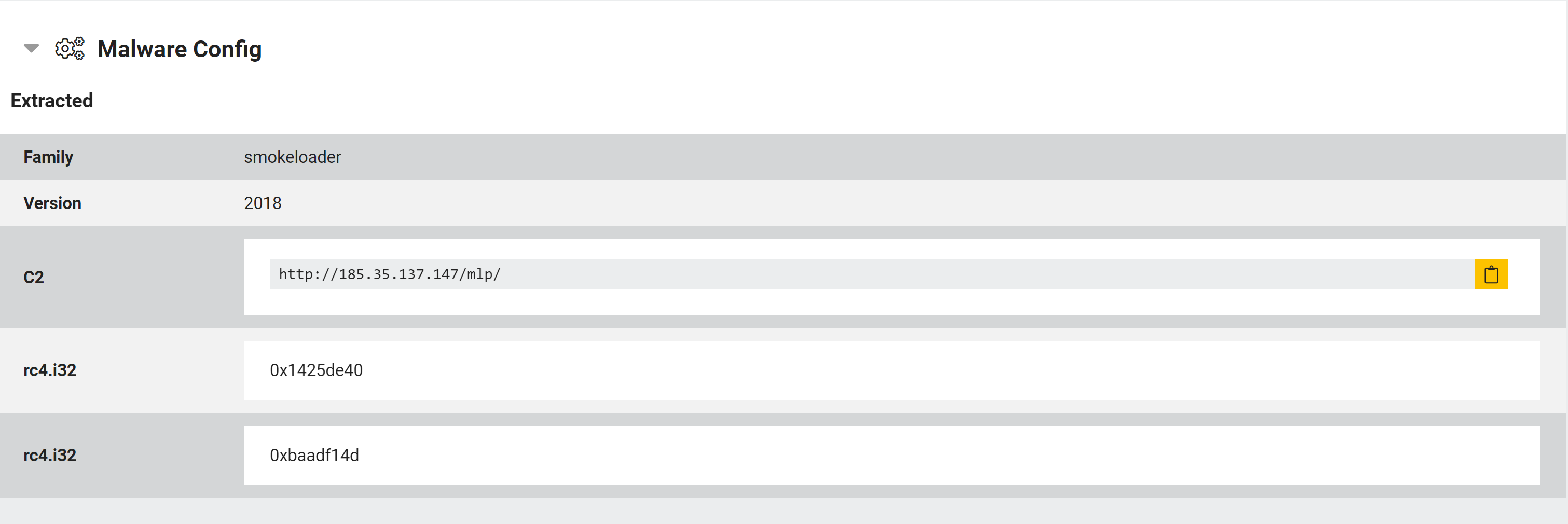
Example SmokeLoader configuration
Examples:
MassLogger Log File Dumping
MassLogger is a recent keylogger first seen in 2020 and gained some new attention in June when it was used with the GuLoader dropper in a widespread phishing campaign. It is developed by the same author as a number of other successful malware families such as AsyncRAT and LimeStealer and sold online via a subscription model.
To help with tracking campaigns and botnets using MassLogger, Triage has been updated to automatically dump the log file created during the stealer’s execution. This file mostly contains basic system information for the VM, but also includes the version and configuration settings for the sample.
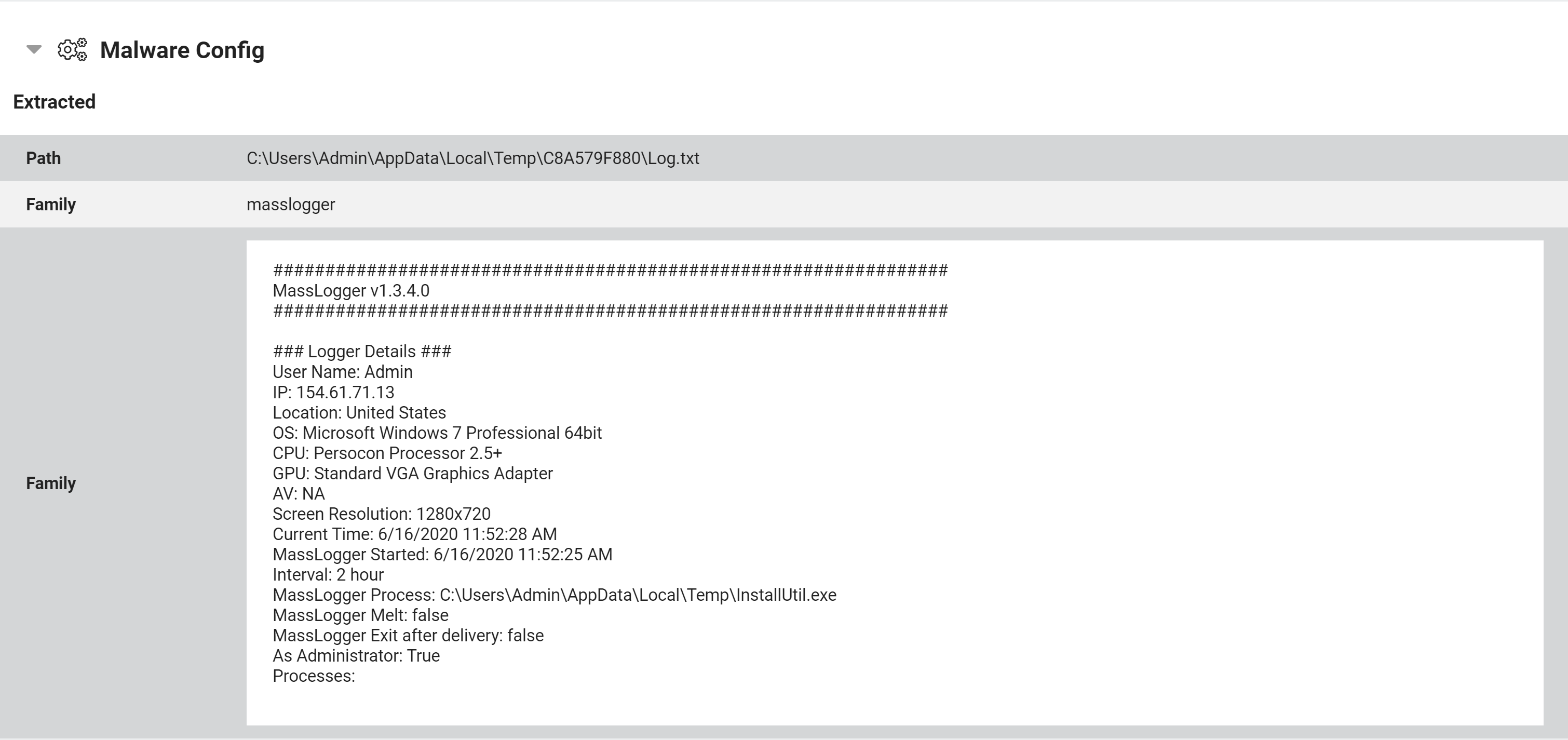
MassLogger Log File
A couple of versions of the family have been submitted to Triage since the family appeared in the wild. Examples of these are below:
v1.3.4.0
v1.3.7.0
v1.3.7.1
- https://tria.ge/reports/200616-ke3m3f7ska/behavioral1
- https://tria.ge/reports/200616-mwqqwx9a4a/behavioral1
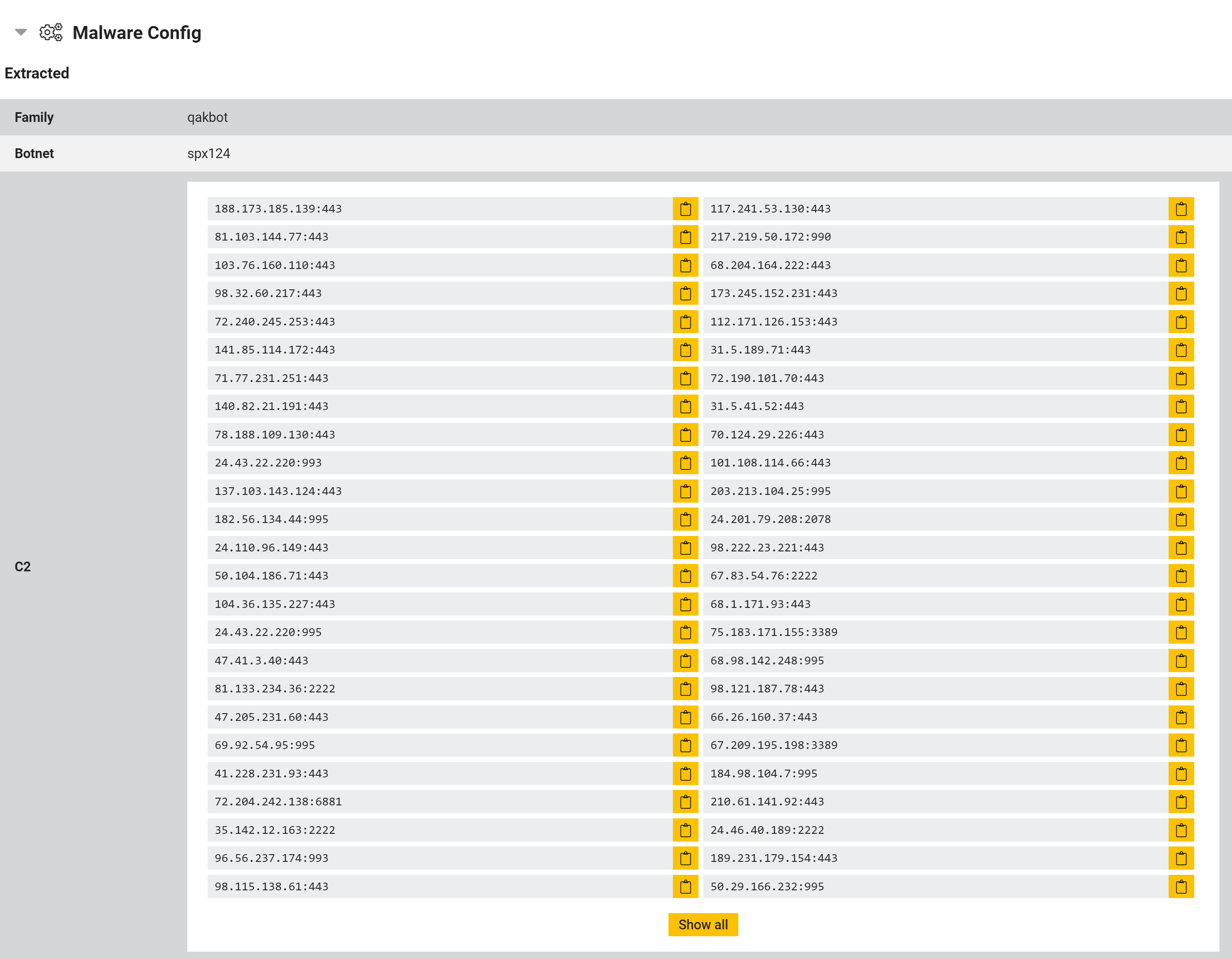
Updated Qakbot Extractor
The Qakbot trojan family has been around in some form since 2009, filling a range of roles over time. From its initial base as a info-stealer trojan it has resurfaced in multiple campaigns, from a banking trojan locking out Active Directory servers to ransomware dropper.
Triage has supported behavioural detection of most Qakbot samples for some time. However with the new update this has been expanded to also include extraction of the configuration file embedded within the Qakbot payload, as well as covering more variants overall.
In Qakbot’s case, this allows the automatic extraction of the sample’s botnet ID value and C2 domains/IP addresses - the other data in the file is mostly system information from the VM.