It’s Thursday again (seriously, I’m sure they used to be further apart than this) and that means it’s time for another blog taking a look at the week’s Triage updates.
As many of you will be aware, last week saw us add Suricata support for Triage, leveraging it network scanning capabilities to expand on our existing detections. We would just like to thank everyone for their tremendous support of that release - it’s great to see such a positive response. We’ll be continuing to expand on this in the coming weeks/months, and we also have a lot of plans which we hope you’ll also be excited about once we have them ready for deployment. Watch this space!
In the meantime, read on below for more on this week’s detection changes. The list is a little shorter than usual today, but we’ve got a lot going on in the background which we’ll be able to talk about more in the future.
- New configuration extractor for Matiex family
- New detection and configuration extractor for Hydra Android banking trojan
- Updated Raccoon configuration extractor and family signatures
- Tweaked detections for Redline stealer
In other news this week saw us pass a bit of a milestone with our public cloud - we now have more than 5,000 registered users!
We are also still looking for a Go developer to join to Hatching team. If you’d like to be involved in the next steps of Triage’s journey - or know someone who might be - you can find the full job listing here. Feel free to reach out with any questions.
If you have any questions or come across any issues on Triage, please feel free to reach out to us. You can contact us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
New Matiex Configuration Extractor
Matiex is an advanced keylogger and infostealer which is sold to users through underground forums and, initially, it’s own open website. It supports a wide range of features, going well beyond standard keylogger functionality with ability to recover data from a large number of programs like browsers and email clients, as well as capturing audio/video, disabling security software, bypassing UAC and much more.
We added behavioural detection for the family back in September 2020, and this week we’ve extended this to also include a full configuration extractor. According to its advertising, Matiex supports 4 main delivery methods - Discord, SMTP, FTP and Telegram - and our extractor is able to dump the credentials/URLs used.
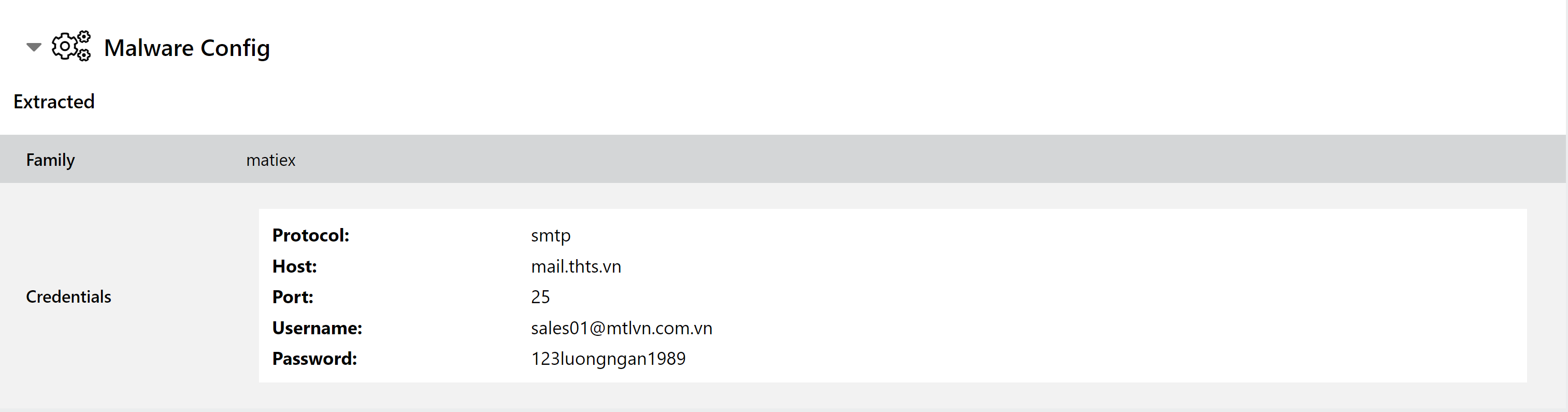
Check out the samples below to see it in action, or search Triage with family:matiex.
Analyses:
New Family Detection and Configuration Extractor for Hydra Android Banker
Hydra is an banking trojan/stealer which targets Android devices. It is based on the older BankBot malware which is the predecessor for many other current Android malware families including common strains like Anubis or Cerberus. Like those, it also leverages overlays to intercept data entered into certain apps which it can then send back to its C2 servers.
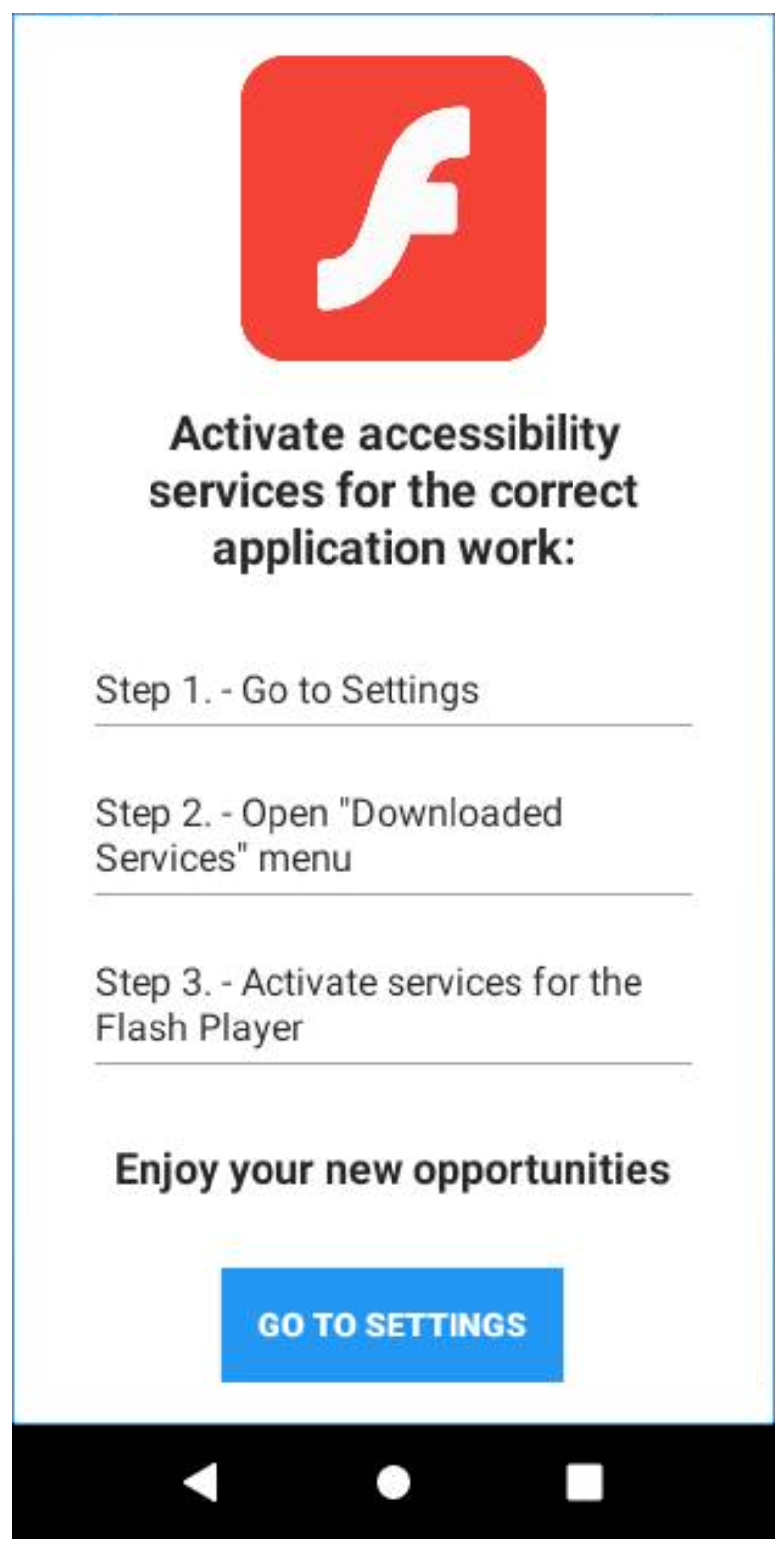
The family has been around since at least mid 2019, but has never been quite as widespread as some other Android based malware. However we are still observing samples being submitted to Triage, so this week we’ve reviewed them and developed detections to cover them.
In many cases, the samples are also covered by a new configuration extractor to dump out the C2 address directly. This currently only affects a subset of the family’s variants however.
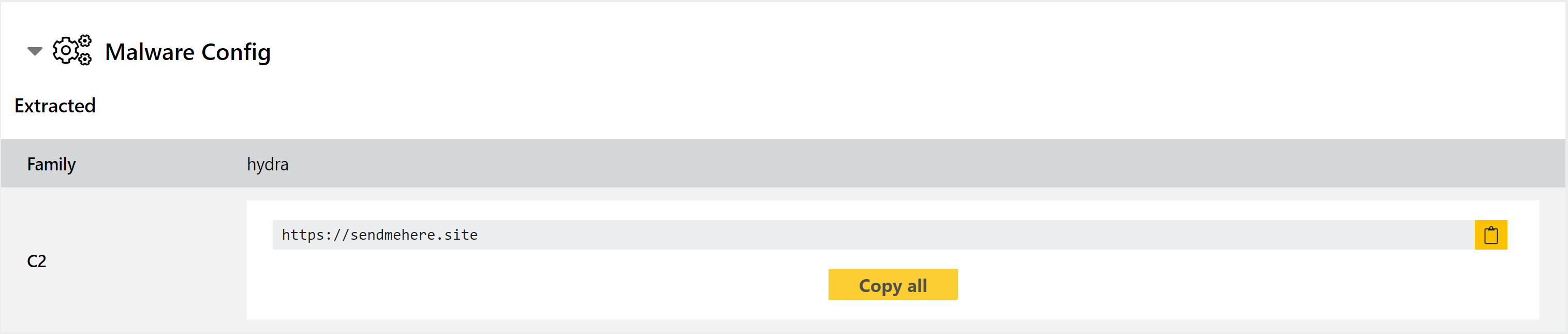
Analyses:
Updated Raccoon Configuration Extractor
Raccoon is a fairly standard infostealer, targeting user data stored by common web browsers and any available cryptocurrency wallets. It is most often seen distributed via phishing emails, generally using macro-enabled Office documents.
The family was first seen in April 2019 and although it is relatively basic in its implementation and supported functionality compared to others in this space, it has proved to be quite popular with cybercriminals due to its low cost and solid reliability. It has seen extensive use since it appeared and is still very active in 2021, being one of the most common threats we see submitted to the public cloud.
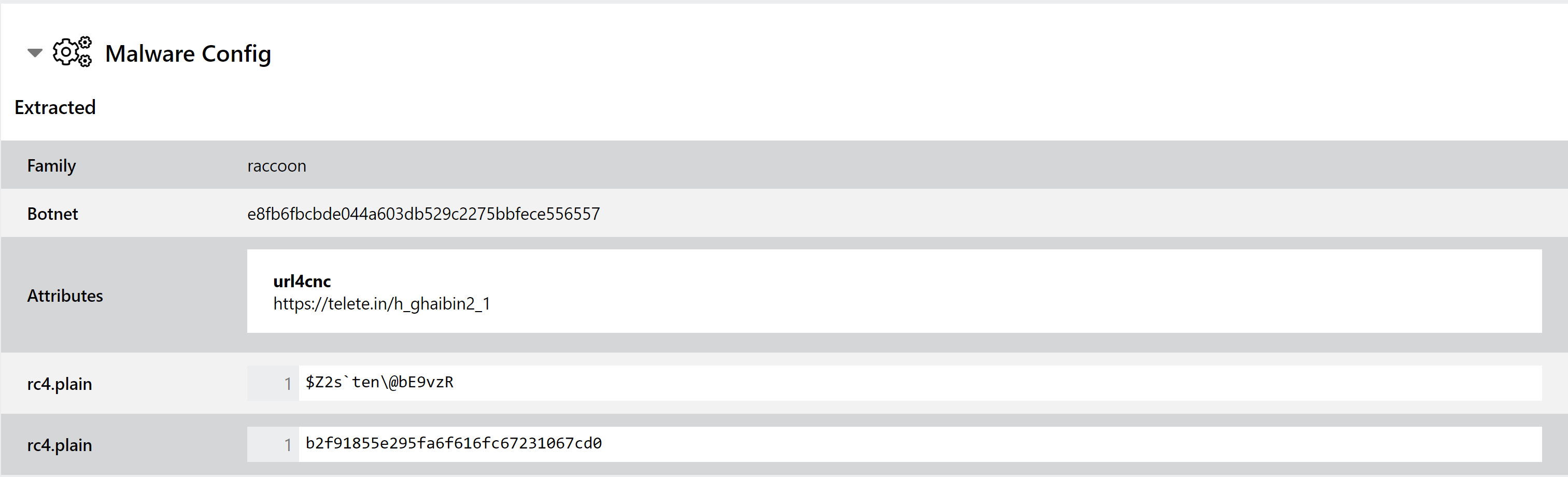
Triage has supported the family with both standard signatures and a configuration extractor for some time. However we’ve noticed a few samples slipping through lately, so this weeks sees a small update to the extractor to more reliably detect Raccoon samples.
Analyses:
Tweaked Redline Stealer Family Signatures
Redline stealer is an infostealer which is currently extremely common in wild. It has appeared on this blog fairly regularly since we added support for it, as it is very actively developed and constantly releases new versions with tweaks which sometimes prevent our extractor from correctly parsing the configuration data.
This week we noticed a version with a slightly different SOAPAction network event, so we have made some minor changes in the background to ensure that these are properly supported.
Analysis:
