We’ve got a lot going on this week so this is going to be a fairly short Triage Thursday entry. We still have a couple of new things we want to share with you though which have been released on Triage in the last week.
We’ll be back with a more changes next week. In the meantime if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
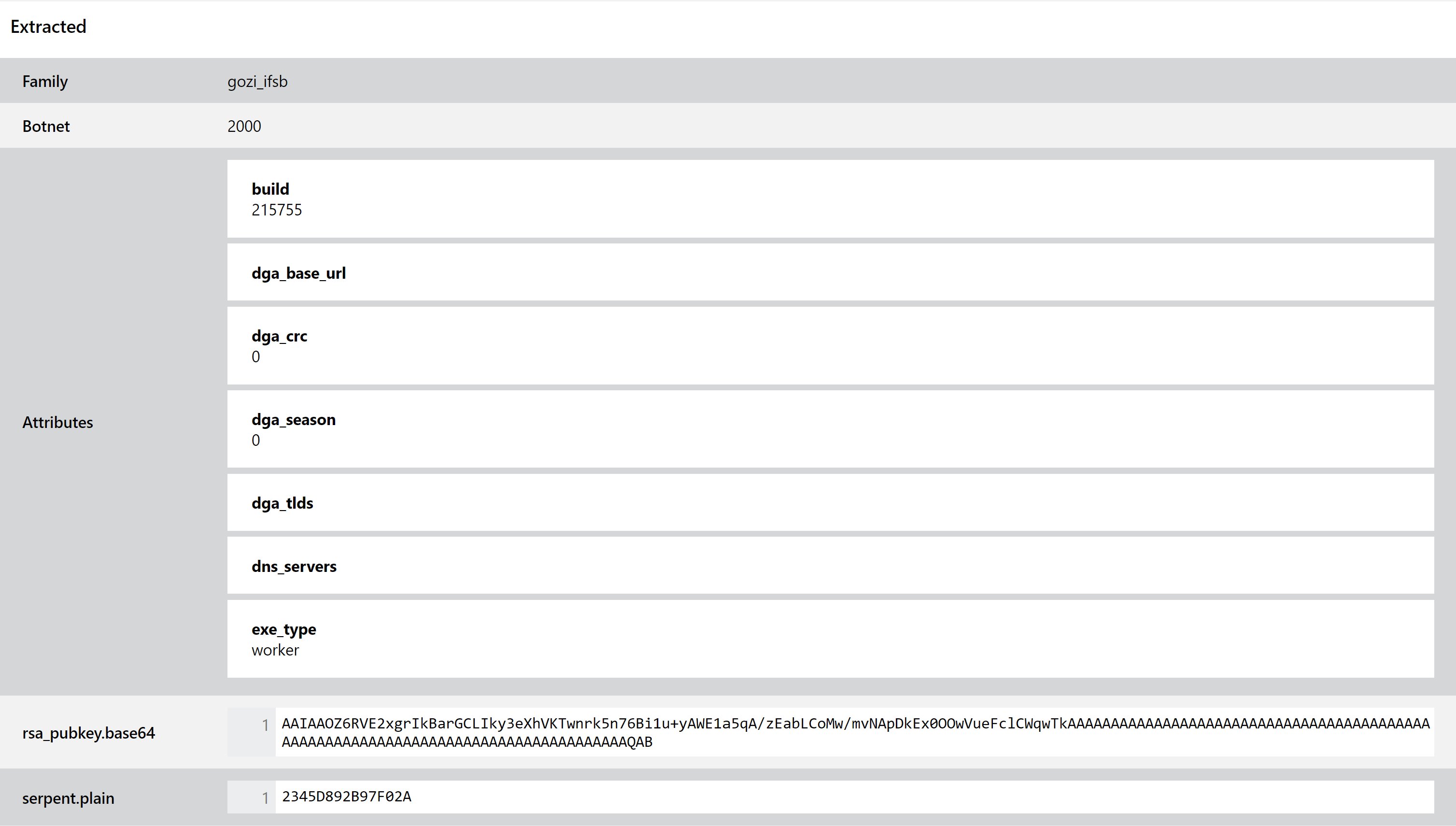
Updated Gozi Family Detection
We recently began to review the Gozi family and published the first round of updates. We’ve been continuing to look at samples and tweak the detections to ensure Triage can identify the family reliably, and this week we are publishing some more changes to this effect.
We have also updated the configuration extractor to include the sample’s Build Number and exe_type in the output, to help analysts identify and track new versions or identify if it is a loader or worker based on previous research
Analyses:
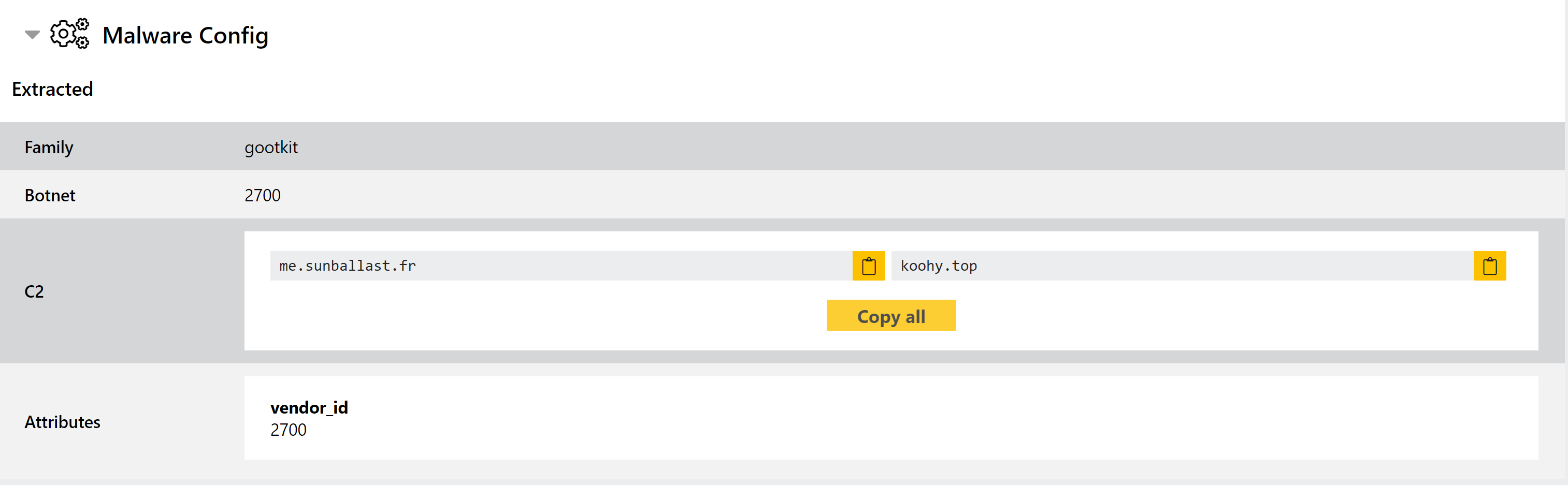
New Gootkit Configuration Extractor
Gootkit is a banking trojan which has been used in the wild since 2014. It includes a wide range of features targeting financial information stored on or accessed through infected machines, including remote access, keylogging, video and screenshot capture, and theft of locally stored data and credentials.
This week we have reviewed samples and updated our detection to better support the family, as well as implementing a new configuration extractor to dump relevant C2 and
Analyses:
