Welcome to another entry in our Triage Thursday blog series, where we go over the main updates and detection changes in the previous week. We’ll be keeping it fairly brief today, but will cover some background on the main additions.
In the news today:
- Added signatures for new Azov ransomware
- Added signatures for Screencap keylogger
- Added signatures and configuration extractor for Ratmilad Android spyware
- Updates for Emotet configuration extraction to handle garbage instructions included in latest versions, and the new IP/port number format
- Updates for Qakbot to handle new C2 list format
- Updates for Raccoon stealer to detect recent samples
- Added fallback rules for Redline stealer to detect recent samples where obfuscation prevents extraction
- Updates for AgentTesla to properly extract credentials from recent samples
As always you can contact us any time directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Azov Ransomware
Towards the end of October a new family was seen in the wild being distributed by the Smokeloader family. Dubbed Azov due to its references and supposed opposition to the Russian occupation of Crimea (‘supposed’ as there appears to be no real activist justification for the targets affected), it was originally identified as ransomware but subsequent analysis has shown that it is in fact effectively a file wiper with no way to recover the locked data.
According to the alert published by NJCCIC and analysis by BinaryDefense the samples will encrypt all files on disk which do not have the .exe, .dll, or .ini extensions, processing them in chunks of 666 bytes at a time. However there is no decryption key and the attackers cannot be contacted to negotiate a ransom or any file recovery.
According to BinaryDefense the files were also configured to only begin encryption after a specific time on October 27th 2022, and include a file infector component which backdoors all executables on the system. This means the ransomware will be run any time a user or process launches one of those files.
Analyses:
ScreenCap Keylogger
In October SentinelOne reported on a new Chinese APT that had begun launching campaigns against telecommunications and IT service providers in the Middle East and Asia. The group - assigned the identifier WIP19 - has been using a stolen digital signature to sign their malware samples and help them bypass detections, with a few different tools being identified by SentinelOne’s research.
One of these new tools is a keylogger called ScreenCap which has was observed being deployed in a slightly unusual way. Using a rarely exploited but previously known quirk of Windows, the attackers can drop the DLL to the c:\windows\linkinfo.dll path and the Explorer process will load it the next time it launches. To activate the functionality the attackers can manually restart explorer.exe to trigger the loading process.
The malware carries out both keylogging and screen capture functions:
- The keylogging mainly targets browsers, detecting a running instance of Internet Explorer, Chrome or Opera and recording all input to a local file.
- The screen recording aspect will capture the user’s screen as a video file and store it locally, again with the aim of using it to extract useful credentials etc.
SentinelOne reports that the family is often very targeted with clear indications of the intended recipient included in the binaries. It seems that it is used manually as part of a larger infection chain.
We have taken a look at the available sample and implemented initial detections.
Analysis:
Ratmilad Android Spyware
Ratmilad was reported by Zimperium labs in early October, having been seen targeting Android devices in the Middle East. It is distributed via direct APK downloads and has not been spotted on any appstores, with download links distributed via social media and messaging apps.
The payloads reported by Zimperium have been concealed as apps supposedly intended to spoof mobile phone numbers to help with verifying social media accounts. They require the user to grant very extensive permissions on the device, and once enabled the app will sideload the Ratmilad spyware.
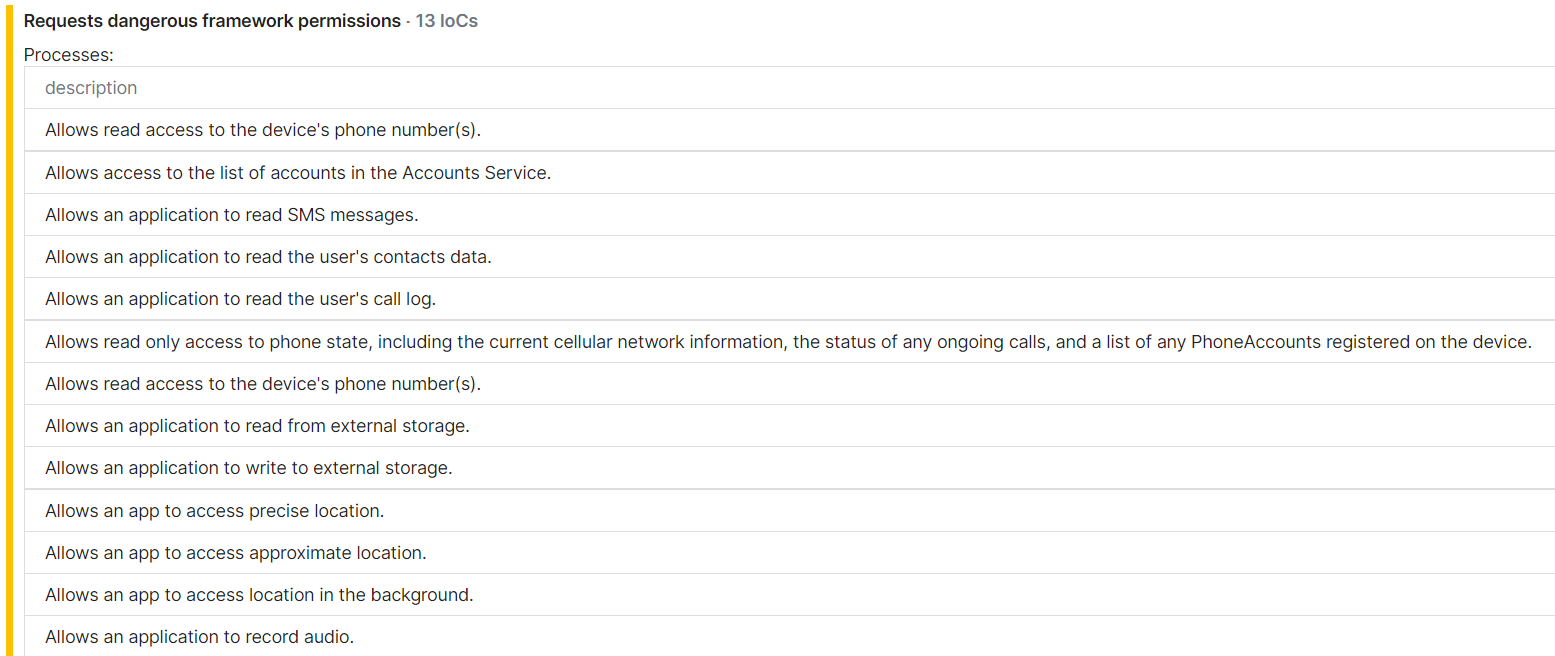
According to Zimperium’s report the app can access the following data once fully installed:
- Device MAC address
- Contact list
- Text messages
- Call logs
- Account names and permissions
- Clipboard data
- GPS location data
- SIM information – mobile number, registered country, IMEI, and SIM state
- File list
- List of the installed applications, along with their permissions
- Device hardware information – model, brand, buildID, Android version, and manufacturer
It can also:
- Read, write, and delete files
- Record sound
- Upload files to C2
- Modify application permissions.
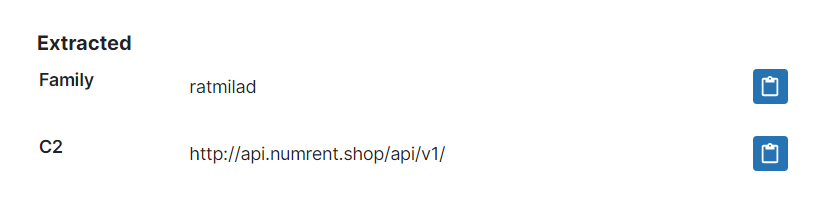
Based on the public sample we were able to acquire we have implemented detection and a configuration extractor to dump C2 for the family, and will update further if needed.
Analysis:
