Welcome back to our Triage Thursday blog series! We’ve had a bit of a hiatus lately due to time constraints making it hard to get these blogs out but rest assured that the updates have been flowing nonetheless. We’ll summarise some of the more notable ones here along with this week’s updates.
Going forwards we’ll be doing our best to keep to our weekly schedule for the update blogs but for at least a while things might continue to be a bit irregular. Either way keep that feedback coming in, and we’ll be continuing to push out new updates in the background!
In the news this week:
- Fixes, updates and refactoring for Ramnit
- Updated Lokibot configuration extractor
- Small fixes for CryptBot v1 configuration extractor and updates for v2
- Fixes to avoid Masslogger and Zloader false-positives
- New signatures for Meow ransomware
- New signatures for Beatdrop downloader
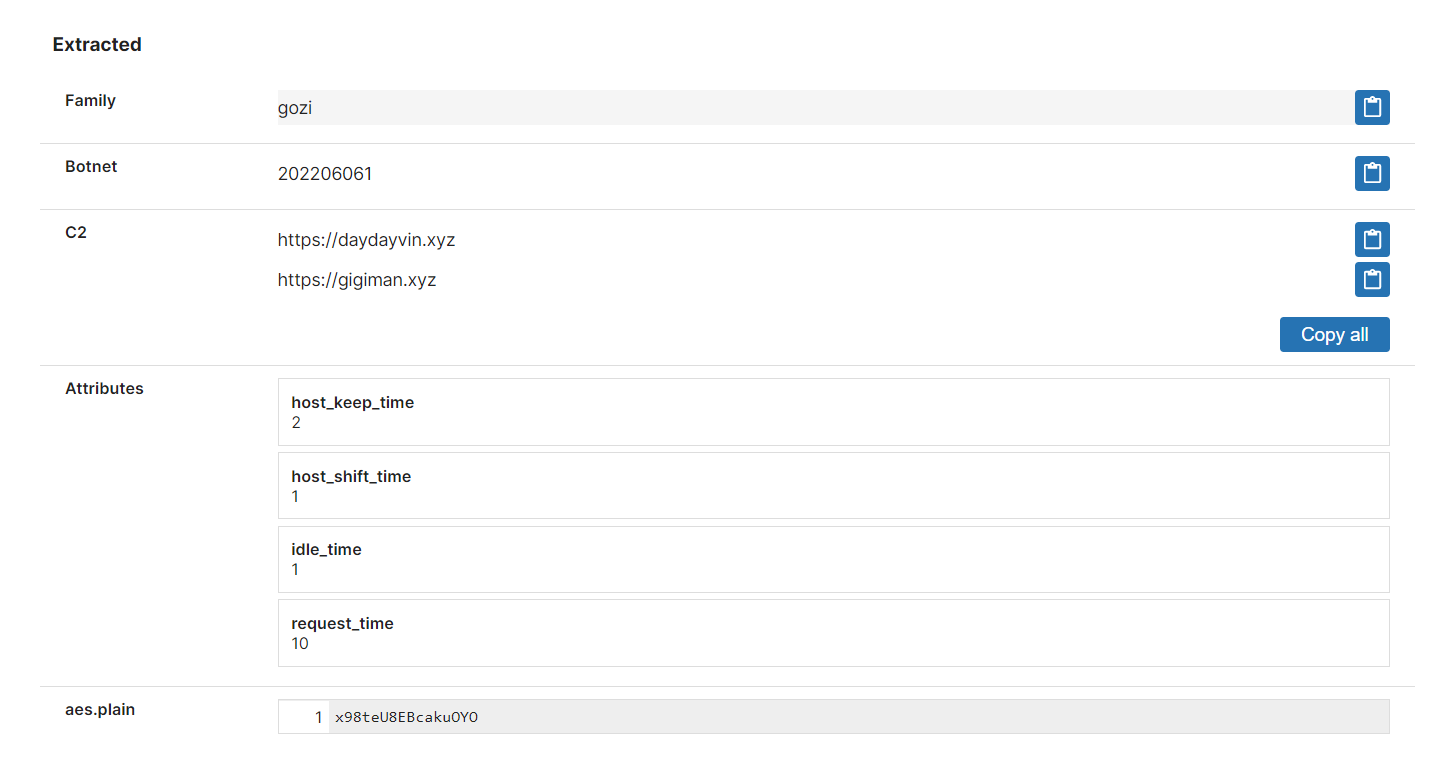
- New signatures and configuration extractor for new Gozi LDR4 variant
- New signatures and configuration extractor for Furball Android spyware
On top of the most recent updates, the following have been deployed over the last couple of weeks where we didn’t release a blogpost:
- Added support for Quantum ransomware
- Added support for Prestige ransomware
- Added signatures and configuration extraction for DarkCloud stealer
- Added signatures and configuration extraction for BruteRatel C2 framework
- Added signatures and configuration extraction for Rekoobe Linux trojan
- Updated Qakbot detections to handle new variant of its string decryption algorithm
- Updated Oski configuration extractor to avoid garbage C2 output
- Added new configuration extractor for CrimsonRAT
- Added signatures for Lgoogloader
- Added signatures for Mafiaware666 ransomware
- Added signatures for Harly Android trojan
As always you can contact us any time directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Meow Ransomware
Meow is a new ransomware family that has popped up in October 2022, reported online by a few researchers. It appears to be a new variant of the Conti family using many of the same techniques.
It does not seem to have any relation to the 2020 wiper attacks that also became known as Meow.
The samples have pretty distinctive behaviour so we have implemented some rules and made sure the ransomnote is properly dumped wherever available.
Analysis:
Beatdrop Downloader
BeatDrop first appeared in early 2022, reported by Mandiant as part of an investigation into the activity of the APT29 threat group. It is a malware downloader that is distributed via email phishing campaigns with an apparent focus on government/diplomatic entities.
Many of the lures observed are based around fake administrative notices related to certain embassies, and compromised email accounts are used to make the emails look more trustworthy.
The main interesting feature of the family is the fact that it uses Trello as its C2 infrastructure - this is done via the service’s API. Data is logged to boards, and these can also be queried to make sure that the infected organisation is not already compromised.
We have added static detection for the family, and may revisit it in future if it continues to show up in our analyses.
Analyses:
Gozi LDR4
The Gozi family - often called Ursnif - is a messy collection of variants and forks which are regularly updated by a wide variety of developers and threat actors. These range from close forks with strong similarities, to more distant variations like RM3 with much more significant changes. As such trying to keep track of the various branches of the family tree can be quite tricky in itself.
This week we’re adding support for yet another variant of this family which has become known as LDR4. This was reported on earlier this month by Mandiant. We’ve long had configuration extractors for Gozi and these have now been updated for this variant, along with our other detections.
We’ve also made the decision to refactor the way we define the different variants in an attempt to make our tags more useful for automation - going forwards instead of having entirely separate family names for each variant all samples will be identified as simply Gozi, and then behavioural tags will be applied to give detail on the exact version. For anyone harvesting the data automatically this will mean you just need to filter for the Gozi family name rather than all the different options.
Analyses:
Furball Android Spyware
Furball is used as part of a long term mass surveillance campaign called Domestic Kitty that goes back to at least 2016. The malware itself has seen a few versions over time, and seems to be solely used by the APT-C-50 threat group and developed on top of the commercial stalkerware ‘KidLogger’.
The surveillance campaign is directed against users in Iran, distributed via fake websites mimicking legitimate resources for Farsi-speakers. Depending on the exact version the family has a range of functionality options:
- Access clipboard contents
- Read device location
- Access SMS messages
- Steal contact list
- View call logs
- Record calls
- Read the content of notifications
- List installed and running apps
- Harvest device information
Furball came to our attention after a recent update brought out a new version that gained some attention online. According to ESET the latest version only requests access to contacts via the app permissions so it cannot access the full list of features above, but it’s unclear if that’s just due to it only being part of the overall infection or if it’s just a change to reduce detection. This latest update does generally seem to have focused on stealth with a new obfuscation layer to make static detection harder.
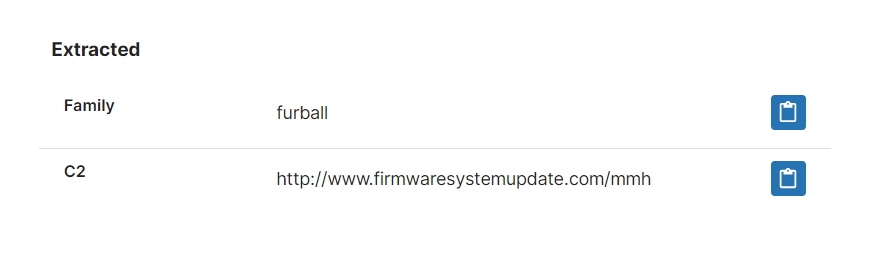
We have added basic detections and a configuration extractor which can dump the C2 information from the samples.
Analyses:
