Welcome back to our Triage Thursday blog series, where we go over the updates deployed over the last week. In the news today:
- Fixed Buer extractor to work with latest samples
- Added configuration extractor for Kutaki stealer
- New signatures for SessionManager backdoor
- New signatures for OrBit Linux backdoor
- New detections and configuration extractor for Joker Android banker
- New detections and configuration extractor for Bahamut Android spyware
If you have any feedback, questions or issues about Triage feel free to reach out to us any time - we do our best to respond to all feedback but even if we can’t get back to you straight away your files will go into our list of things to review and help us prioritise tasks. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Buer
Buer is a loader framework which was first seen in late 2019. It is operated on a malware-as-a-service model, with the developers selling it to others for use instead of deploying it for operations themselves. It has been seen dropping a wide variety of other families including Trickbot, BazarBackdoor, Ryuk ransomware, and CobaltStrike beacons.
The original version was written in C, and in 2021 a variant was found which used the Rust language instead (and was this named RustyBuer).
The family is quite popular and has seen several changes since its discovery. We have made some tweaks in the past but we have recently started seeing some samples which were not being properly handled by our configuration extractor. We have now made some improvements to handling at the static phase but there is still an issue with results at the behavioural stage - we should have a fix out for that shortly.
Analyses:
Kutaki
Kutaki is a stealer which mainly targets acquisition of data from infected systems through keylogging; clipboard harvesting; and recording from webcams, microphones and screens. In some cases it has also been seen dropping secondary utilities like SecurityXploded’s BrowserPasswordDump to augment its own native capabilities.
It features a number of anti-VM and anti-analysis techniques but these appear to have been taken from blogposts dating back to 2010-11, meaning that they are now very much out of date. They can still be effective for simple analysis but are easily bypassed by most modern tools (including Triage of course!).
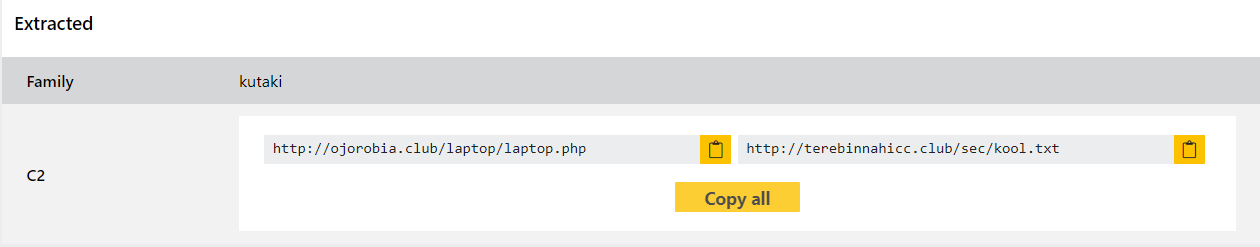
Triage has had detection for Kutaki since August 2020 but we’ve revisited it this week to add a configuration extractor which can dump the C2 domains/URLs.
Analyses:
SessionManager
SessionManager is a backdoor which targets Microsoft IIS - it is deployed as an addon module and enables attackers to maintain persistent and stealthy access to compromised infrastructure. This kind of approach can be quite effective as the module has access to the standard web traffic being handled as part of the server’s normal operations, and can trigger actions based on commands which look like totally benign traffic but are actually carefully crafted. Without prior knowledge of the format it’s very hard to detect these as unusual.
The malware can perform file actions on the compromised system, download and execute additional binaries from its C2, and connect to other network devices for data collection and propagation.
Since it requires an IIS instance examples of this family will not work properly in an environment like Triage, so we have added some static detection rules to identify it without relying on behavioural actions. Some example files are shown below.
Analyses:
OrBit
OrBit is a newly discovered Linux backdoor that was first reported by Intezer earlier this month. According to their report it includes quite advanced evasion techniques, effectively working like a rootkit to hook certain APIs and hide any sign of the malware’s presence on the machine. It tracks the group identifier (GID) for all resources related to OrBit and inserts a hook which looks that up any time a function is called - if anything else tries to access a known GID directly or indirectly it will intercept and alter the function response to prevent discovery.
In terms of functionality it can provide full remote access via SSH, harvest credentials stored in local files, and log TTY commands. It directly infects all running processes to make removal difficult.
As a new threat we have only identified a couple of samples so far but have built out static detections based on these. We will continue to monitor the family and will update if needed as more samples become available.
Analyses:
Joker
Joker has been around in various forms since 2017, hiding in applications which appear to be legitimate downloads and are often listed on the Google Play Store.
It has something of a dual role, performing actions related to both data theft and click/billing fraud. The exact capabilities vary from app to app but in some cases it has been seen directly uploading contact lists and device information to its C2 infrastructure, and can also be used to download and deploy additional payloads. Its main function though is to carry out fraud by subscribing the infected device to various paid services or calling/texting premium numbers which are controlled by the attacker - this can be quite effective as many users will not notice anything amiss until they receive their phone bill at the end of the month.
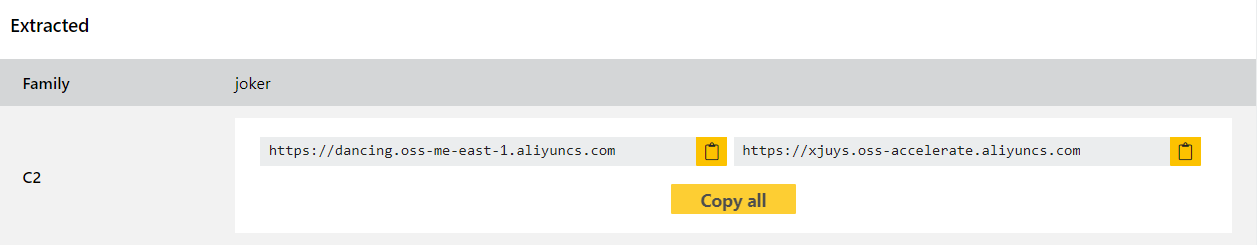
Despite being one of the older Android threats it is still widely used so we have added some behavioural and static detections for the family with this update along with a configuration extractor.
Analyses:
Bahamut
Bahamut is technically an Advanced Persistent Threat (APT) group but in this case we’re referring specifically to their Android spyware implant which was reported on by Cyble back in August 2021. It recently came back into the news with additional updates and a new attack pattern, now being delivered via carefully crafted phishing websites instead of relying on Google Play.
The other differences with this new version mainly come down to additional targets for data theft - according to Cyble’s post from June 2022 the new version now goes after content from various messaging applications where the original was only exfiltrating metadata like contacts, SMS data and call logs.
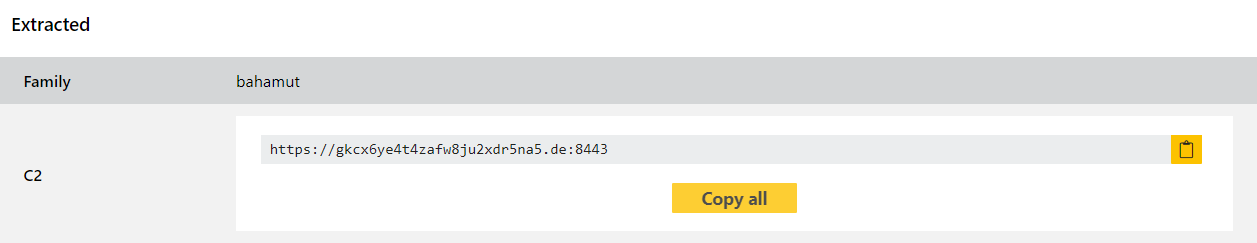
We have reviewed available samples and built standard detections and a configuration extractor which can dump the C2 domain/URL.
Analyses:
