Welcome back to our Triage Thursday blog series! Today we’ve just got a quick one to go over a few detection updates, so let’s get straight into things:
- Updated Qakbot extractor to handle latest samples
- Updated BumbleBee configuration extractor
- Added detections for recent Gh0stRAT
- Updated Redline extractor to improve coverage
As usual if you have any comments, suggestions or other feedback about Triage feel free to get in touch with us. You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Qakbot
Qakbot is an infostealer and trojan which goes all the way back to 2009, and has seen many different versions over the years. We’ve featured it many times on this blog over time so we won’t go into detail again here, but if you’d like more information about the family you can find a report on it from CISA here.
This week’s update for the family is fairly small, but widens support for our configuration extractor - we’d recently noticed some samples with new resource IDs that were causing some issues. This has now been fixed so you should see better coverage for the family.
Analyses:
BumbleBee
BumbleBee is a loader generally associated with the EXOTIC LILY Initial Access Group, who have often worked with ransomware gangs like Conti to provide already-compromised systems for them to infect.
It is a fairly typical loader - it uses WMI to harvest general information about the system and reports that back to the C2, which can issue it a task for the next stage. This task can vary but mainly revolve around deploying code and payloads onto the system. For a fuller writeup of the samples you can find a blogpost about it from Google’s Threat Analysis Group here.
The family has changed a few times already since it first appeared and this week brings some more new versions which need a few tweaks to our handling. We noticed some new samples which are now using RC4 encryption to protect their configuration data meaning our existing code wasn’t supporting it - we’ve now taken a look at the way they handle this and replicated it so we support both these and the older, plaintext versions. We have also made some improvements to the way the extractor presents data, with a bit more differentiation between some of the output.
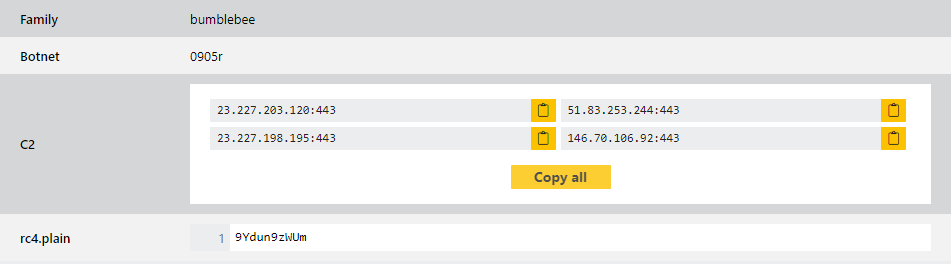
As it’s so active we’ll be keeping a close eye on the family going forwards, and will continue to make changes as needed.
Analyses:
Gh0stRAT
The Gh0stRAT family has a long history, with the core of its code base going all the way back to 2001. However it continues to be relevant today with a bunch of new versions coming out over time, especially with the source code available online.
It is pretty full-featured with a wide range of functionality supported out of the box. Based on a 2015 report this includes:
- Take full control of the remote screen on the infected bot
- Provide real time as well as offline keystroke logging
- Provide live feed of webcam, microphone of infected host
- Download remote binaries on the infected remote host
- Take control of remote shutdown and reboot of host
- Disable infected computer remote pointer and keyboard input
- Enter into shell of remote infected host with full control
- Provide a list of all the active processes
- Clear all existing SSDT of all existing hooks
For more details on Gh0stRAT you can check out the link included above, or a detailed SentinelOne report on it and its background here.
Although it hasn’t come up in the time we’ve been publishing these blogs Triage has supported Gh0stRAT since the platform’s early days. However we have recently seen samples which appear to be a new version with significant enough changes to require some tweaks to our detections so these have now been implemented, and we’ll continue to watch out for any outliers which may need additional tweaks.
Analyses:
Redline
Redline is a stealer family which has seen a lot of activity since it came to prominence in early 2020. Featuring an extensive feature set for data theft and specialised C2 communications, the family has become a popular choice among cybercriminals. It has been observed to be deployed in a number of different ways including sideloading with legitimate applications, masquerading as applications like Telegram, or regular phishing attacks.
This week’s change is not driven by a new variant or version, but is just intended to widen support for some existing samples which were not being properly covered. We have been improving our memory dumping strategies to provide better data for the extractors etc. and this builds on that to make things more stable and robust. We have reprocessed some examples and these are below for reference.
Analyses:
