We’re back with a short blogpost this week for the last Triage Thursday of February. We have 3 detection-related bits of news to cover today:
- Updated Smokeloader Extractor
- New configuration extractor for Amadey
- Updated maldoc handling to bypass new ZLoader anti-VM technique
We’re excited to share some of the larger features we’ve been working on, but for now they need a little more time for the final touches. Watch this space for more news next week!
If you have any feedback on Triage or particular samples please do get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Updated Smokeloader Configuration Extractor
This is Smokeloader’s first appearance in our Triage Thursday blogs for 2021, although we’re sure it won’t be the last (previous time we said that was about Emotet and it got taken down almost immediately afterwards to let’s see if we can curse this one too!).
We first added an extractor for the family back in June last year and continued to push updates to handle the new versions that have appeared since. Earlier this week we noticed that some Smokeloader samples were not being properly handled by our extractor and investigated. It would appear that these samples have changed their decryption routine for C2 communication, removing the original XOR-based function and replacing it with a new system built around RC4.
We have updated our configuration extractor to handle this variant.
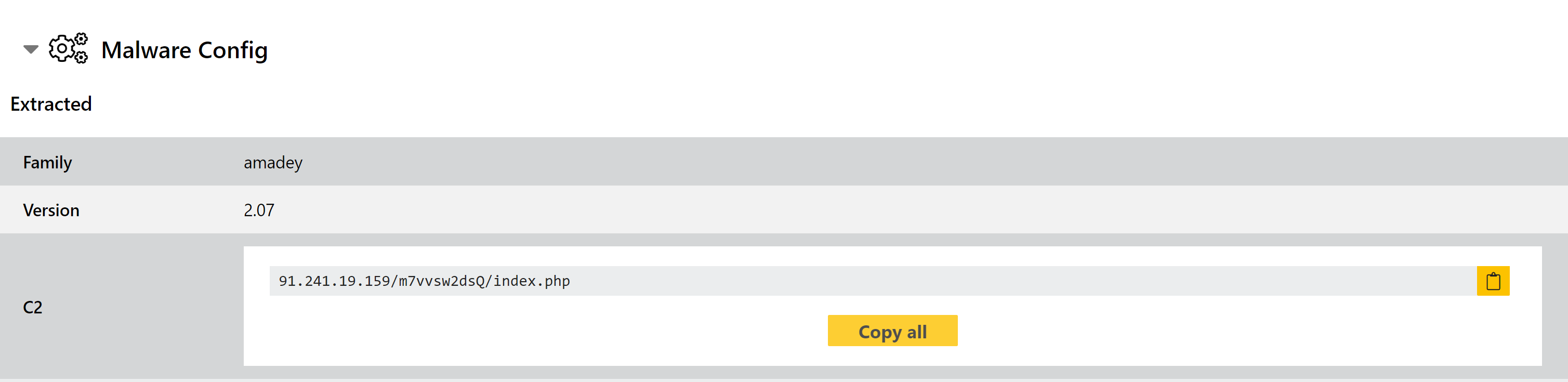
New Amadey Configuration Extractor
Amadey is a trojan and botnet which is available for purchase as malware-as-a-service. Infected machines form a botnet which can be used to further propagate malicious spam emails, carry out DDoS attack, or deploy additional payloads.
Triage has long featured behavioural detection for the family, but this week we have implemented a configuration extractor to complement it and aid with easily tracking C2 and version information across campaigns.
Analyses:
Updated Maldoc Handling to Bypass Anti-VM
Some ZLoader maldocs were recently reported to us which included an anti-VM technique which was successfully detecting the Triage environment. The files were checking for the existence of a Zone.Identifier Alternate Data Stream (ADS) for the original sample file and exiting prematurely if it was not present.
The Zone.Identifier ADS is a feature available on NTFS file systems and is used to ’tag’ files with a trust rating based on their source. However these files area not automatically generated by the filesystem - they are only created by certain events, the most common of which is downloading a file from the internet or an email attachment.
Naturally, as ZLoader is distributed as email attachments the malicious Office doc it is embedded in should always have a Zone.Identifier attached - however this was not the case in Triage where only the file as-submitted was executed.
We have now implemented a fix for this, generating a Zone.Identifier ADS for relevant files before executing them in the virtual machine.
Analysis:
