Since the initial opening of tria.ge to the public, a number of users have got in touch to request extra features. We’ve been listening, and today we’re delighted to announce the release of an experimental ‘Analysis Log View’ in the report UI. This serves as an overview of all interesting actions which have taken place during the analysis, not just those which have resulted in signature matches.
Screenshot of new 'Analysis Log View' UI
This information was already partially available via the API, but this should make it easier to quickly refer to the data.
There is also a search feature within the overview which allows the finding of specific IoCs within the (sometimes quite large) dataset. Every field is searchable, so you can use paths, operation types, process names etc.
This feature is still very much a work-in-progress. We’ll be pushing updates to this over the coming weeks, including things like whitelisting certain actions to remove noise from background processes on the system.
Check out the examples below for a better idea of the information available. We hope you like this update! As usual, feel free to get in touch with us to give us any feedback on this or other aspects of Triage. Follow us on Twitter (@hatching_io) for news on the latest changes as they are released.
Not signed up yet? Head on over to https://tria.ge/ to request early access to the platform!
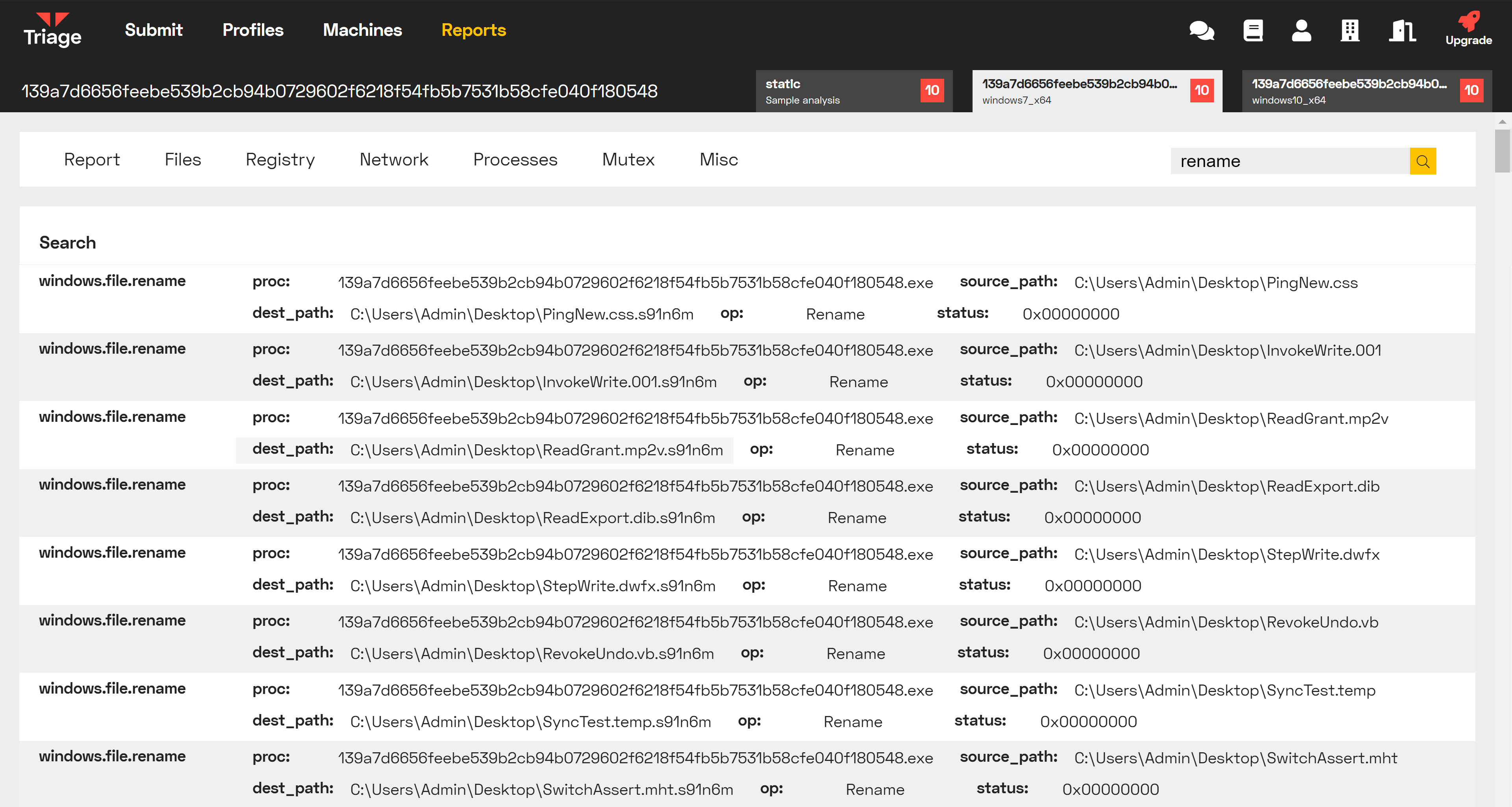
1. Lockbit Ransomware
Lockbit uses a rename operation to add its file extension to files after encrypting them. We can search for this to see only encrypted files, and identify the extension (in the case of Lockbit, this is always .lockbit).
Search for 'rename' showing files encrypted by Lockbit (notice the source/destination paths).
Alternatively, to filter by .txt files in search of ransomnotes:
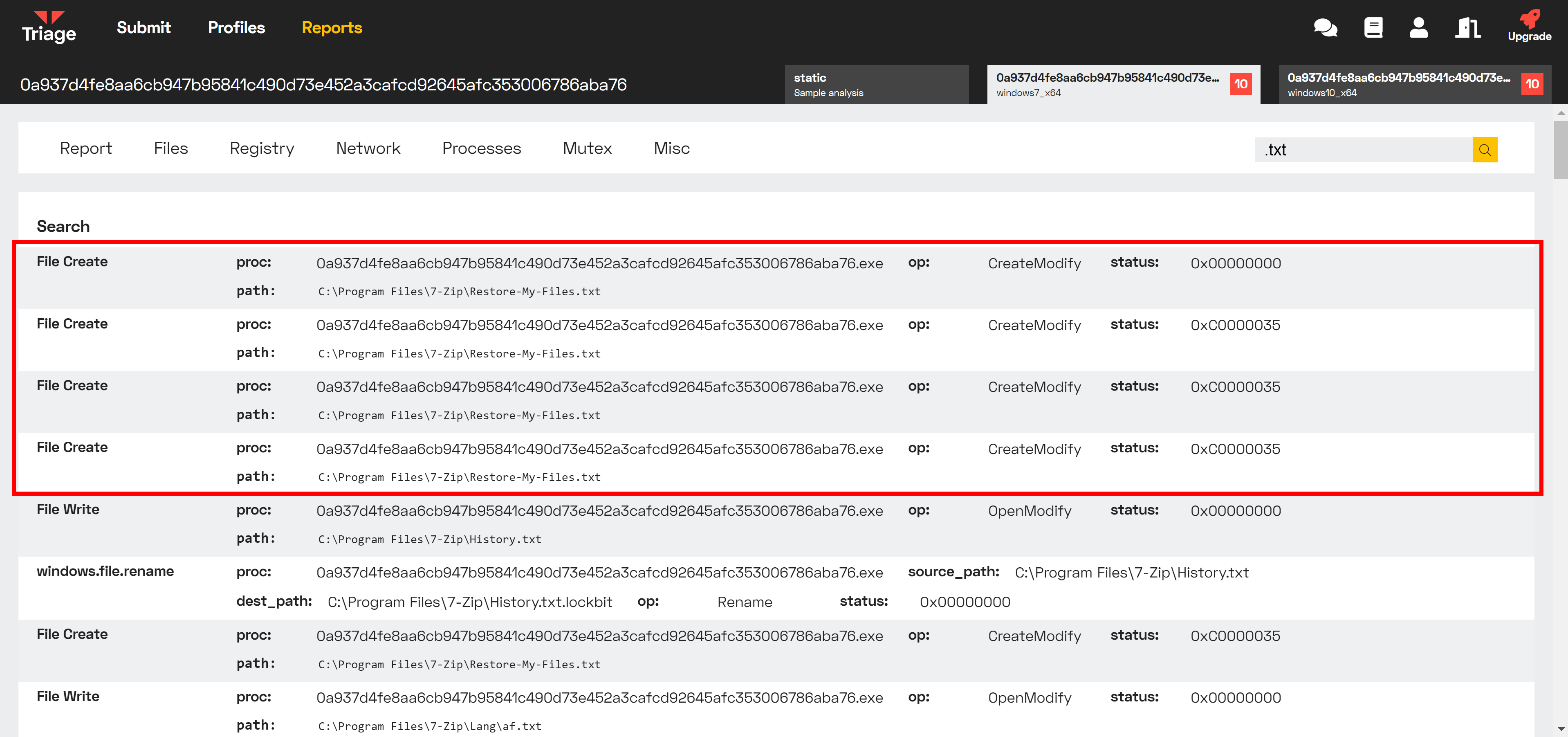
Search for '.txt' showing ransom notes dropped by Lockbit.
2. Remcos RAT
This example clearly shows the mutexes checked/created during the execution of a Remcos RAT sample.
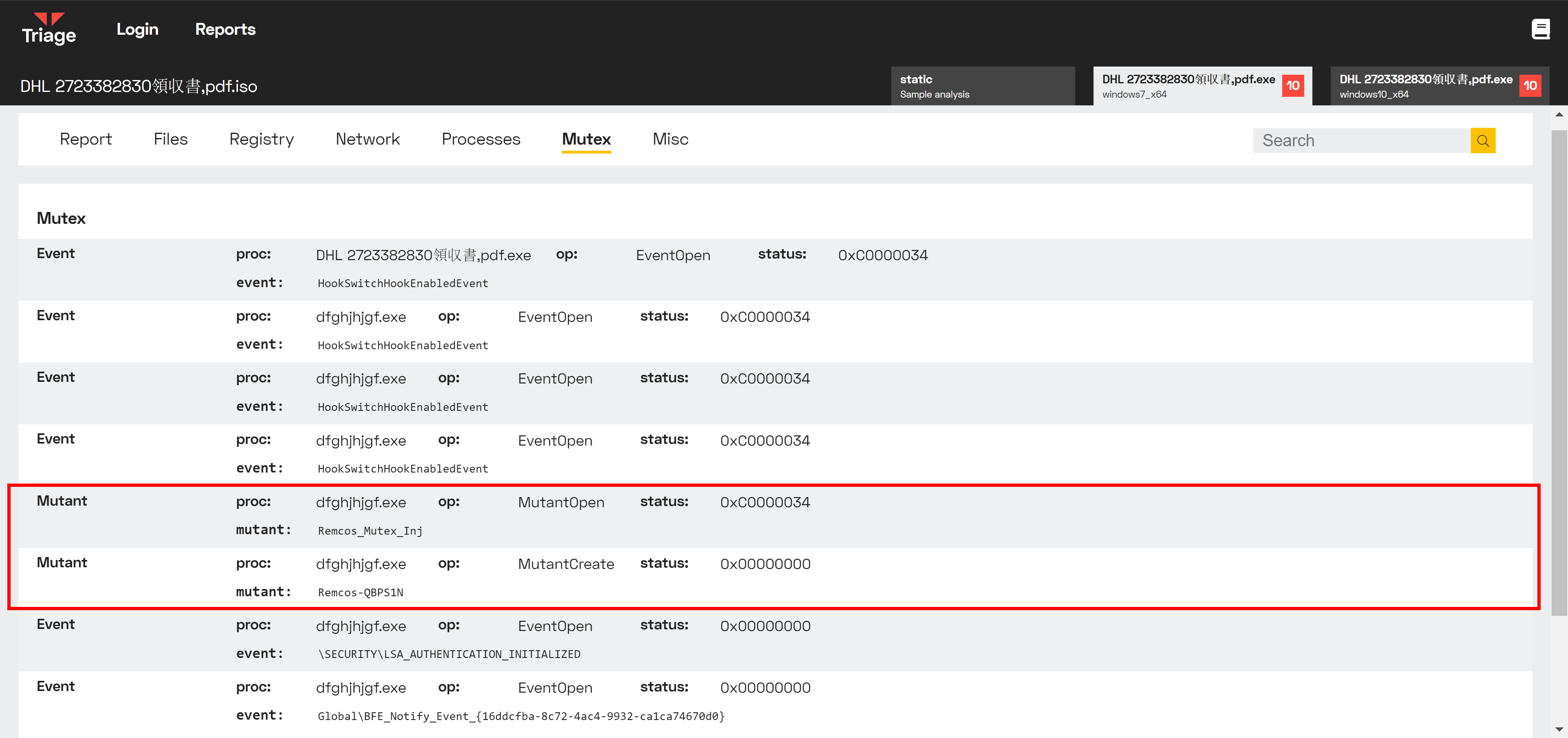
Remcos mutex example.
Signatures report that the sample writes to the Startup directory. This can be verified with a search on the Analysis Log View.
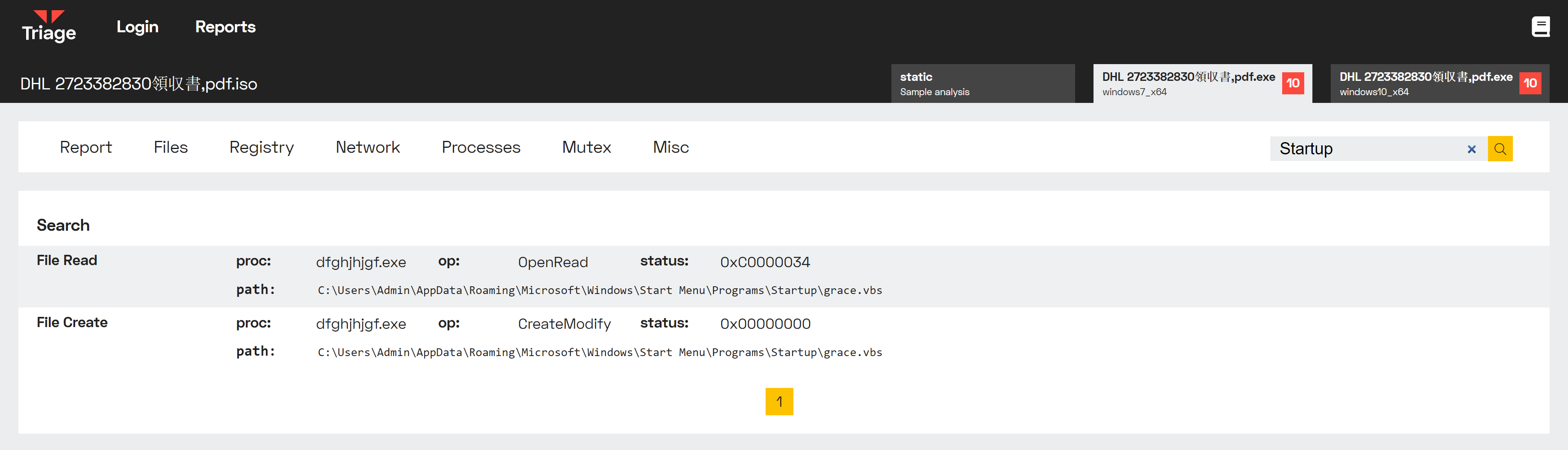
Search for 'Startup' showing relevant file operations.
3. AgentTesla
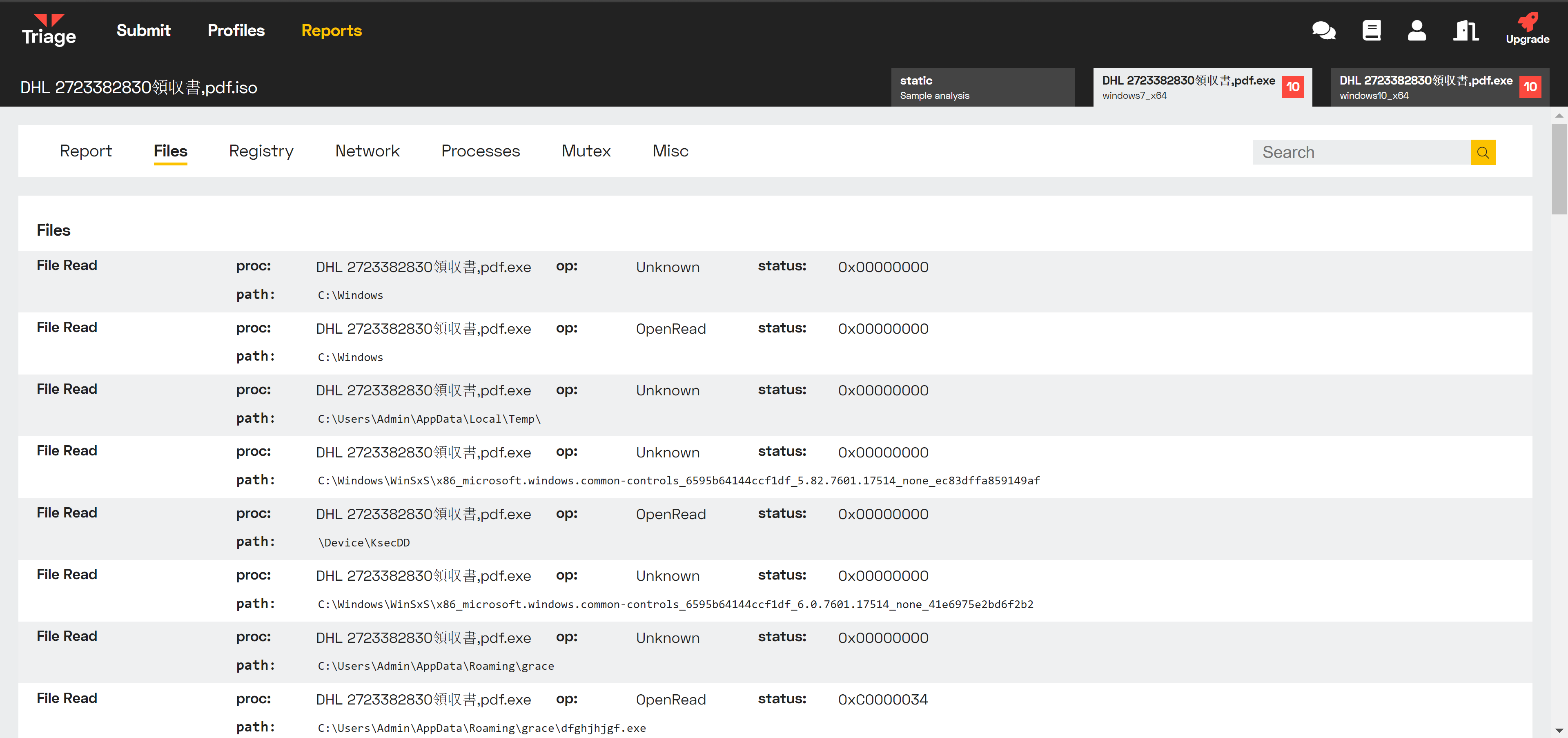
AgentTesla is an infostealer which looks for and exfiltrates user data such as saved browser passwords, FTP credentials, email credentials from local clients, etc.

Search for profiles.ini (common path for browser storage)
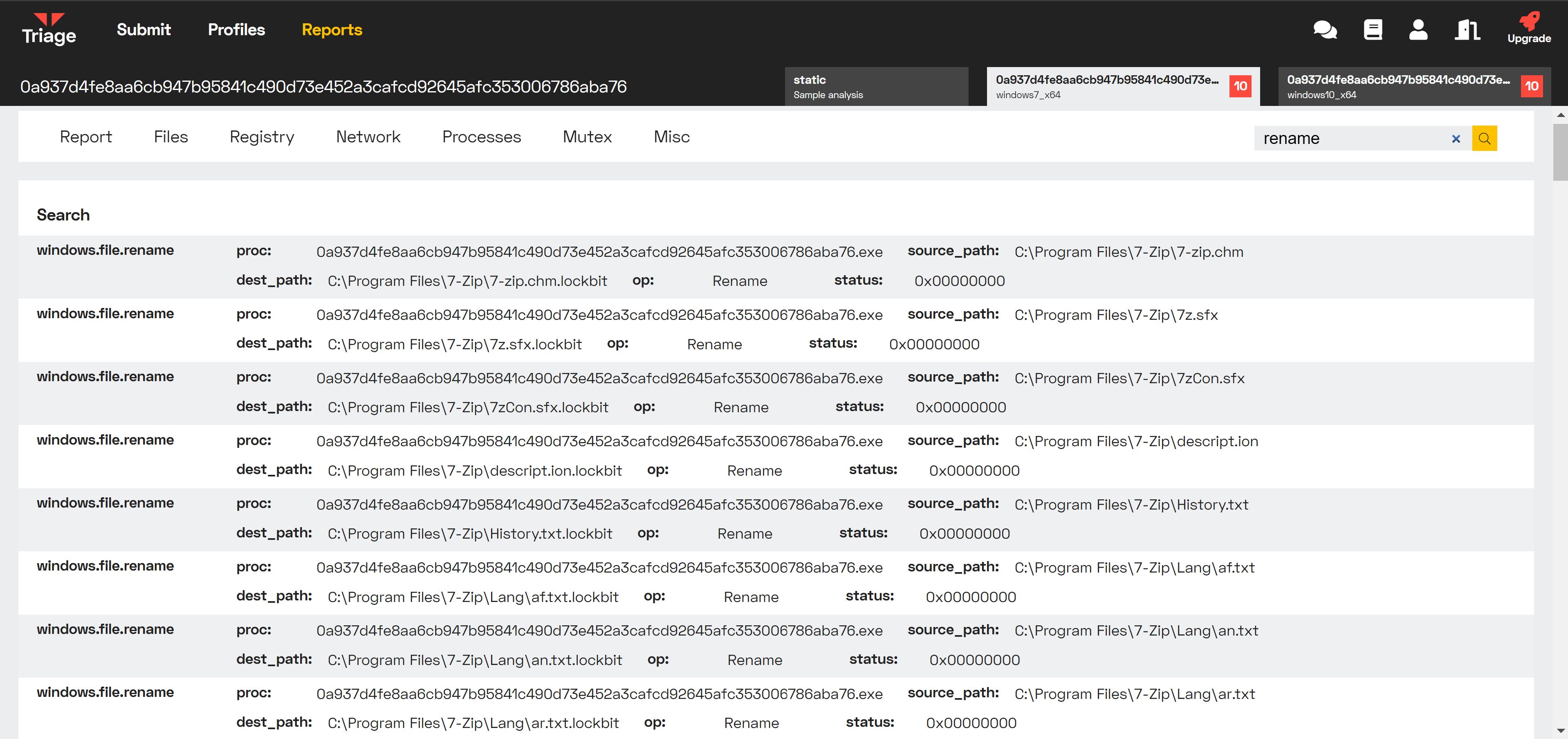
4. Sodinokibi Ransomware
Sodinokibi, also known as REvil or Sodin, contains configuration settings defined by the specific campaign operator. During operation it generally writes a number of these values to the registry for future use as shown here.
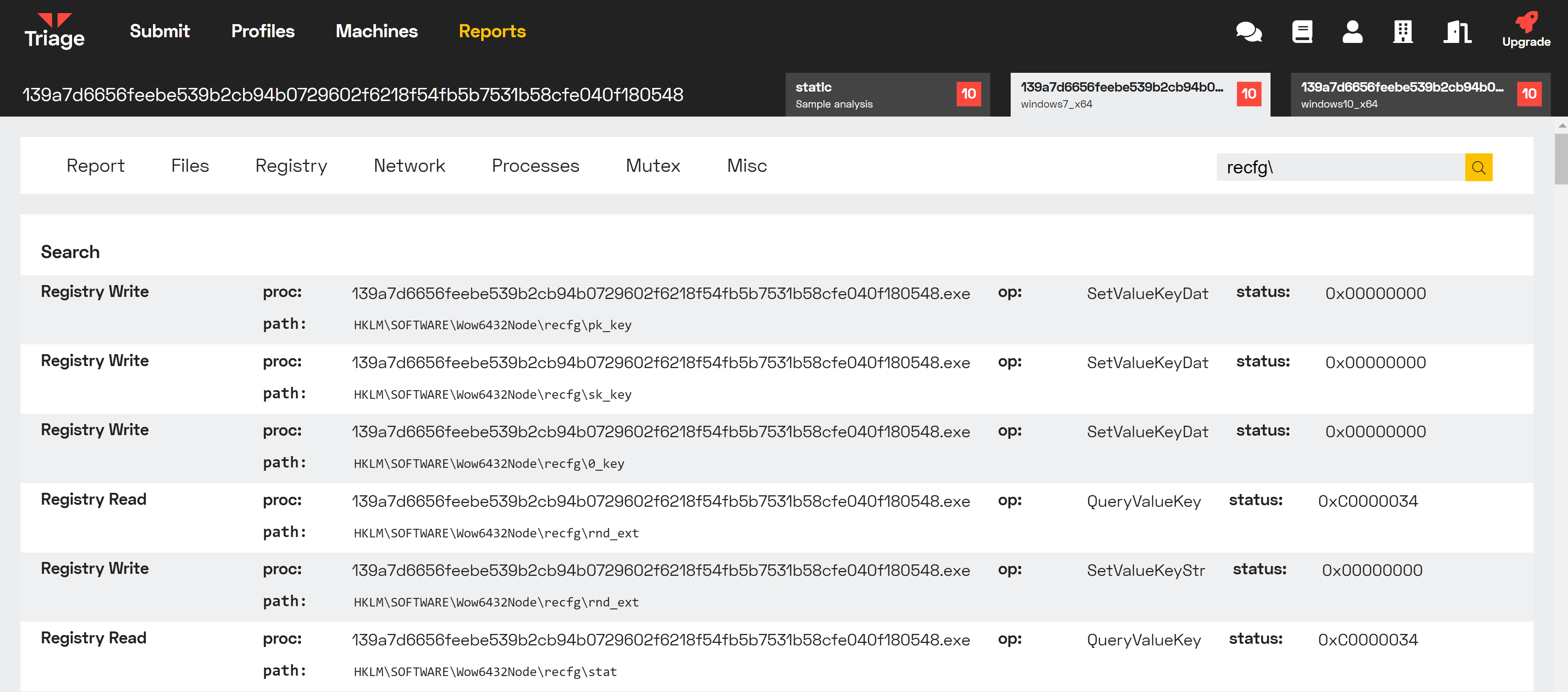
Registry writes for Sodin's configuration settings
Unlike Lockbit, Sodinokibi uses a randomly-generated string as its encrypted file extension. Searching for ‘rename’ actions shows the string created during this analysis.