Welcome back to another Triage Thursday blogpost! In this series we introduce all the new features and updates we’ve added to our Triage sandbox over the past week. As always, if you notice anything that needs attention or have any thoughts you’d like to share with us, please don’t hesitate to reach out. We always appreciate your feedback on how we can improve Triage.
Let’s jump into what’s fresh this week:
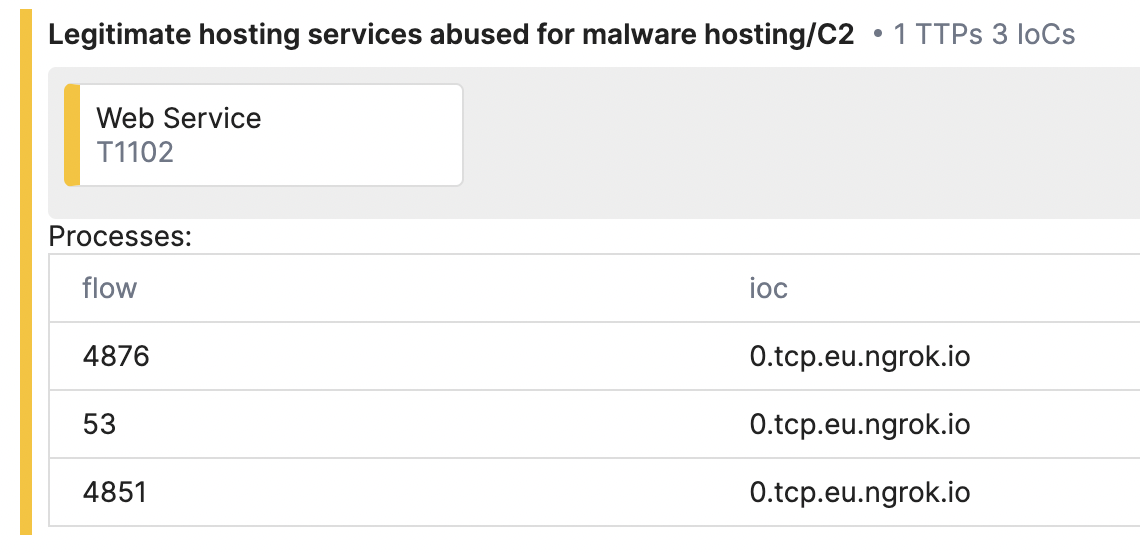
Update for Legitimate hosting services abused for malware hosting/C2 signature
We’ve made a small but helpful update to the signature Legitimate hosting services abused for malware hosting/C2. This change will allow you to easily locate the domains IoCs for this signature and its corresponding network flow in the report. We hope this makes things a bit easier for you!
Next up as usual, here is our weekly update on malware detection and configuration extraction:
New Families This Week
- Added detection and extraction support for Wikiloader family
- Added detection and extraction for DroidSpy Android stalkerware
- Added extraction support to Vidar v7
- Added detection and signature for Drokbk dropper and backdoor
- Updated detection for Raccoon V2 new unextracted variant
- Updated detection rules for Adwind to cover recent undetected sample
Updates for Existing Families
- Updated fallback detection for recent Lumma stealer
- Updated fallback detection for recent Socks5Systemz family
- Updated the ransomnote detection for BlackBasta
If you have any feedback, questions, or issues about Triage feel free to reach out to us any time - we do our best to respond to all feedback but even if we can’t get back to you straight away your files will go into our list of things to review and help us prioritize tasks.
As always feel free to reach out to us any time directly through the website, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
