Happy Thursday! It’s time for another update on the Triage Thursday blog post. As always, we’re here to support you and make the internet a safer place with the help of our lovely Triage Sandbox.
This week, in addition to our usual updates on malware family detection and configuration extraction, we have some exciting news to share. We’ve just launched a new feature called Analysis Logs. You can find it next to the report button in the behavioral section. This feature is a total rework of the old analysis logs view and will help you gain advanced insights into a sample’s runtime behavior.
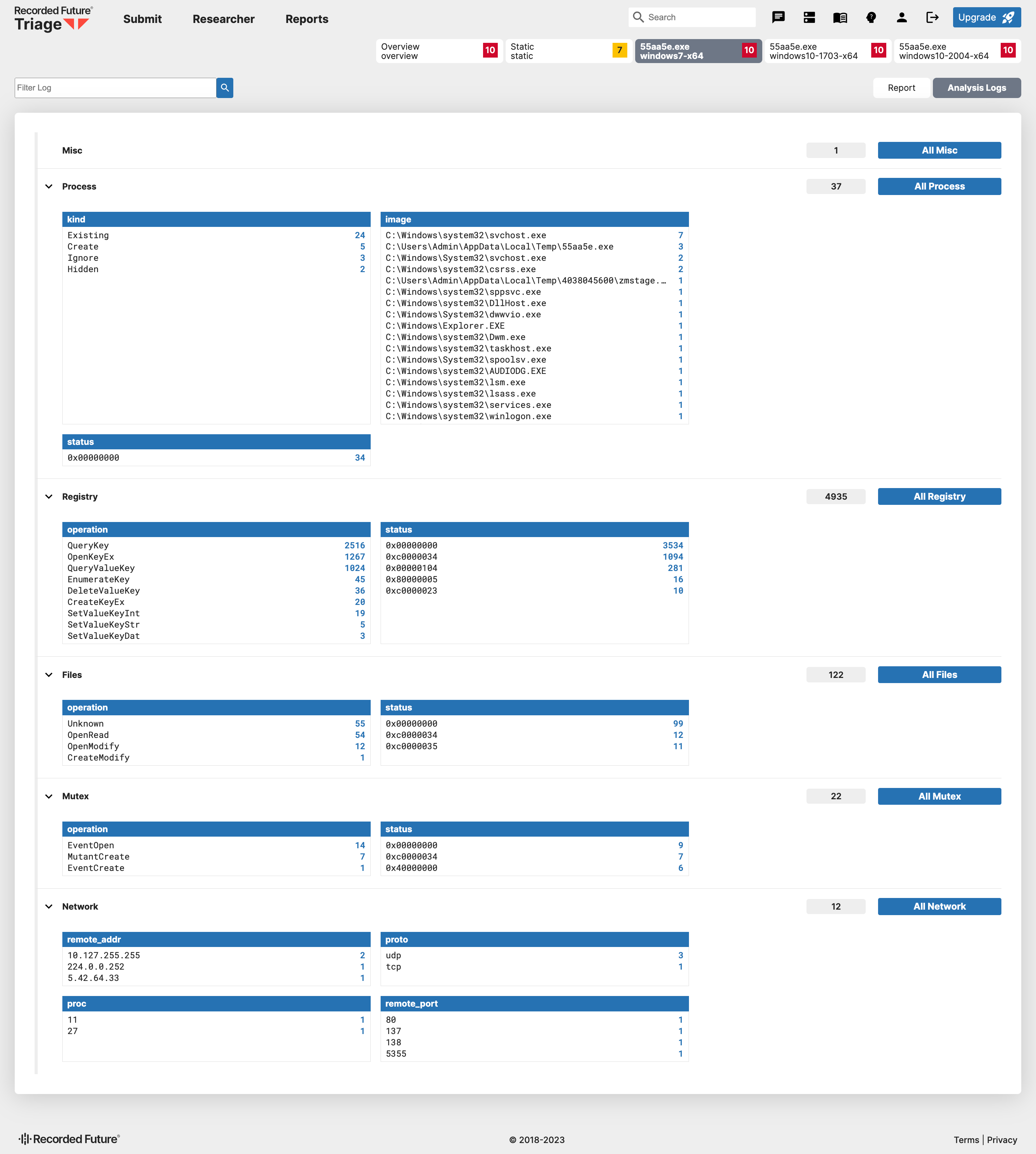
https://tria.ge/230920-rt5nzagg9v/behavioral1/analog
The Analysis Logs provide a handy way to access information about sample runtime details. For example, when a sample is running on a Windows VM, you can observe various types of processes in execution, all kinds of modifications or accesses to registry entries, file operations, mutex operations, and network activities.
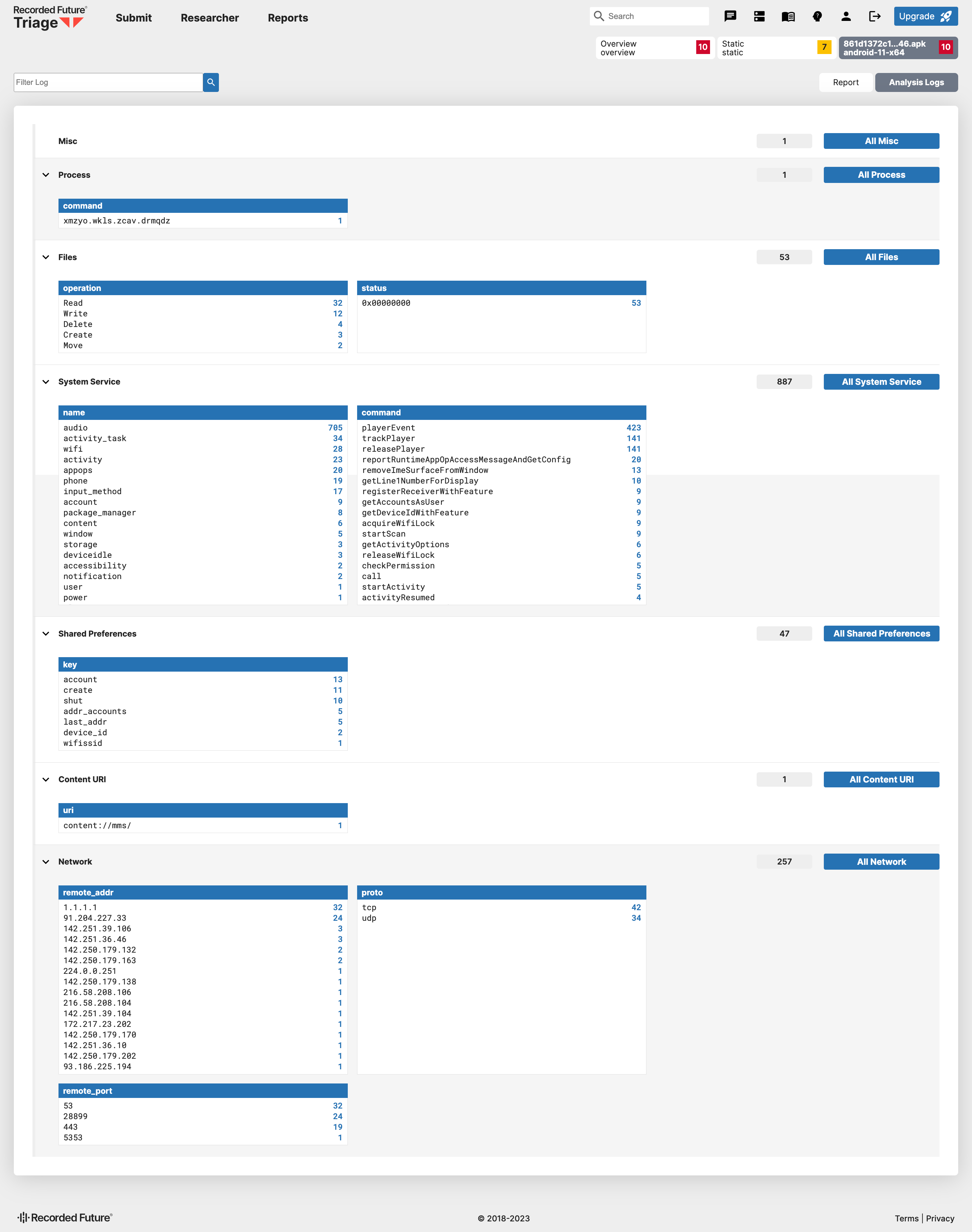
https://tria.ge/230920-rt5nzagg9v/behavioral1/analog
In addition to the information mentioned above, the Android VM’s Analysis Logs also provide Android-related details, such as system services utilized by the application during runtime, the Content URI the application intends to observe, as well as the key value associated with the Shared Preferences.
https://tria.ge/230920-1xj14sch82/behavioral1/analog
If you’re lucky, you might even find a hidden C2 in the Shared Preferences section.

https://tria.ge/230920-1xj14sch82/behavioral1/analog?event=Shared%20Preferences&key=last_addr
To get more information about a specific operation, simply click on any item that you are interested in. You may also use keywords to filter your search by typing them in the search bar at the top of the page. We hope that you find this new feature helpful in your journey to hunt evil.
Moving forward, please find our weekly update below. Stay tuned and enjoy!
New Families This Week
- Added extraction support to Fabookie
- Added detection for SLocker Android malware
- Added detection and signature for Oscorp Android info stealer
- Added signature and rule detection for the Mystic Stealer family
- Added signature and rule detection for the obfuscated Ploutus ATM malware
Updates for Existing Families
- Updated detection and extraction for CustomerLoader for missed samples and avoid FP
- Updated Raccoon V2 detection to extract the latest samples
- Updated signature for Hook Android malware family to cover more undetected samples
- Updated extractor for recent undetected Irata Android malware
- Updated the rule for MetaStealer for undetected samples
- Updated the new variant of Darkgat
- Fixed extractor error with StealC
If you have any feedback, questions, or issues regarding Triage feel free to reach out to us any time - we do our best to respond to all feedback but even if we can’t get back to you straight away your files will go into our list of things to review and help us prioritize tasks.
You can contact us through the website, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
