Welcome to another week of update news in our Triage Thursday blog series! This week we have our normal range of detection updates, but there’s also an exciting new feature we’re finally ready to announce - network simulation. Read on below for the full details on that.
Of course we’ve been busy working on signatures too! Check out the full list of content for today:
- Triage Network Simulation
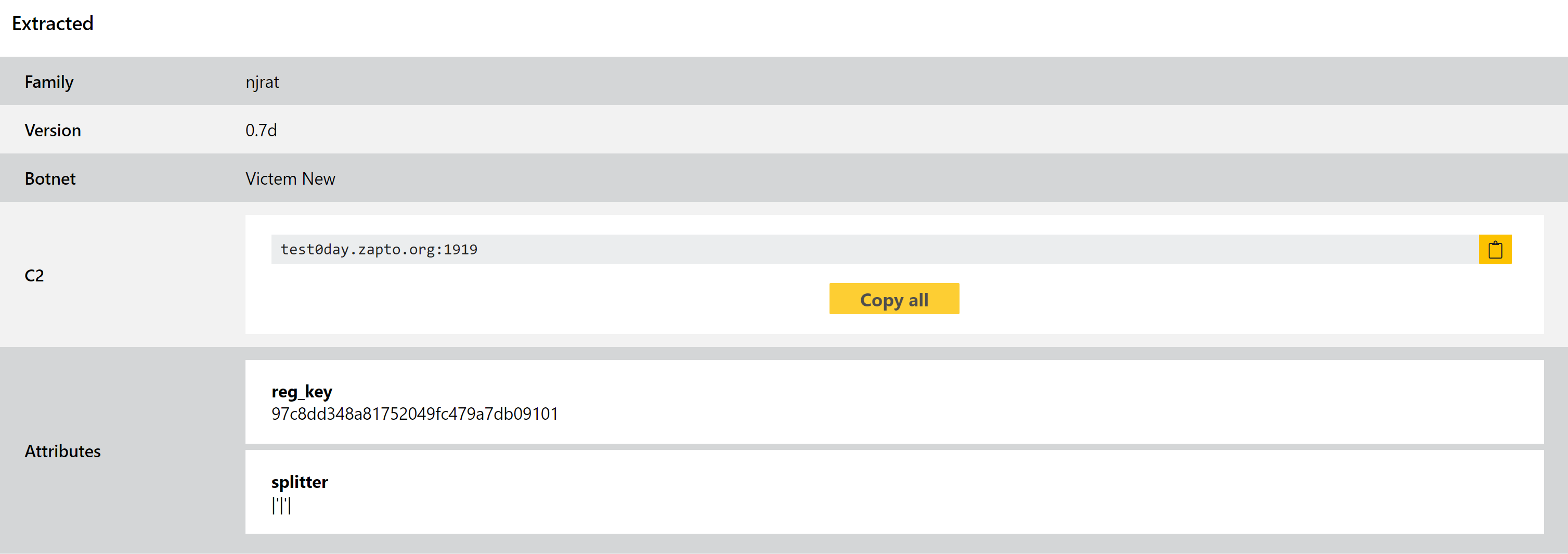
- Added njRAT configuration extractor
- New Backdoor-Machine Stealer family signatures
- ElectroRAT family signatures
- Mercurial Grabber family signatures
- Hive ransomware detection
- Nitro ransomware detection
If you have any feedback or suggestions on Triage itself or individual samples feel free to get in touch! You can reach us directly through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
Triage Network Simulation
Writing these blogposts I use words like “excited” a lot. I’m British, so in reality I don’t get excited very often and when I do it’s just cause for a cup of tea and a quick lie down to think over my disgraceful display of emotion. This week though I can very safely say we’re all excited to be finally announcing the start of our new network simulation feature.
If you’ve been following our roadmap at all you’ll know that we’ve been aiming to add this functionality for some time now, and its turn has come at last. So what exactly is our network simulation all about?
What is it?
If you’ve done a lot of malware analysis yourself you’ll likely have come across tools like INetSim, FakeNet, or ApateDNS which aim to spoof certain network responses in an attempt to trick malware into revealing more of its operations and functionality. For example, if a C2 domain is no longer active thus preventing a sample moving past its initial beacon action, setting up a tool to spoof a 200 OK response and return some fake data matching the expected file type might enable you to convince it to perform additional actions in your virtual machine.
Our new feature works in very much the same way, allowing you to configure fake responses to certain types of HTTP/HTTPS network requests in order to make it appear as though the malware successfully (or unsuccessfully as the case may be) contacted its C2 servers.
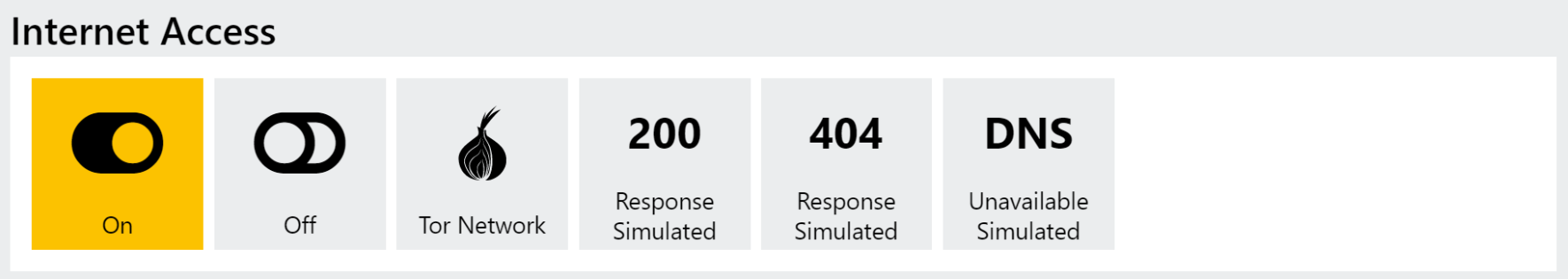
Current State
Today we’ve released the first version of network simulation onto the public cloud, for you to play around with and test out. This initial release is a very basic version of what we’re aiming for over the coming months and weeks, but it forms the initial groundwork in terms of backend support which we’ll be able to add to rapidly.
This version supports 3 main modes of operation:
- 200 Response Simulated: Will return a
200 OKresponse to any HTTP/HTTPS requests - 404 Response Simulated: Will return a
404 Not Foundresponse to any HTTP/HTTPS requests - DNS Unavailable Simulated: Will simulate the failure of all DNS requests as though C2 domains are no longer active. Useful for forcing some families to cycle through their entire configured list of C2 URLs rather than stopping at the first success.
Future Plans
At the moment all of the responses provided are empty/blank, with very generic headers presented in all instances. Besides potentially adding some additional modes of operation, our next major focus will be on filling those with something a bit more useful and relevant.
We are still working out exactly what that looks like, based on initial testing with the feature and discussion with our analysts. If you have any feedback on that side of things too please do feel free to get in touch once you’ve had the chance to try out the existing format. However these expansions will generally revolve around making the system a bit more ‘intelligent’ - e.g. by making it return genuine files of the correct type when specific requests are passed, or providing additional headers etc.
We will likely also be adding support based on the functionality of specific families, for example returning specific timestamps or geoip results.
We hope you’re as excited about this one as we are, and as mentioned feel free to get in touch with any use-cases you’d like to see supported by it.
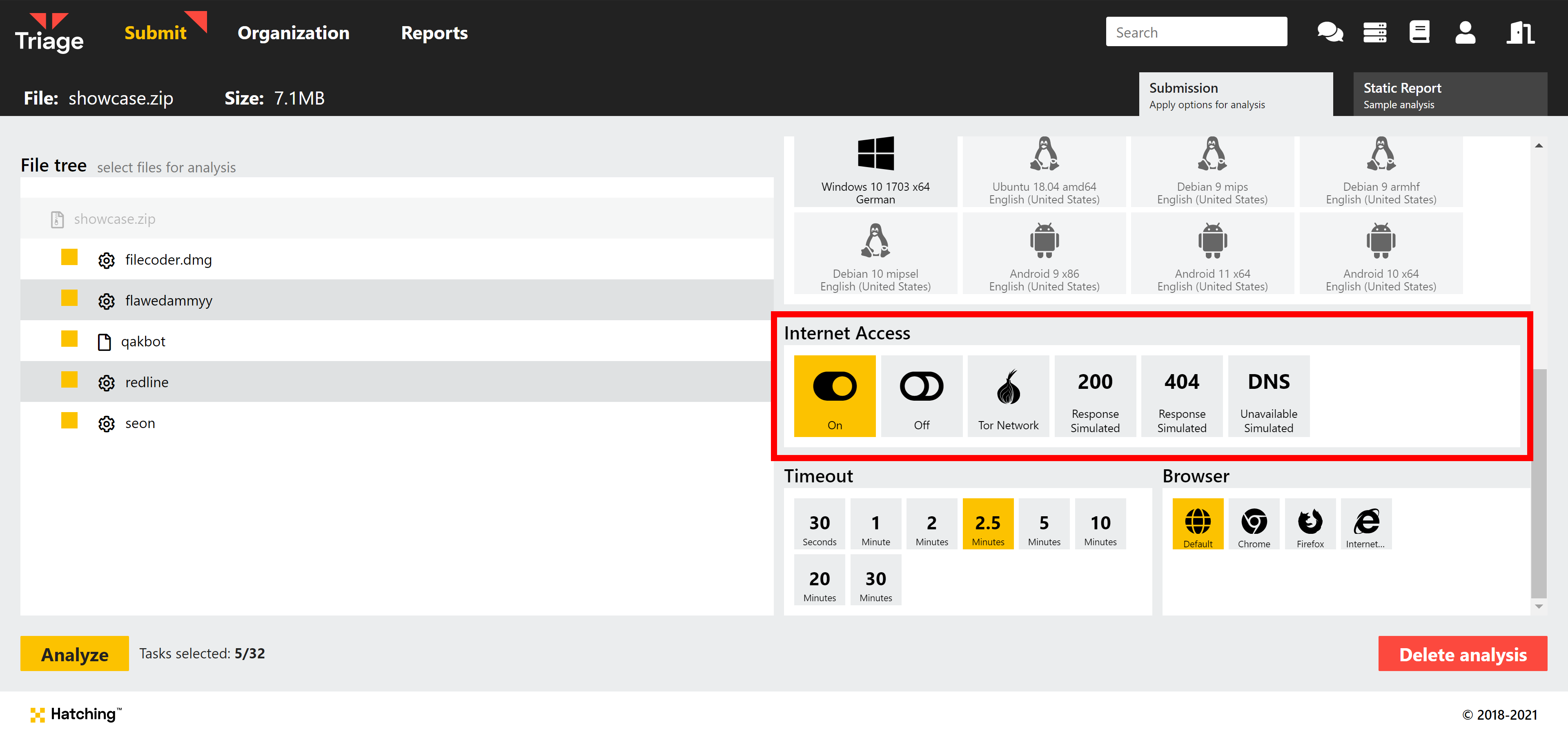
Network simulation is now available for all users on both Private and Public clouds. Just select it from the options during submission or add it to your Profiles.
Read on below for this week’s detection updates.
njRAT Configuration Extractor
First observed all the way back in 2013, njRAT continues to be one of the most widely used remote access trojans in the world. Originally a variant of a family called jRAT or Bladabindi, it is a very full-featured platform with functionality ranging from full remote control to automated actions like keylogging, stealing local passwords for web browsers etc., webcam capture and cryptocurrency wallet theft.
The family also includes a few anti-VM/anti-analysis techniques, including extensive use of packers and the ability to kill processes related to common anti-virus software.
Triage has included support for njRAT for some time, but our coverage of all the different variants and campaigns was somewhat incomplete. We have been carrying out a review of the family, and this week sees the deployment of improved rules and an entirely new configuration extractor.
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| netsh firewall add allowedprogram “C:\ProgramData\Window Update.exe” “Window Update.exe” ENABLE |
| C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\18900b42aac048bd9201b12a3ef8c3b4.exe |
Backdoor-Machine Stealer
Backdoor-Machine is an open-source Python stealer. It was originally listed on Github but was later removed and is now only available through a repository for Python projects specifically. Releases are available here from back in May 2021, but the project has almost certainly been available for longer than that.
The malware is fairly limited in scope, only going after credentials stored by Google Chrome and Brave browsers. It can also steal tokens from the victim’s Discord application. Discord also serves as its C2 infrastructure, with any stolen information being exfiltrated via a webhook to a server controlled by the attacker.
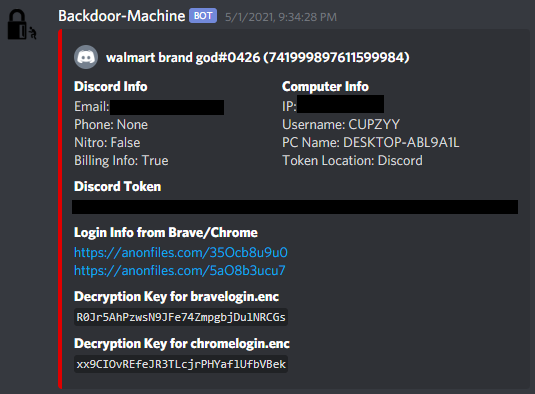
Image of the malware's webhook output taken from the project readme
We have added basic detection for the family to Triage to ensure that it is classified properly.
Analysis:
Indicators of Compromise:
| Indicator |
|---|
| C:\Users\Admin\AppData\Local\Temp\chromelogin.txt |
| C:\Users\Admin\AppData\Local\Temp\chromelogin.enc |
| C:\Users\Admin\AppData\Local\Temp\bravelogin.txt |
| C:\Users\Admin\AppData\Local\Temp\bravelogin.enc |
| C:\Users\Admin\AppData\Local\Temp_MEI18162\brave.py |
| C:\Users\Admin\AppData\Local\Temp_MEI18162\chrome.py |
ElectroRAT
Back in January Intezer published a blogpost about a campaign they’d spotted which they estimated to have originally begun in January 2020. This was a widespread effort using social engineering across multiple websites, social media accounts and fake applications aimed at convincing users in the cryptocurrency community to download and install trojanised software.
At the end of this chain lies ElectroRAT, a cross-platform Golang malware capable of infecting Windows, Linux and macOS systems. It takes its name from the fact that the fake applications it has been seen embedded in are all written using the Electron framework.
The family’s functionality focuses on stealing the private keys and contents of cryptocurrency wallets, but that doesn’t mean it can’t do anything else. It also includes a wide range of other capabilities commonly seen in stealers, such as keylogging, screen capture, downloading and running additional files, or uploading files from the infected machine.
For more information check our Intezer’s full blogpost and the author’s Tweet thread.
Analysis:
Indicators of Compromise:
| Indicator |
|---|
| C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\systemcl.lnk |
| C:\Users\Admin.systemcl.exe |
Mercurial Grabber
Mercurial is yet another “for research purposes only” malware family which is, to noone’s surprise, being used maliciously in the wild. It is available open-source via Github.
The software is written in C# and has a good range of features, including a couple of slightly unusual targets in that it attempts to steal user accounts for Roblox and Minecraft besides the usual web browsers/Discord. To take the feature list directly from the author’s readme:
- Grabs Roblox cookies from Roblox Studio
- Grabs Minecraft sessions
- Grabs Google Chrome passwords
- Grabs Google Chrome cookies
- Grabs Discord token
- Grabs victim machine info
- Grabs Windows product key
- Grabs IP address, geolocation
- Grabs screenshot
- Anti Virtual Machine
- Anti Debug
As with Backdoor-Machine, Discord generally serves as the C2 infrastructure for the family.
We recently had a sample of the family reported to us via feedback and have added some initial static detections to tag it correctly.
Analysis:
Hive Ransomware
Hive is a relatively new ransomware first reported in June 2021. Like most modern ransomware families it also exfiltrates data from infected machines/networks before encrypting files, and then leverages this to encourage ransom payment by threatening to release sensitive information. The operators have their own leak site along the same lines as other larger families, and based on the contents on this they appear to be finding some success in breaching companies.
One of the first companies to be publicly disclosed as suffering a breach was the Altus Group, a company providing commercial real estate software. More recently they have reportedly breached the non-project Memorial Health System in the US, a small network of hospitals and outpatient services in Ohio and West Virginia.
We have reviewed a number of samples available publicly and implemented detections as relevant.
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| C:\Users\Admin\Desktop\fwdM_HOW_TO_DECRYPT.txt |
| C:\YCGOr8OKUvVDOVsbzhPuN7zUcfVjtcHtF3cEzeMa7u4.key.w2tnk |
| C:\Users\Admin\AppData\Local\Temp\bB9B1encv6.bat |
| [*].w2tnk |
Nitro Ransomware
From the same developer as Mercurial Grabber, Nitro Ransomware is a new family first released in April 2021. Once again it is available open-source through Github, and is listed for educational purposes only (although the mention of the prebuilt ransom payment system in the same line of the readme seems to contradict that somewhat…).
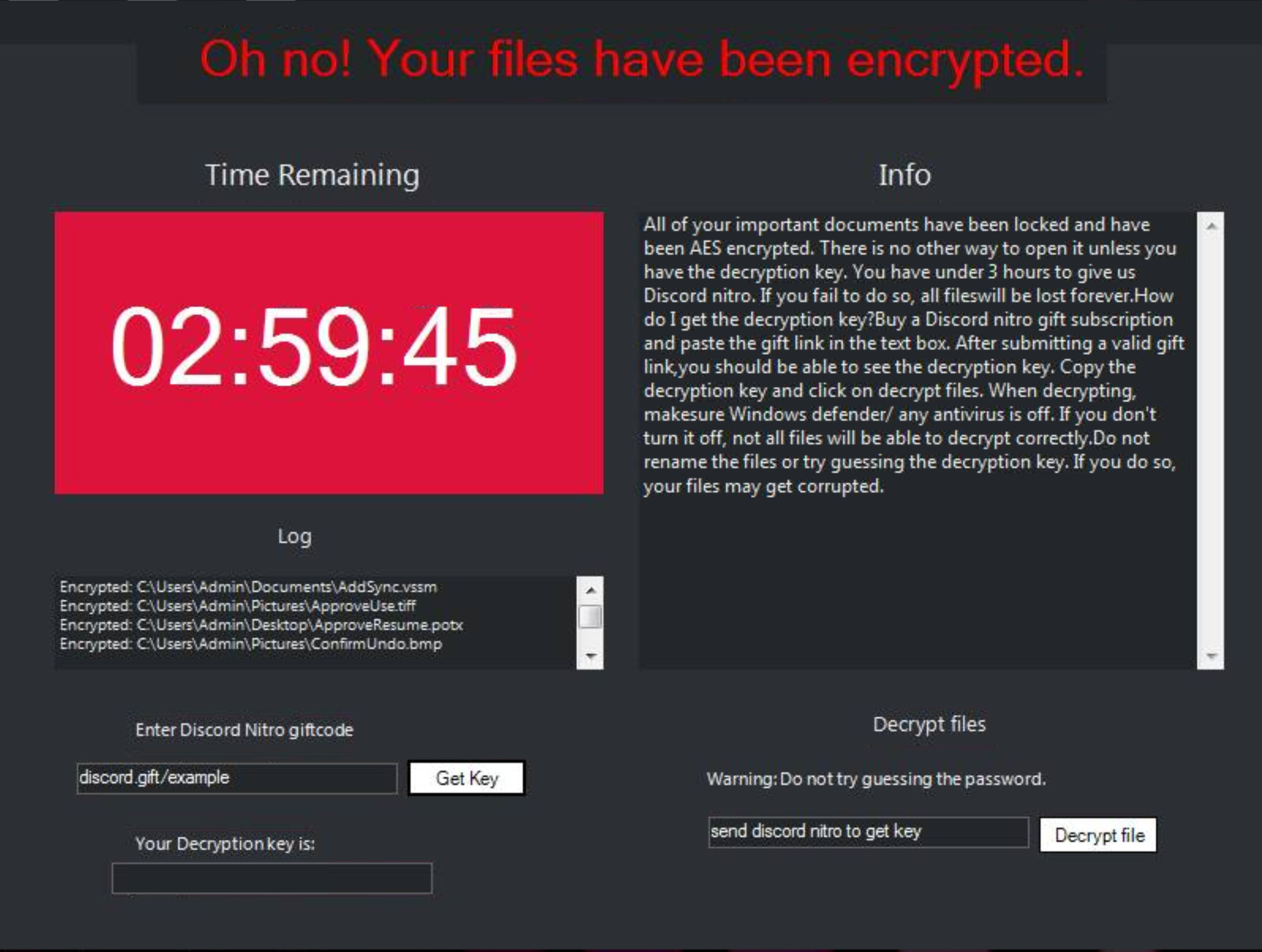
It gets its name from the fact that it is designed to extort payment in the form of Discord Nitro gift codes, although it has been reported that the encryption key is actually included in the executable itself making decryption relatively straight forward without paying the ransom.
As with some of the other families above, C2 communication is carried out through Discord webhooks.
We have reviewed a large number of available sample and implemented detection as relevant.
Analyses:
Indicators of Compromise:
| Indicator |
|---|
| wmic csproduct get uuid |
| C:\Windows\assembly\NativeImages_v4.0.30319_32\NitroRansomware\ |
| [*].givemenitro |
| \REGISTRY\USER[s-id]\Software\Microsoft\Windows\CurrentVersion\Run\NR |
