We’re doing something a little different for this week’s Triage Thursday blogpost. Over recent weeks we have been working on a new set of functionality for Triage to support analysis and rating of phishing URLs which would not normally trigger behavioural detections. Although it is still in early stages, in today’s blogpost we’ll be showing something of a sneak preview of the current state and our goals with the project.
Our Approach to Phishing Analysis
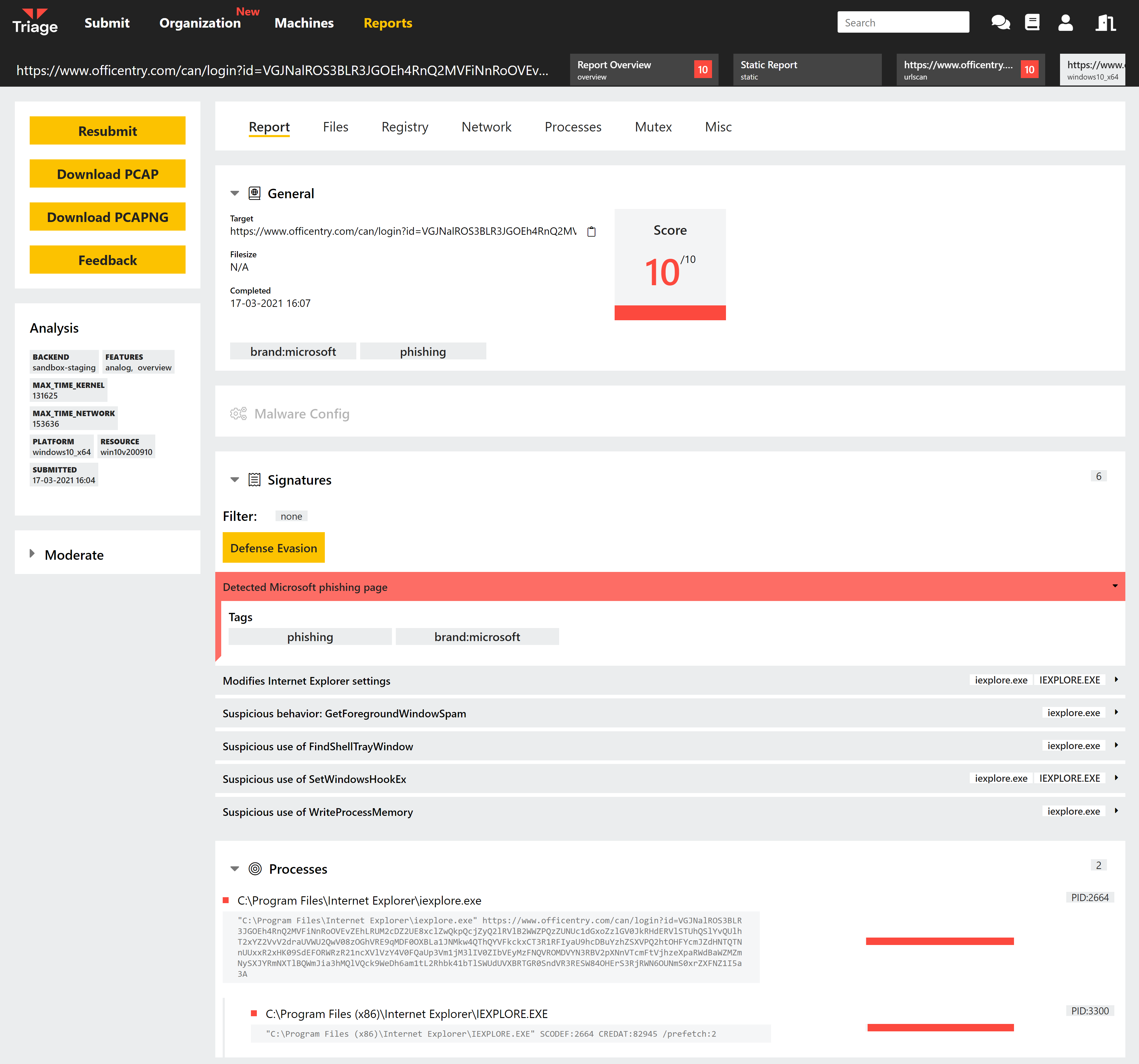
In general processing phishing URLs through a behavioural sandbox returns limited or no results, as there is no interaction between the web page and the local system - for example in the screenshot above the URL would receive a score of 1 under the current signature system. However just because a page isn’t deploying exploits or malware to the VM doesn’t mean that it is of no interest.
To address this we are building a system around static analysis of the webpage that is retrieved during live analysis. The new module assesses multiple aspects of the site accessed, comparing them against known page layouts to identify likely phishing attempts. In its final verdict it also takes into account other aspects of the web server hosting the page to eliminate false positives and separate legitimate websites from those attempting to imitate them.
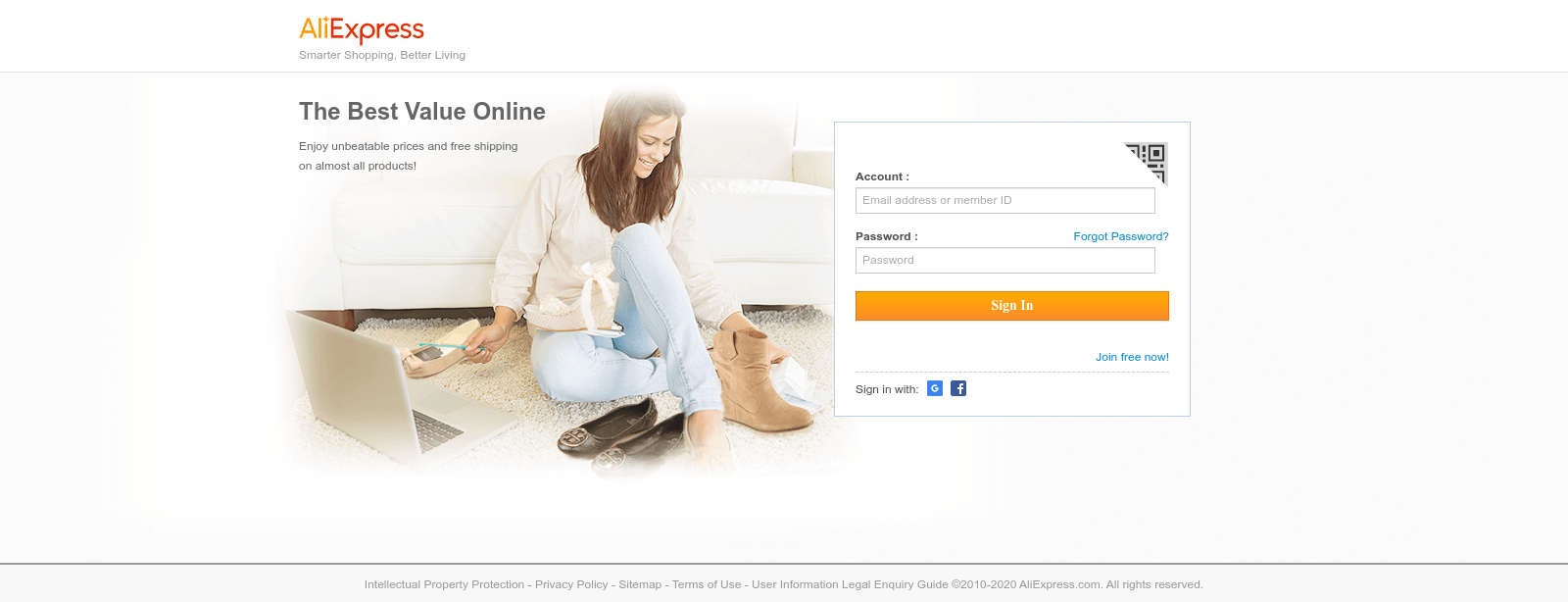
Example phishing page imitating AliExpress account login
Where Are We Currently?
Right now we have the basic groundwork in place to start building out detections and adding details. Our focus so far in development has been to target particular known websites commonly targeted in phishing attempts - such as PayPal, mail carriers and major banks - while we get the system working. We currently have support for a few dozen common brands or organisations and are now expanding that list rapidly.
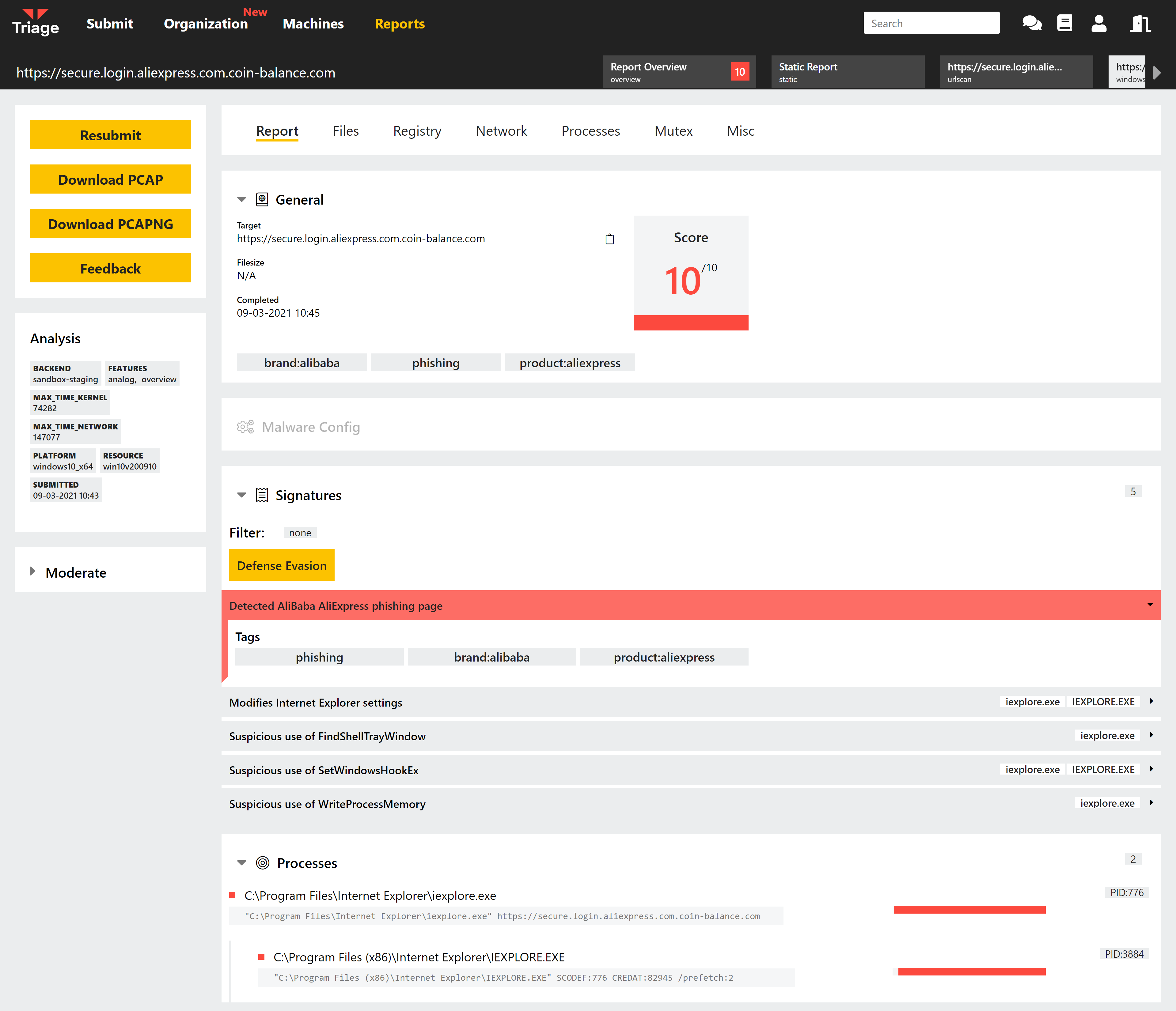
The phishing analysis system fits straight into the existing Triage workflow for URL submissions. You will have access to the VMs during analysis through our Live Monitor, letting you interact with the phishing sites directly in a safe environment. You can also use Profiles to configure which browser will be used to launch the analysis, how long it will run for, and which operating system it uses. URL analysis is already supported by all of our OS options - Windows 7/10, Linux, Android and our upcoming macOS environment - and this is also true of the phishing module.
What’s Next?
With the framework ready we have 2 major objectives:
- Expand the list of currently supported brands/companies commonly imitated for phishing purposes.
- Widen the scope of the detections to include general detections which are not limited to matches against specific known bad values.
With the scale and range of phishing campaigns the second point of the list is of particular interest going forwards. We want to ensure that Triage provides good detection coverage in a landscape that is constantly changing, so it is important that we are not anchored to a set of ’templates’ which need regular updating. We’ll be building out this aspect in the coming weeks and months.
Conclusion
We’ll have more information on phishing support in future blogposts. Note that this is not currently available on Triage public or private cloud servers, as it is still in early development. We’ll let you know when versions are going live through our normal channels here and on Twitter.
If you would like to reach out to us about anything covered here or with general questions and feedback you can find us through the website, on Twitter, or using the Feedback option on an analysis report page.
Not signed up yet? Head over to tria.ge to register for a free account.
